Introduction
In the ever-evolving landscape of mobile development, handling permissions and security is paramount to building reliable, safe, and trustworthy cross-platform apps. Developers must safeguard user data while ensuring seamless experiences across Android and iOS, especially as privacy regulations and OS policies become increasingly stringent.
Curiositytech.in, based in Nagpur, champions secure mobile development with robust, end-to-end solutions, addressing both beginners and experienced developers at every step. Learn how to protect data and privacy and prevent vulnerabilities, leveraging resources and personalized guidance from Curiosity Tech’s expert mobile security team at 1st Floor, Plot No 81, Wardha Rd, Gajanan Nagar, Nagpur.
Main Content
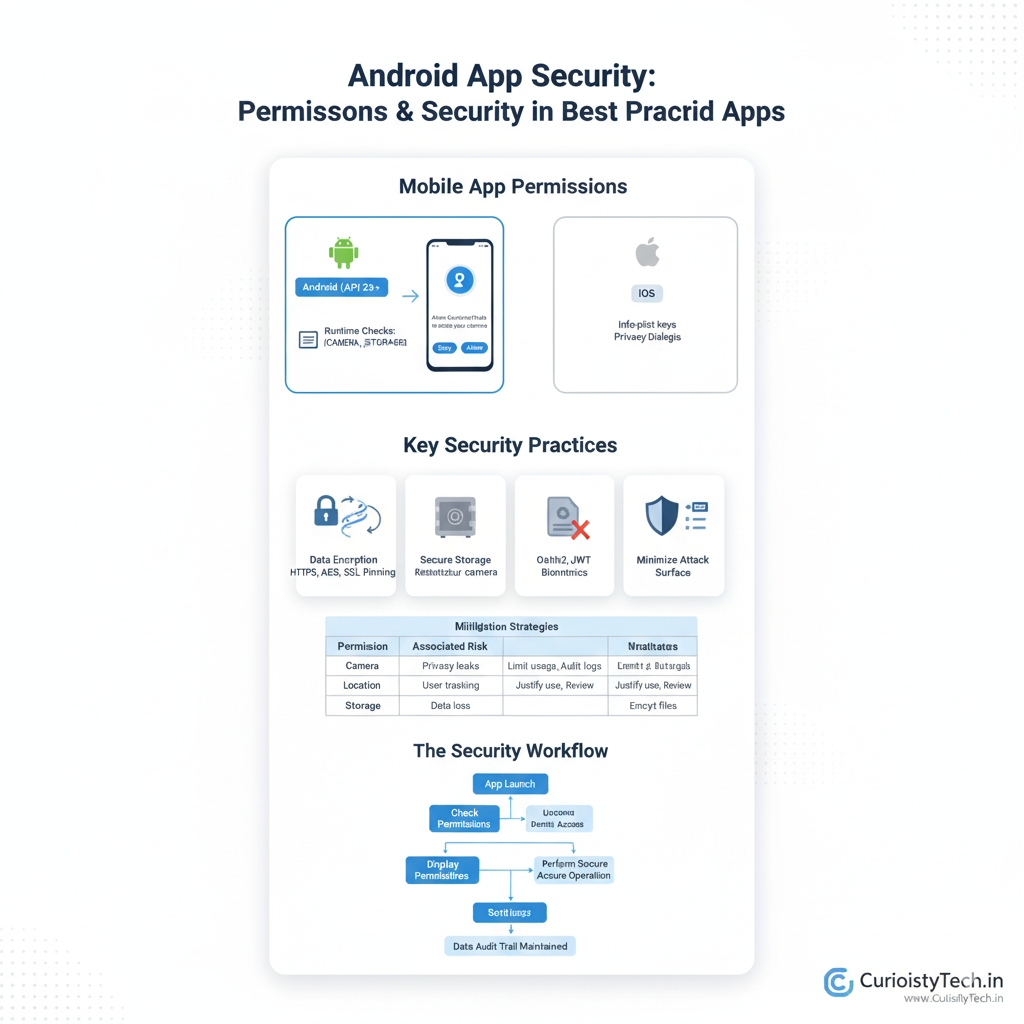
Deep Dive into Mobile App Permissions
Permission paradigms differ across platforms. Android and iOS both require explicit user consent for sensitive operations, like camera, storage, contacts, and location. Permissions are requested at runtime and must be handled gracefully:
- Android (API 23+): Runtime permission model using ContextCompat.checkSelfPermission and requestPermissions methods.
- iOS: Uses Info.plist keys with system dialogs, such as NSCameraUsageDescription for camera access.
Example: Requesting Camera Permission (Android, Kotlin)
kotlin
if (ContextCompat.checkSelfPermission(this, Manifest.permission.CAMERA) != PackageManager.PERMISSION_GRANTED) {
ActivityCompat.requestPermissions(this, arrayOf(Manifest.permission.CAMERA), CAMERA_REQUEST_CODE)
}
Discuss why direct permission prompts should be avoided—preface with in-context explanations to build user trust.
Security Practices in Cross-Platform Development
Security isn’t just about permissions—it’s about data protection throughout the app’s lifecycle.
- Data Encryption: Protect communication with HTTPS, SSL pinning, and end-to-end encryption (e.g., AES for local data).
- Storage Safety: Avoid writing sensitive data to insecure storage (e.g., external SD card or unencrypted databases).
- Authentication: Use OAuth2, JWT, or Firebase Auth for robust user identification. Integrate biometric authentication for added security.
- Minimizing Attack Surface: Remove unused permissions; never request more than needed.
- Code Obfuscation: Use ProGuard or R8 to make reverse engineering harder.
