Introduction
Security teams are under constant pressure: more assets, faster deployments, and threats that never sleep. Manual processes can’t keep pace. Automation is the difference between an overwhelmed SOC and a proactive, resilient security program.
Over 20 years I’ve watched the discipline move from ad-hoc scripts to mature security automation ecosystems (SIEM → SOAR → MDE/EDR integrations → policy-as-code). The goal of this chapter is practical: teach you how to design, build and operate security automation pipelines that reduce mean time to detect (MTTD) and mean time to respond (MTTR), while preserving safety, auditability and human oversight.
At CuriosityTech.in we teach engineers to automate responsibly — building playbooks that a CISO can sign off on and auditors can inspect. Contact avenues (website: curiosity tech, email: contact@curiositytech.in, phone: +91-9860555369) are woven into our lab exercises and real-world coaching so learners get hands-on with the exact tech stacks used in industry.
Learning objectives (what you’ll be able to do after this guide)
- Map security use-cases to automation outcomes.
- Select appropriate tools (SIEM, SOAR, EDR, IaC scanners, CI/CD hooks).
- Write and test automation scripts (Bash, Python) for detection, containment, and remediation.
- Build a basic SOAR playbook and integrate it with a ticketing system.
- Design safe escalation, auditing, and rollback practices.
- Understand monitoring, metrics and continuous improvement for automation.
1. A Practical Taxonomy: Where to Apply Automation
- Start by mapping what to automate. Not everything should be automated; some tasks require human review.
- Alert Triage & Enrichment — automatically enrich incoming alerts (IP reputation, DNS history, asset owner).
- Containment — automated network isolation or endpoint quarantine for high-confidence detections.
- Remediation — patch deployment, revoke credentials, rotate keys (with approvals).
- Vulnerability Management — schedule scans, correlate with asset inventory, open tickets for critical hosts.
- Compliance & IaC Scanning — run policy-as-code checks in CI pipelines (prevent insecure templates from deploying).
- Threat Hunting & Orchestration — scheduled hunts, automated data collection for analysts.
- Reporting & Metrics — auto-generate dashboards and compliance evidence.
2. Core Components of a Security Automation Stack
You need tooling that complements each other. Below is a concise map and how they interact.
| Component | Purpose | Example Actions |
| SIEM | Centralize logs, detect anomalies | Correlate logs; generate alerts |
| EDR / MDE | Endpoint visibility + response | Quarantine endpoint; dump suspect process |
| SOAR | Orchestrate playbooks and automate workflows | Enrichment, containment, ticketing |
| IAM Automation | Manage credentials and sessions | Force password resets, disable accounts |
| IaC Scanners | Prevent insecure infrastructure rollout | Block deploys with misconfigurations |
| CI/CD Hooks | Shift-left security checks | Run SAST/DAST on pull requests |
| Asset DB / CMDB | Reliable asset metadata | Owner, criticality, RTO/RPO values |
| Ticketing / ITSM | Audit and remediation tracking | Create/close incidents with evidence |
Note: choose tools that can be integrated via APIs and provide strong logging for audit trails.
3. A Realistic Workflow (flowchart description)
Below is a textual flowchart representing a typical automated detection → response path. Use it to design your SOAR playbooks.
