Introduction
Industrial IoT (IIoT) security in 2025 faces evolving and increasingly complex challenges. IIoT environments span legacy systems, diverse vendor devices, and critical operational technology (OT) networks where breaches risk physical safety, financial loss, and operational disruption. To address this, a multi-layered defense-in-depth strategy and continuous risk management process are fundamental.
This comprehensive guide draws upon the latest expert insights, industry standards, and emerging technological trends to present a thorough roadmap for securing IIoT ecosystems, essential for practitioners and decision-makers alike. I’ve structured it differently than the last post: here you’ll find challenges, framework and standards, best practices and CuriosityTech insights.
Key IIoT Security Challenges
- Legacy Equipment and Protocols: Many deployed systems lack built-in security or use plaintext protocols like Modbus, making them vulnerable.
- Operational Performance Constraints: IIoT requires real-time deterministic communication; security interventions must avoid adding latency.
- Physical Exposure & Tampering Risks: Devices scattered across factory floors, substations, or pipelines are susceptible to physical attacks.
- Device & Network Diversity: A multiplicity of vendors, OSes, and protocols complicate uniform security enforcement solutions.
- Massive Scale & Complexity: Thousands to millions of connected devices require scalable management and automation.
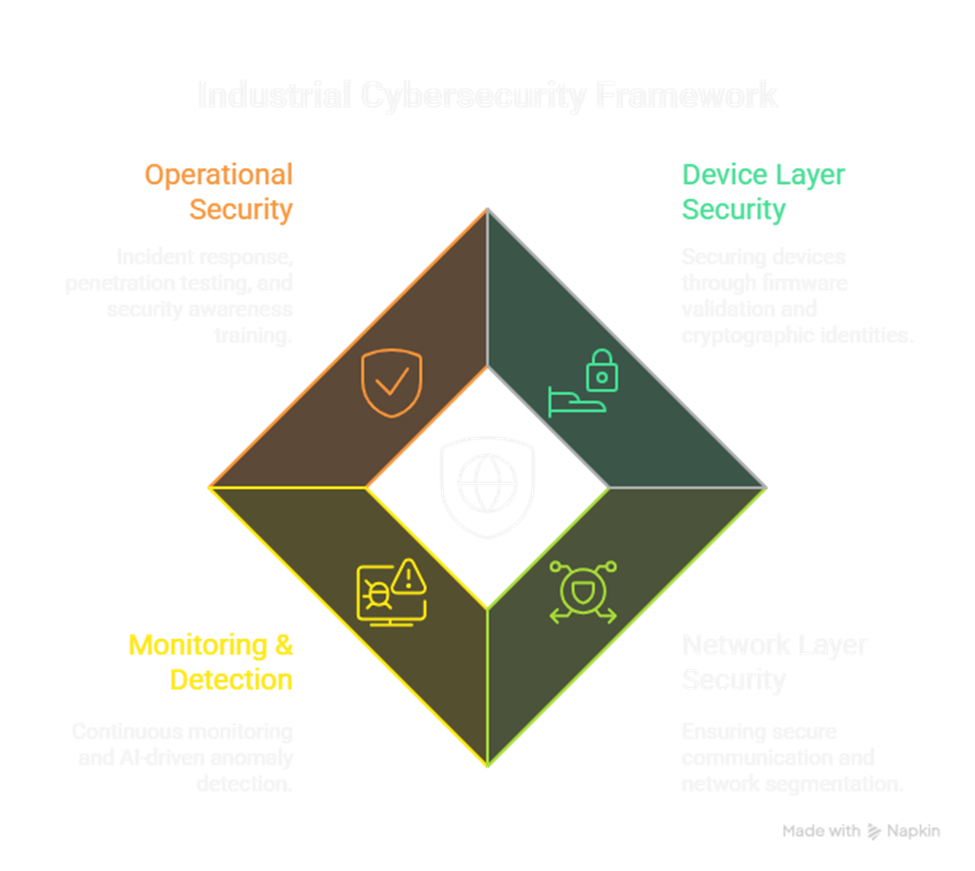
Multi-Layered IIoT Security Architecture
Device Layer
- Secure Boot: Device firmware validated cryptographically during startup to block unauthorized code execution.
- Hardware Root of Trust & TPMs: Secure storage of cryptographic keys and device identity.
- Unique Cryptographic Identities: Use X.509 certificates per device with lifecycle management.
- Secure Firmware & OTA Updates: Signed firmware and secure over-the-air update mechanisms prevent supply chain attacks.
Network Layer
- Encrypted Communications: TLS 1.3 enforced for protocols such as MQTT and OPC UA. No plaintext device communications.
- Network Segmentation & Zoning: Purdue model implementation isolates OT from IT layers with DMZ zones for gateways.
