Handbook Abstract
By 2025, IoT devices have become prime attack vectors for hackers. Whether it’s a smart home camera being hijacked for surveillance, a factory sensor leaking sensitive production data, or a pacemaker vulnerable to remote exploitation — IoT security is no longer optional, it’s mandatory. This handbook serves as a field-ready guide for IoT engineers to design, deploy, and maintain secure IoT ecosystems.
At Curiosity Tech Nagpur, one motto is repeated in every IoT bootcamp : “An insecure IoT system is worse than no IoT system at all.”
Threat Landscape in IoT (2025)
IoT threats evolve constantly, but the most common categories include:
- Device Hijacking – Malware installs on IoT cameras, routers, or gateways to form botnets (e.g., Mirai botnet).
- Data Interception – Man-in-the-middle attacks stealing sensor data.
- Firmware Exploits – Outdated firmware with vulnerabilities exploited by attackers.
- Unauthorized Access – Weak or default passwords on IoT dashboards.
- Physical Tampering – Attackers opening IoT devices, replacing chips, or injecting malicious firmware.
Layered Defense Framework (The “IoT Security Onion”)
Think of IoT security like an onion with protective layers:
- Device Layer Security :-
- Secure boot processes.
- Unique device identifiers.
- No default hard-coded credentials.
- Network Layer Security :-
- Encrypted transmission (TLS/DTLS).
- Firewalls for IoT gateways.
- VPN tunnels for industrial deployments.
- Application & Data Security :-
- Strong API authentication and authorization.
- Data encryption at rest in cloud databases.
- Secure dashboard login with MFA.
- Cloud & Edge Security :-
- Role-based access in AWS, Azure, or Google IoT platforms.
- Monitoring for anomalies (e.g., unusual traffic bursts).
- Edge device hardening (disable unnecessary ports, patch OS).
Best Practices Checklist
Device Security
- ✅ Implement secure boot and encrypted firmware.
- ✅ Force per-device unique certificates.
- ✅ Disable debugging interfaces (UART/JTAG) in production.
Data Transmission Security
- ✅ Always use MQTT over TLS, never plain MQTT.
- ✅ Implement mutual authentication (both device & server verify each other).
- ✅ Rotate encryption keys regularly.
Cloud & Storage Security
- ✅ Encrypt sensitive IoT data at rest using AES-256.
- ✅ Apply token-based API requests.
- ✅ Monitor for suspicious cloud activity using built-in alerting.
Operational Security
- ✅ Patch management system for IoT firmware updates (OTA).
- ✅ Enable audit logs for compliance.
- ✅ Train teams on incident response workflow.
Case Study 1: Smart Camera Breach
Incident: Millions of unsecured CCTV cameras worldwide were hijacked and became part of the Mirai botnet.
Cause: Default admin passwords remained unchanged.
Lesson: Always enforce unique, secure credentials and force updates at first boot.
Case Study 2: Smart Healthcare Wearable Attack
Incident: A hospital in the US faced breaches when fitness trackers connected to patient apps transmitted unencrypted data.
Cause: HTTP instead of HTTPS/TLS; lack of API authentication.
Lesson: Data in healthcare IoT must be encrypted end-to-end to comply with HIPAA/GDPR.
Case Study 3: Industrial IoT Plant Malfunction (Simulated at CuriosityTech Labs)
Scenario: Trainee engineers simulated an attack on factory vibration sensors controlling motors. Attackers flooded MQTT broker with false data (MQTT flooding).
Mitigation Applied:
- Setup broker authentication.
- Implemented rate-limiting on messages.
- Configured anomaly detection to spot unusual traffic burst.
- Result: Security restored, demonstrating importance of MQTT hardening.
Key Security Tools and Frameworks (2025)
- AWS IoT Device Defender – Security audits, alerts, network monitoring.
- Azure Security Center for IoT – Threat intelligence, policy checks.
- Google IoT IAM + Shielded VM – Access controls & runtime protections.