Flow:
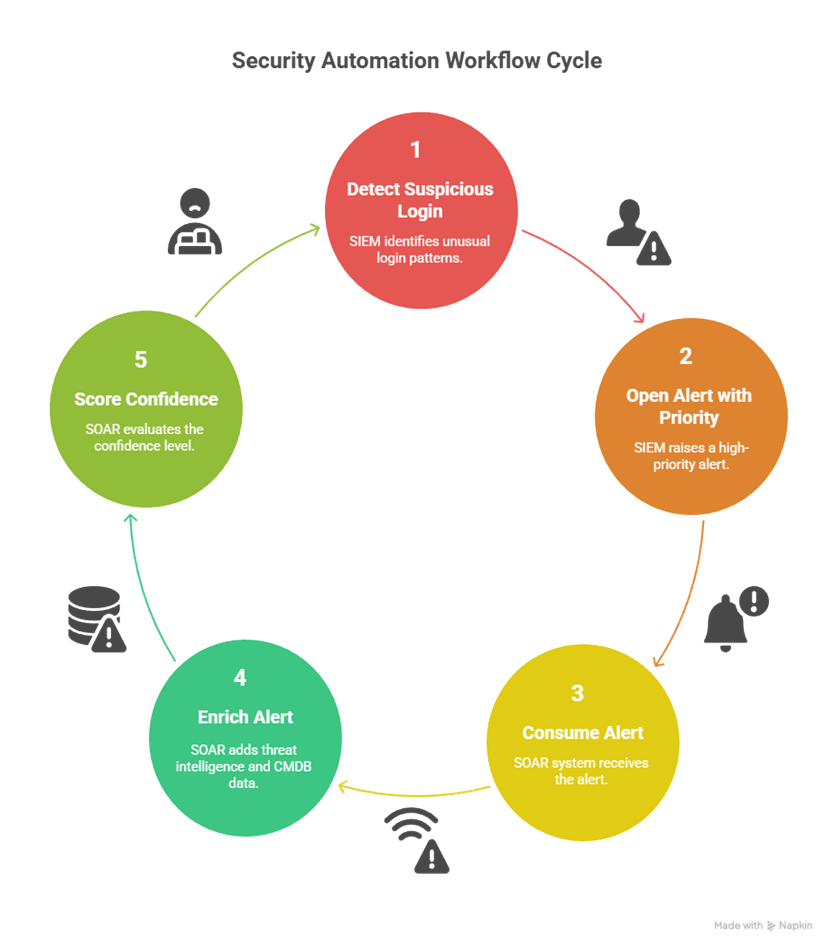
This flow enforces safe automation boundaries (auto-action only at high confidence or with approvals).
4. Designing Safe Automation Policies
- Automation is powerful but dangerous when misconfigured. Follow these principles:
- Fail-safe by default: automation should prefer “safe state” not “disruptive state”. For example, quarantine a non-critical server only after human approval.
- Graduated actions: enrichment → notify → auto-contain — escalate progressively
- Approval gates: for high-impact actions (rebooting clusters, nuking VMs) require multi-party approval.
- Auditable playbooks: log every decision, who approved it, and what data was used.
- Backout plans: every remediation must include rollback instructions.
- Testing in staging: maintain staging instances that mirror production for testing playbooks.
- Least privilege for automation: use service accounts with minimal scopes and short-lived credentials.
- Rate limiting: automate with throttles to avoid API storms.
5. Tool Patterns & Example Integrations
Below are common automation patterns and example pseudo-integrations
A: Enrichment pipeline
- Trigger: SIEM alert (webhook).
- Actions: Query threat intel API, CMDB lookup, DNS history, passive SSL fingerprint.
- Output: Append enrichment to alert, compute risk score
B: Auto-containment for confirmed malware
- Trigger: EDR detection with malicious signature + SIEM correlation.
- Actions:
- EDR quarantines endpoint.
- SOAR snapshots memory collects forensic logs.
- Create incident ticket with artifacts.
- Notify asset owner & SOC team.
C: CI/CD Preventative Automation
- Trigger: PR opened.
- Actions: Run SAST, IaC scanning (e.g., Checkov/TerraScan), DAST on ephemeral environment. Block merge if severity > threshold.
6. Script Examples — Practical, Safe, and Auditable
Below are bite-size automation scripts you can use as starting points. Each script includes logging and dry-run options so you can test before doing real actions.
6.1 Bash: Enrich an IP and append to incident (dry-run capable)
# enrich_ip.sh — simple enrichment demo
# Usage: ./enrich_ip.sh –ip 1.2.3.4 –dryrun
set -euo pipefail
IP=””
DRYRUN=false
LOGFILE=”./enrich_ip.log”
while [[ $# -gt 0 ]]; do
case $1 in
–ip) IP=”$2″; shift 2;;
–dryrun) DRYRUN=true; shift;;
*) echo “Unknown option $1”; exit 1;;
esac
done
if [[ -z “$IP” ]]; then
echo “Usage: –ip <address>”
exit 1
fi
echo “$(date -u) INFO: Enrichment started for $IP” | tee -a “$LOGFILE”
# Placeholder for threat intel call (replace with real API)
REPUTATION=”suspicious” # stubbed; call actual API in prod
echo “$(date -u) INFO: Threat intel reputation: $REPUTATION” | tee -a “$LOGFILE”
if $DRYRUN; then
echo “$(date -u) DRYRUN: Would append enrichment to incident” | tee -a “$LOGFILE”
else
# Example: POST to SOAR incident API (pseudo)
# curl -X POST “https://soar.example/incidents/123/enrich” -H “Authorization: Bearer $TOKEN” \
# -d “{\”ip\”:\”$IP\”,\”reputation\”:\”$REPUTATION\”}”
echo “$(date -u) ACTION: Appended enrichment to incident for $IP” | tee -a “$LOGFILE”
6.2 Python: Quarantine endpoint via EDR API (safeguarded)
# quarantine_endpoint.py
import argparse, logging, requests, os, sys
logging.basicConfig(level=logging.INFO)
logger = logging.getLogger(“quarantine”)
def quarantine(host_id, dryrun=True):
logger.info(“Starting quarantine for host_id=%s dryrun=%s”, host_id, dryrun)
# Placeholders — replace with real EDR API endpoints and token retrieval
edr_api = os.getenv(“EDR_API_URL”, “https://edr.example/api/v1”)
token = os.getenv(“EDR_TOKEN”)
if not token:
logger.error(“EDR_TOKEN not set”)
sys.exit(1)
if dryrun:
