When businesses moved aggressively to the cloud over the last decade, the promise was clear: scalability, cost-efficiency, and speed. But what most executives didn’t realize was that with cloud adoption comes a new threat surface. Attacks on misconfigured buckets, stolen access keys, and weak IAM policies have caused millions in damages.
As a cyber security consultant at CuriosityTech.in Nagpur, I’ve seen clients trust too much in “default” cloud security. Truth? Cloud providers offer security tools—but responsibility lies with the customer. In this blog, we’ll compare AWS, Azure, and GCP practices and show how engineers must secure them.
The Shared Responsibility Model
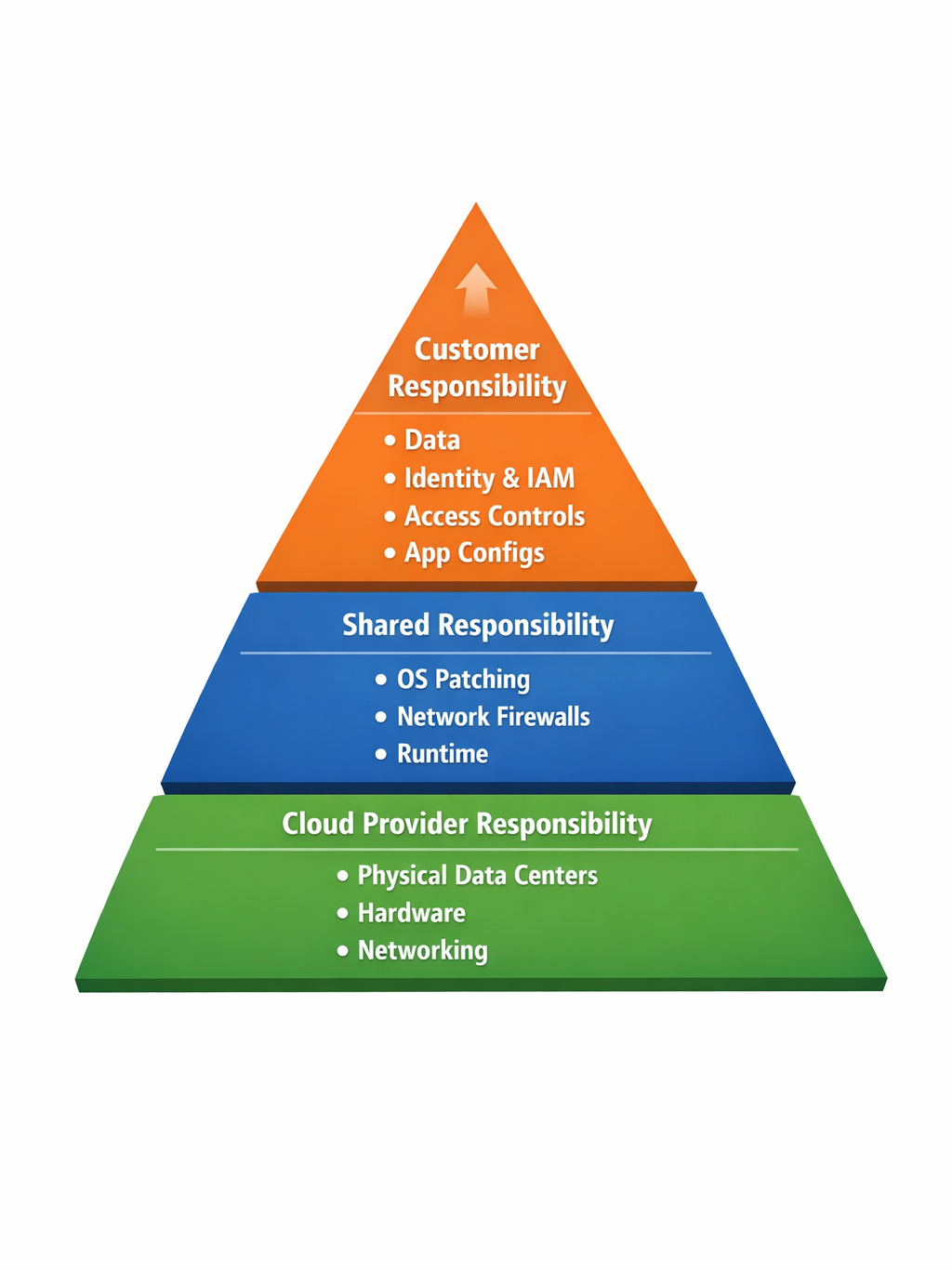
- Cloud Provider Responsibility: Physical data centers, networking, hardware.