- Regular Security Audits: Schedule code reviews and vulnerability scans.
Table: Common Permissions & Security Risks
| Permission | Associated Risk | Mitigation Strategies |
| Camera/Photos | Privacy leaks | Explain logic, limit usage, audit logs |
| Contacts | Data theft | Hash/sanitize data, minimal access |
| Location | User tracking | Justify use, frequent permission review |
| Storage | Data manipulation/loss | Encrypt files, restrict access |
Hierarchical Diagram: The Security Workflow
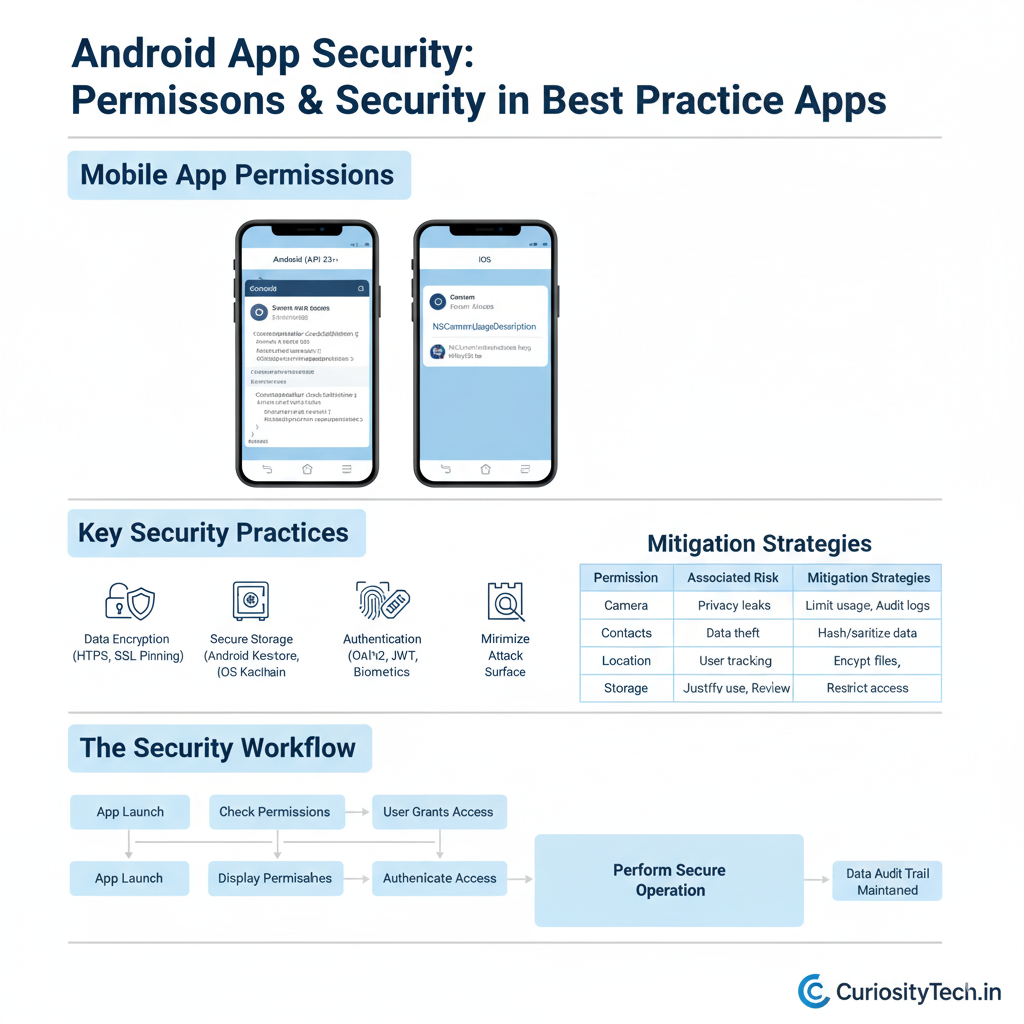
Description:- This hierarchy visually abstracts the stepwise process from runtime permission checks through authenticating and encrypting data and maintaining logs—all elements supported by Curiosity Tech’s comprehensive development services and workshops, detailed at curiositytech.in.
Practical Example: Encrypting Local Storage (Flutter)
dart
final key = encrypt.Key.fromLength(32);
final iv = encrypt.IV.fromLength(16);
final encrypter = encrypt.Encrypter(encrypt.AES(key));
final encrypted = encrypter.encrypt(“Sensitive Data”, iv: iv);
Explain: Encryption libraries should be introduced only where necessary, while secrets are stored using secure keystores (Android Keystore/iOS Keychain).
How to Become Expert in Handling Permissions & Security
- Learn platform-specific permission models and associated best practices (Android, iOS, cross-platform like Flutter/React Native).
- Stay current on mobile OS updates and new security vulnerabilities—follow sources like OWASP Mobile Security and Curiosity Tech’s blog.
- Participate in security audits, code reviews, and ethical hacking workshops.
- Experiment: Build real-world apps with deliberate security features, thoroughly documenting edge cases and permission responses.
Engage with the CuriosityTech community: Join live webinars, social media groups like curiositytechpark on Instagram, and use resources at curiositytech.in or call +91-9860555369 for direct mentorship.
Conclusion
Mastering permissions and security lays the cornerstone for professional cross-platform app development. By applying proven techniques—runtime permission management, encryption, secure authentication—and integrating regular audits, developers will create apps that earn user trust and withstand emerging threats. CuriosityTech.in proudly drives this mission in India’s tech landscape, with expertise and resources for both learning and implementation.