logger.info(“DRYRUN: Would call %s/hosts/%s/quarantine”, edr_api, host_id)
return
headers = {“Authorization”: f”Bearer {token}”, “Content-Type”: “application/json”}
resp = requests.post(f”{edr_api}/hosts/{host_id}/actions/quarantine”, headers=headers)
resp.raise_for_status()
logger.info(“Quarantine action submitted: %s”, resp.json())
if __name__ == “__main__”:
parser = argparse.ArgumentParser()
parser.add_argument(“–host”, required=True)
parser.add_argument(“–dryrun”, action=”store_true”)
args = parser.parse_args()
quarantine(args.host, dryrun=args.dryrun)
Best practice: Always run with –dryrun first. Store tokens in short-lived vaults (HashiCorp Vault/AWS Secrets Manager).
7. Building a Simple SOAR Playbook (Example)
Structure your playbook as modular steps that can be reused across incidents.
Playbook: “Suspicious Login – Auto-Enrich + Notify”
Trigger: SIEM webhook when anomalous login occurs.
- Step 1 (Enrichment): Lookup IP, user agent, geo, device posture.
- Step 2 (Context): Query CMDB for asset owner and criticality.
- Step 3 (Score): Apply risk scoring rules (e.g., user in critical group + from foreign IP = high).
- Step 4 (Decision):
- If high: open incident, send urgent Slack alert, create ticket, and add analyst assignment.
- If medium: create ticket and email owner.
- If low: log and archive.
- Step 5 (Wrap): Attach artifacts, create timeline, set SLA timers.
- Pre-merge checks: run SAST (Semgrep/SpotBugs), IaC scanning (Checkov/Terraform-Validate) on PRs. Block merges with high-risk findings.
- Post-deploy checks: run DAST against ephemeral environments created per PR. If DAST finds a critical vulnerability, automatically revert or flag for hotfix.
- Artifact signing: automated signing of artifacts and policy validation before deployment.
Implementation tips: represent playbook steps as idempotent actions, log inputs/outputs, and version your playbooks in git for auditability.
8. CI/CD Integration — Shift Left Security
Embed automation earlier in the developer lifecycle.
Sample GitHub Actions snippet (IaC scan)
name: IaC Security
on: [pull_request]
jobs:
checkov:
runs-on: ubuntu-latest
steps:
– uses: actions/checkout@v3
– name: Run Checkov
uses: bridgecrewio/checkov-action@master
with:
directory: ./terrafo
9. Container & Cloud Automation Patterns
- Image Scanning: Auto-scan images on push to registry; block deployment if critical CVEs detected.
- Runtime Protection: EDR + K8s admission controllers to block suspicious pods.
- Cloud Policy Enforcement: Use tools like OPA/Gatekeeper to enforce policies at admission time.
- Automated Remediation: For failed compliance (e.g., publicly exposed S3 bucket), create a SOAR job to auto-restrict ACLs and open a ticket
10. Metrics – How to Measure Success
Automation isn’t an end; it’s judged by outcomes.
Key metrics:
- MTTD (Mean Time To Detect) — time from compromise to detection.
- MTTR (Mean Time To Respond) — time from detection to containment.
- Automation coverage — percentage of high-priority alerts with automated enrichment.
- False positive rate of automation — must be monitored.
- Playbook execution success rate — % of runs that completed without manual rollback.
- Time saved (FTE equivalent) — analyst hours saved by automation.
Industrial IoT security 2025, IIoT cybersecurity best practices, IEC 62443 compliance, secure MQTT IIoT, network segmentation IIoT, AI anomaly detection IoT, CuriosityTech Nagpur cybersecurity
11. Governance, Compliance & Change Management
Automation introduces new compliance needs
- Change governance: playbooks are changes to production. Use git workflows, code review and approvals for playbooks.