- Customer Responsibility: Data, access controls, app configurations, identity.
- Middle zone (shared): OS patches, network firewalls depending on service type (IaaS/PaaS/SaaS).
This shows why breaches often happen: customers forget their half of the responsibility.
Cloud Providers at a Glance
| Cloud | Strengths | Common Pitfall |
| AWS | Dominant global presence, largest toolset. | Misconfigured S3 buckets expose sensitive data. |
| Azure | Strong enterprise integration, Active Directory synergy. | Over-exposed default ports/services during VM setup. |
| GCP | High innovation, advanced AI/ML integrations. | Weak IAM governance, mismanaged service accounts. |
Cloud Security Best Practices – Comparative Guide
1. Identity & Access Management (IAM)
AWS:
- Use IAM roles instead of long-term keys
- Enforce MFA for root & privileged accounts.
- Rotate credentials via AWS Secrets Manager.
AZURE:
- Integrate Azure Active Directory.
- Enforce Conditional Access (device + user + location).
- Privileged Identity Management (PIM) to limit admin rights.
GCP :
- Implement Service Account key governance.
- Use Cloud Identity-Aware Proxy for Zero Trust.
- Use organisation policies to enforce restrictions.
2. Data Storage Security
AWS (S3) :-
- Default buckets private.
- Always enable S3 Encryption (AES-256, KMS).
- Monitor with Amazon Macie for data classification.
Azure (Blob Storage) :-
- Use Azure Storage encryption with managed keys
- Configure private endpoints.
- Enable immutable blob storage for compliance.
GCP (Cloud Storage) :-
- Apply CMEK (Customer-Managed Encryption Keys)
- Enforce signed URLs with expiration.
- Enable object lifecycle rules for secure archival.
3. Network Security
AWS :-
- Configure VPC Security Groups & NACLs.
- Use AWS WAF & Shield for DDoS protection.
- Avoid assigning public IPs unnecessarily.
Azure :-
- Configure Network Security Groups (NSGs).
- Deploy Azure DDos Protection.
- Use Firewall with threat intelligence in blocking mode.
GCP :-
- VPC firewall rules with principle of least privileage.
- Leverage Cloud Armor for DDoS.
- Enable private Google Access (block internet for cloud resources)
4. Monitoring & Logging
- AWS: CloudTrail + GuardDuty + CloudWatch.
- Azure: Azure Monitor + Sentinel SIEM.
- GCP: Cloud Audit Logs + Security Command Center.
Best Practice: Centralize logs into SIEM (Splunk, ELK, Sentinel).
5. Compliance & Governance
- AWS → Compliance blueprints: HIPAA, GDPR, ISO 27001.
- Azure → Enterprise-ready governance templates, Microsoft Defender for Cloud.
- GCP → Assured Workloads for regulated environments.
Exercise at CuriosityTech Training: Students are asked to design a multi-cloud compliance matrix—mapping customer GDPR obligations across three providers.