- Legacy Protocol Wrapping: Encapsulate or replace unsecured legacy protocols with secure tunnels or newer alternatives.
- Firewall & IDS Integration: Industrial-grade firewalls combined with intrusion detection/prevention tailored for industrial protocols.
Monitoring & Detection
- Continuous Device and Traffic Monitoring: Real-time event detection and collection feeding SIEM platforms.
- AI-Driven Anomaly Detection: Behaviors learned over time enable early detection of novel attack attempts.
- Passive Network Monitoring: Essential to avoid disrupting sensitive OT processes.
- Comprehensive Asset Inventory: Full visibility of connected devices, firmware versions, and configurations.
Operational Security
- Incident Response & Disaster Recovery: Well-rehearsed playbooks tailored for OT environments ensuring rapid containment and system restoration.
- Regular Penetration Testing & Audits: Focused on industrial communication protocols, firmware, and cloud interfaces.
- Security Awareness Training: Educate all personnel involved in OT management on phishing, safe device handling, and incident reporting.
Compliance Framework & Standards
- IEC 62443 Series: Global benchmark for industrial automation security.
- NIST Cybersecurity Framework: Adapted for critical infrastructure and IIoT.
- ISO/IEC 27001: Information security management, applicable for cloud and enterprise IT environments.
- Regulatory Standards: HIPAA for healthcare devices, GDPR for personal data, among others.
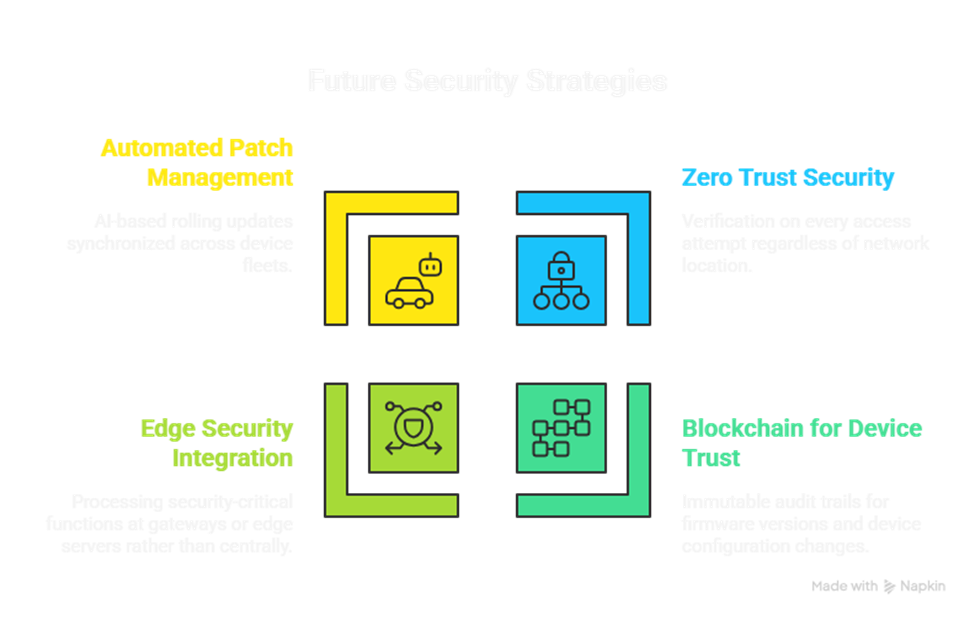
Emerging Best Practices for 2025
- Zero Trust Security: Verification on every access attempt regardless of network location.
- Blockchain for Device Trust: Immutable audit trails for firmware versions and device configuration changes.
- Edge Security Integration: Processing security-critical functions at gateways or edge servers rather than centrally.
- Automated Patch and Configuration Management: AI-based rolling updates synchronized across device fleets.
CuriosityTech Nagpur’s Approach to IIoT Security Training
- Hands-on lab setups with MQTT brokers configured for TLS and certificate authority.
- Network segmentation exercises mapping Purdue model zones with VLANs and firewalls.
- Realistic threat simulation exercises including MQTT flooding, credential theft, and firmware tampering.
- SIEM platform deployment and AI anomaly detection for OT device log aggregation.
Conclusion
Robust IIoT security in 2025 demands a comprehensive, multi-layered defense strategy consistent with industry standards, best practices, and emerging technologies. As cyber threats evolve, so must defenses—emphasizing zero trust, cryptographic device identity, secure communication, continuous monitoring, and well-prepared operational responses.
Institutions like CuriosityTech.in Nagpur play a pivotal role equipping next-generation IoT engineers with the knowledge and hands-on skills necessary to build resilient, secure, and future-proof industrial environments.