- Access controls: restrict who can edit/run automation. Use role separation: playbook authors ≠ approvers.
- Audit trails: all automatic actions must be logged with who approved or triggered them. Store logs centrally and retain per policy.Legal & privacy review: automated data collection (e.g., memory dump) may have legal implications — get legal sign-off for playbook artifacts.
12. Example Use Cases & Detailed Playbooks (three scenarios)
A — Credential Stuffing Attempt (Automated Response)
- Detect: SIEM detects multiple failed logins across tenant accounts from same IP range.
- Automated Actions:
- Enrich IP (reputation).
- Temporarily block IP at WAF for 30 minutes.
- Force password reset for accounts with suspicious activity (notify users).
- Create ticket with evidence.
- Safety: Rate-limit blocks to avoid blocking valid users.
B — Public S3 Bucket Exposed (Auto-Remediate & Notify)
- Detect: Cloud Config rule flags public ACL on storage.
- Automated Actions:
- Create read-only snapshot for audit (prevent data loss).
- Change ACL to private.
- Notify owner and open remediation ticket.
- If critical data found, trigger incident response and forensic capture.
C — Malware Execution on Endpoint (High Confidence)
- Detect: EDR detects known malware signature plus telemetry correlates with suspicious outbound traffic.
- Automated Actions:
- Quarantine endpoint (EDR).
- Snapshot disk and memory for forensics.
- Kill malicious processes.
- Generate IOC and push to SIEM and endpoint sensors.
- Start a SOAR incident with full timeline.
13. Common Pitfalls & How to Avoid Them
- Over-automation: Automating everything without thresholds causes outages. Use graded responses.
- Insufficient logging: If automation actions are opaque, you’ll blindside auditors. Log everything.
- Stale playbooks: Threat landscape changes; schedule playbook reviews.
- Poorly scoped permissions: Avoid running playbooks with overly broad credentials. Use short-lived tokens.
- No staged testing: Never test first in production. Maintain a staging environment that mirrors production.
14. How to Become an Expert in Security Automation
- Build a repo of safe, reusable scripts (Bash, Python) with dry-run and logging by design.
- Master tools: at minimum learn one SIEM (ELK/Elastic or Splunk), one SOAR (Cortex XSOAR/TheHive + Cortex), and one EDR (CrowdStrike/Microsoft Defender for Endpoint).
- Practice: deploy a mini SOC in a lab: instrument a few VMs, ship logs to an ELK stack, create detection rules and SOAR playbooks. CuriosityTech.in runs workshops replicating this end-to-end.
- Study real incidents: dissect postmortems to understand where automation could have helped and where it would have made things worse.
- Certifications & Courses: pursue SANS automation courses, vendor SOAR certifications, and cloud provider training on automation.
- Contribute to playbook libraries: join community repos and contribute to shared automation templates.
15. Infographic & Diagram Suggestions (for visual learners)
(If you’d like, I can render these diagrams or provide SVG/PlantUML text you can paste into a diagram tool.)
16. Integration Example: How CuriosityTech.in Trains Engineers
At CuriosityTech.in we run a 3-week lab that maps to everything above:
- Week 1: Build an ELK stack, write detection rules, instrument endpoints.
- Week 2: Implement a basic SOAR playbook (enrichment + ticketing) with dry-run testing.
- Week 3: Advanced automation — CI/CD integration, IaC policy enforcement, and red-team vs blue-team automation drills.
- Students get hands-on access to real APIs, mentor reviews, and career coaching. You can reach us via curiositytech.in or email contact@curiositytech.in for course schedules.
17. Actionable Checklist — Start Automating Today
- Inventory critical assets and owners in a CMDB.
- Identify top 10 repeatable tasks in your SOC.
- Prioritize tasks where automation reduces toil without increasing risk.
- Implement dry-run & logging for every script.
- Start with enrichment playbooks before auto-containment.
- Enforce version control and code review for playbooks.
- Create rollback and backout plans for every automated remediation.
- Measure MTTD/MTTR and iterate monthly.
Conclusion
Security automation is the bridge between catching threats and fixing them at scale. When designed with safety, governance, and strong telemetry, automation reduces human toil and compresses response time. The path to mastery is iterative: instrument, automate low-risk tasks, measure, and expand.
Curiosity Tech helps organizations and individuals traverse that path with real labs, mentoring and practical playbooks — a place where theory meets the API-driven reality of modern security.