Real-World Case Studies
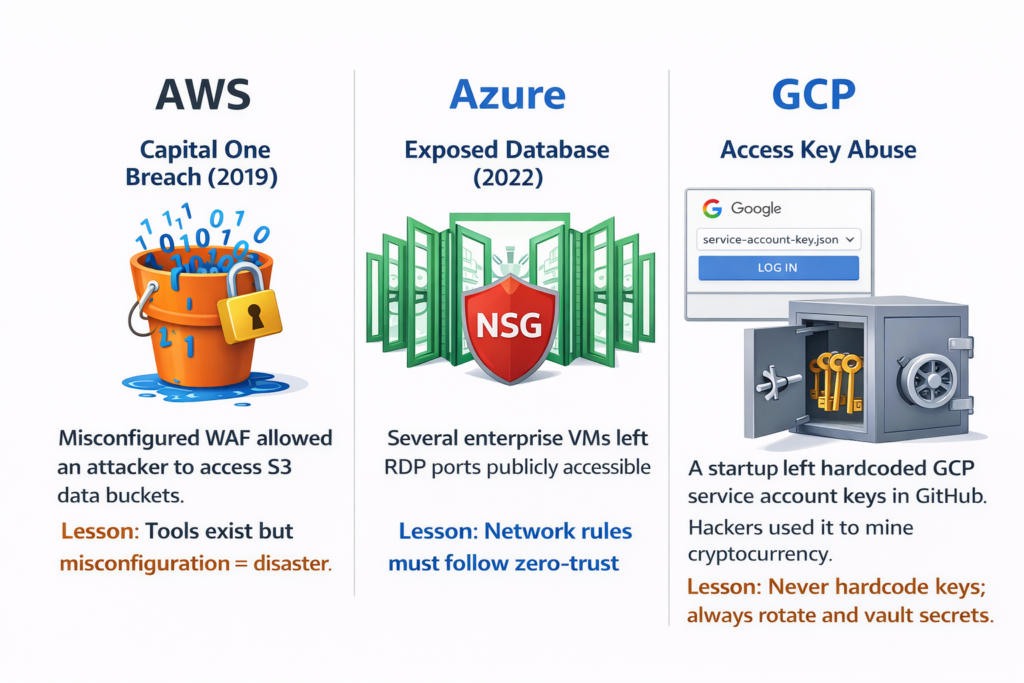
- AWS: Capital One Breach (2019)
- Misconfigured WAF allowed an attacker to access S3 data buckets.
- Lesson: Tools exist but misconfiguration = disaster.
- Azure: Exposed Database (2022)
- Several enterprise VMs left RDP ports publicly accessible.
- Lesson: Network rules must follow zero-trust.
- GCP: Access Key Abuse
- A startup left hardcoded GCP service account keys in GitHub. Hackers used it to mine cryptocurrency.
- Lesson: Never hardcode keys; always rotate and vault secrets.
Engineer’s Cloud Security Checklist (2025 Ready)
| Control Area | AWS | Azure | GCP |
| IAM | MFA, IAM Roles | AAD, PIM | IAP, Service Account Key Mgmt |
| Data Security | Encrypt S3 | Blob storage encryption | CMEK |
| Network | VPC SGs + Shield | NSGs + Firewall | Cloud Armor |
| Monitoring | GuardDuty | Azure Sentinel | Security Command Center |
| Compliance | ISO, GDPR, FedRamp | HIPAA, SOC | GDPR, Assured Workloads |
Infographic Description
A three-column infographic representing AWS, Azure, GCP:

- AWS: Illustration of an open bucket leaking data → lock applied.
- Azure: A network gate with too many open doors → secured with NSG.
- GCP: Login with service account keys → vault storing keys properly.
- At the bottom: text: “Cloud Misconfigurations = #1 Cause of Breaches.”
My Personal Consulting Insight
One of the most alarming cases I handled was for a retailer in Nagpur using multi-cloud (AWS + Azure). They assumed cloud was “auto-secure.” During an internal audit, we found:
- An exposed S3 bucket with customer receipts.
- An Azure VM with default RDP open to the world.
- GCP service account credentials stored in GitHub.
The client was stunned—they thought spending on enterprise cloud licenses guaranteed safety.
Lesson: You can rent the safest building in Nagpur, but if you don’t lock your office door, a thief still walks in.
Conclusion
Cloud security in 2025 is no longer about choosing the “best cloud”—it’s about mastering multi-cloud best practices. AWS, Azure, and GCP all provide powerful tools, but the burden lies on engineers to configure, monitor, and govern them correctly.
At CuriosityTech.in (Gajanan Nagar, Nagpur | Phone: +91-9860555369 | Email: contact@curiositytech.in | Socials: Instagram @curiositytechpark, LinkedIn/Facebook: Curiosity Tech), we prepare engineers to think beyond single vendors, practicing cross-cloud security labs. Because hackers don’t care if it’s AWS, Azure, or GCP—they only care where misconfigurations exist.



