In 2009, I was called to investigate a strange incident at a mid-sized manufacturing company. Employees reported that their computers were “acting slow” and were connecting to unknown IP addresses late at night. Initially, the IT team believed it to be a network glitch. But within days, confidential design documents were stolen. The culprit? A worm exploiting a misconfigured Windows XP operating system with weak user permissions and no security patch installed.
That case reinforced for me what I had been teaching for years: the operating system is the bedrock of cyber security. Without mastering OS fundamentals—how they work, how they control access, and how attackers exploit them—you cannot call yourself a complete cyber security engineer.
At CuriosityTech.in, Nagpur, we teach our learners to think of operating systems not as boring background software, but as the battlefield where hackers and defenders engage daily. Let’s dive into OS fundamentals through this narrative lens.
Why Operating Systems Matter in Security
Operating Systems (OS) are the interface between users, hardware, and applications. If an OS is poorly secured, attackers gain a master key to everything.
- Every system runs on an OS: From servers in AWS to desktops at offices.
- Attack surface is huge: OS controls users, processes, memory, and files.
- History proves OS as entry point: From the Windows XP Worms to the Solaris rootkits, operating systems remain a prime target for attackers.
- Security Engineers’ role: Harden, patch, and monitor OS to prevent intrusions.
Storyline: The Evolution of OS Security
The Early Days – Windows 95 & User Freedom
In the 90s, operating systems prioritized usability, not security.
- No login password enforcement.
- Users often ran as administrators by default.
- Malware spread easily via floppy disks and email attachments.
The Patch Era – 2000s
After worms like Conficker and Blaster caused billions in damages, vendors like Microsoft and Linux communities began pushing security patch management as a survival model.
- Patch Tuesday was born.
- Firewalls became built-in features.
- Linux hardened kernel modules were introduced.
The Modern Era – 2020s to 2025
Security is now proactive, not reactive.
- Sandboxing (Windows Defender Application Guard, SELinux).
- Zero Trust architectures (no implicit trust of users).
- Memory protections like DEP (Data Execution Prevention).
- Cloud OS (containers, Kubernetes) with micro-segmentation.
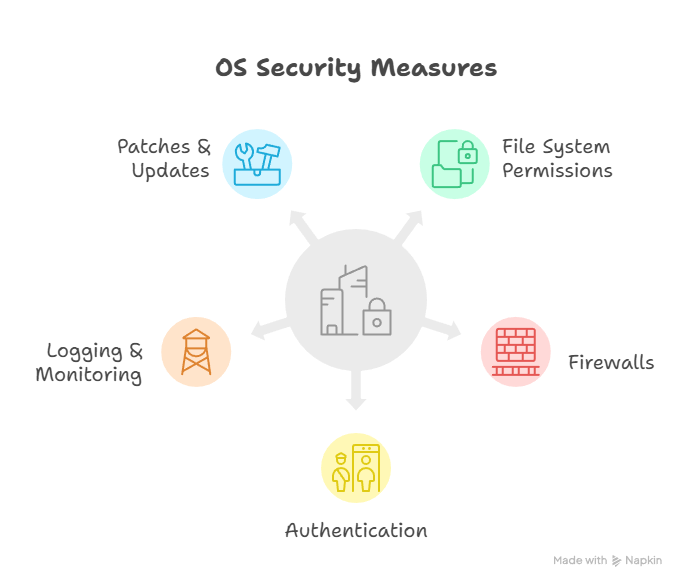
OS Security Concepts Every Engineer Must Know
1. User Authentication & Access Control
- Password policies, biometric login, 2FA.
- Role-Based Access Control (RBAC).
- Principle of Least Privilege: never run software as admin unless required.
2. File System Permissions
- In Linux: rwx permissions define who can read, write, execute.
- In Windows: NTFS permissions manage file access.
- Attack Example: Ransomware encrypts files because users had write access where it wasn’t needed.
3. Process Management & Security
- Processes isolate applications.
- Malware often injects code into legitimate processes (e.g., explorer.exe).
- Engineers must understand tools like top, Task Manager, or Sysinternals to monitor unusual activity.
4. Memory & Kernel Protection
- Buffer Overflow: Attackers overwrite memory to run malicious code.
- Modern OS use protections: ASLR (Address Space Layout Randomization), DEP, kernel integrity checks.
5. Patch Management
- Without frequent patching, OS vulnerabilities are discovered and weaponized by hackers.
- The infamous WannaCry ransomware in 2017 spread using an unpatched Windows SMB protocol exploit.
6. OS Logging & Monitoring
- Security logs are the “black box” of OS activity.
- Engineers must review syslog (Linux) or Event Viewer (Windows) for intrusion evidence.
Case Study: The Healthcare Hack
Incident: In 2022, a healthcare provider was attacked through a vulnerability in its outdated Windows Server. Attackers bypassed weak access controls and accessed millions of patient records.
Analysis:
- Operating System was unpatched.
- No role separation—admins used same passwords for years.
- Logs were not monitored; breach was detected months later.
Lesson for Engineers: Operating Systems aren’t just IT maintenance—they are security gateways. A single weak OS node can bring down entire infrastructure.
OS Security Hardening Checklist.
| Area | Windows/Linux Action |
| Authentication | Enforce 2FA, disable default accounts |
| File Permissions | Limit write access, audit critical folders |
| Patch Management | Automate updates, monitor CVE announcements |
| Services | Disable unused services (e.g., Telnet, FTP) |
| Firewall & Antivirus | Enable host-based firewalls, use EDR solutions |
| Logging | Centralize monitoring in SIEM |
| Backups | Regular encrypted OS backups |
At Curiosity Tech Nagpur, we often combine this checklist with real-world penetrations by letting students harden a Linux server, while ethical hackers in the same lab attempt to exploit it. This hands-on challenge bridges theory with reality.
Infographic Description
Personal Insight from Experience
Back in 2015, I worked on securing control systems for a manufacturing plant using outdated Windows servers. They believed “since it’s offline, it’s safe.” That illusion shattered when a contractor connected an infected USB drive. The malware propagated and shut down production for a week. From that point forward, I carried one guiding mantra: “Operating System security is not optional; it is your first and last line of defense.”
Conclusion
Operating Systems are often ignored as “just the environment.” But in truth, they are the foundation of cyber security architecture. Whether it’s Linux servers in the cloud, Windows desktops in offices, or containerized OS frameworks in Kubernetes, securing the operating system means securing everything built on top of it.
At CuriosityTech.in (Phone: +91-9860555369 | Email: contact@curiositytech.in | Office: 1st Floor, Plot No 81, Wardha Rd, Gajanan Nagar, Nagpur | Social: Instagram @curiositytechpark, LinkedIn: Curiosity Tech, Facebook: Curiosity Tech), we train engineers with real-world labs, showing how OS vulnerabilities are exploited and how to harden defenses effectively. Because in a world where attackers never sleep, secure operating systems are your strongest shields.