- EdgeX Foundry Security Services – Edge-specific APIs for secure device management.
Diagram: IoT Threat Vectors (Conceptual Description)
Picture IoT ecosystem layers (Device → Network → Cloud → App). Threat vectors point inward from all sides:
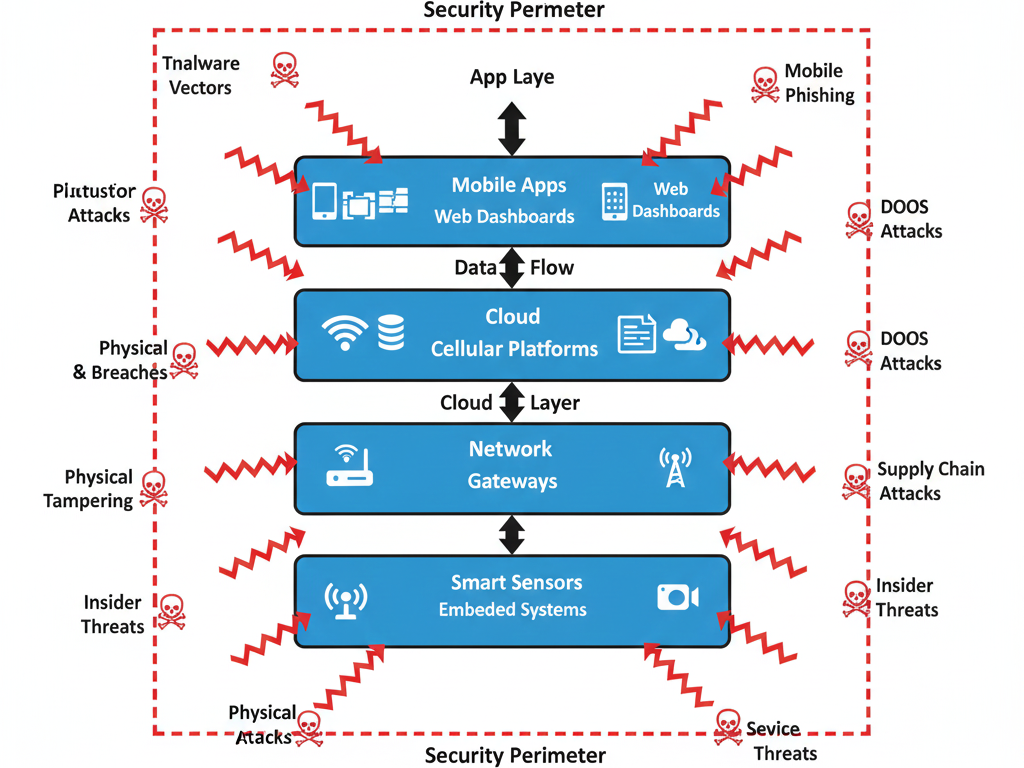
- Red arrows at Device = malware injection, physical tampering.
- Red arrows at Network = man-in-the-middle, packet sniffing.
- Red arrows at Cloud = API hacks, database breaches.
- Red arrows at Apps = weak login, phishing dashboards.
This visual onion demonstrates that every layer of IoT can, and will, be attacked.
Training Engineers for IoT Security
At Curiosity Tech Nagpur, IoT engineers undergo hands-on labs like:
- Ethical hacking exercises – breaking into an unsecured ESP32 MQTT connection.
- Secure by design workshop – implementing TLS, OTA patching, and token-based APIs.
- Incident response drills – simulating cyber threats in industrial settings.
True IoT expertise in 2025 is about building systems that assume attack will happen — and are engineered to defend, detect, and recover quickly.
Conclusion
In IoT, “connectivity without security” is a recipe for disaster. With the rising number of connected devices in 2025, IoT engineers must adopt secure-by-design principles: hardened devices, encrypted transmissions, layered defenses, and continuous monitoring. Security is not a one-time setting but an ongoing discipline of vigilance and adaptation.