When I consult with businesses—from startups in Nagpur to multinational partners—the number one question they ask after setting up technical defenses is: “Are we compliant?”
Why? Because in 2025, failure to follow security policies and compliance standards doesn’t just mean higher security risk—it means legal penalties, loss of reputation, and even business shutdowns.
At Curiosity Tech Nagpur, we train not only on firewalls and penetration tests but also on the organizational side—ISO standards, GDPR, HIPAA, and others—which every cyber security engineer and manager must know. This blog is structured like a briefing note you’d present to executives.
Why Security Policies Matter
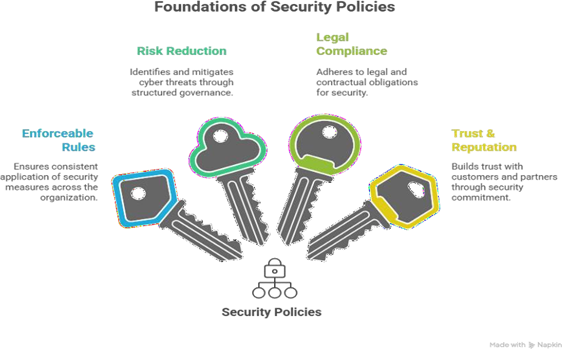
Core Global Compliance Standards Overview
Executive Brief – Case Lessons from History
1: British Airways GDPR Breach (2018)
- Attackers diverted user traffic to fraudulent site → exposed 400,000+ customers’ data.
- GDPR fine: £183 million (later negotiated lower).
- Lesson: Even large enterprises must follow privacy by design and patch timely.
2: Anthem Health HIPAA Breach (2015)
- Hackers stole nearly 79 million patient records (names, SSNs, medical IDs).
- HIPAA fine: $16 million.
- Lesson: Securing PHI is not optional. Healthcare organizations must encrypt, audit, and restrict access.
3: Small Indian Outsourcing Firm Losing ISO 27001 Certification (2020)
- Poor documentation and lack of periodic audits.
- Contracts with major EU clients revoked.
- Lesson: Standard compliance directly ties to business continuity.
Security Policies (Engineer’s Role)
It’s easy to think compliance is all about executives—but engineers build compliance into systems.
Key Policy Areas
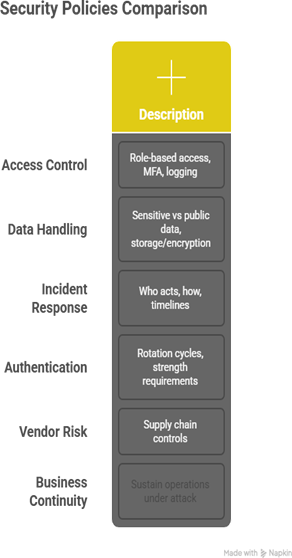
At CuriosityTech, our compliance lab simulates policy enforcement. Students practice:
- Writing data classification policy.
- Enforcing access control lists technically on servers.
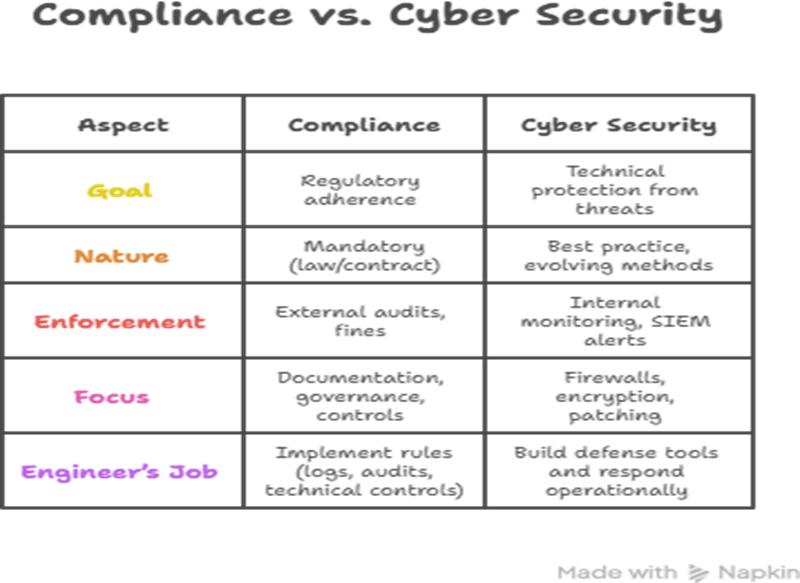
Comparative Snapshot: Compliance vs Security
| Aspect | Compliance (ISO/GDPR/HIPAA) | Cyber Security Practice |
| Goal | Regulatory adherence. | Technical protection from threats. |
| Nature | Mandatory (law/contract). | Best practice, evolving methods. |
| Enforcement | External audits, fines. | Internal monitoring, SIEM alerts. |
| Focus | Documentation, governance, controls. | Firewalls, encryption, patching. |
| Engineer’s Job | Implement rules (logs, audits, technical controls). | Build defense tools and respond operationally. |
Step-by-Step Framework for Organizations
1: Identify Standard(s)
- Healthcare = HIPAA.
- EU customers = GDPR.
- Global IT services = ISO 27001.
2: Map Current Security Posture
- Run a gap assessment (policies vs actual practice).
3: Build Security Policies
- Draft policies covering access controls, encryption, incident response.
4: Implement Controls Technically
- Example: ISO requires access control → configure IAM & logging.
- GDPR requires user consent → modify web apps with consent banners + opt-out systems.
5: Train Employees
- No compliance works without human awareness. 60% of GDPR fines come from human mistakes.
6: Monitor, Audit, Improve
- Continuous compliance is required; standards evolve.
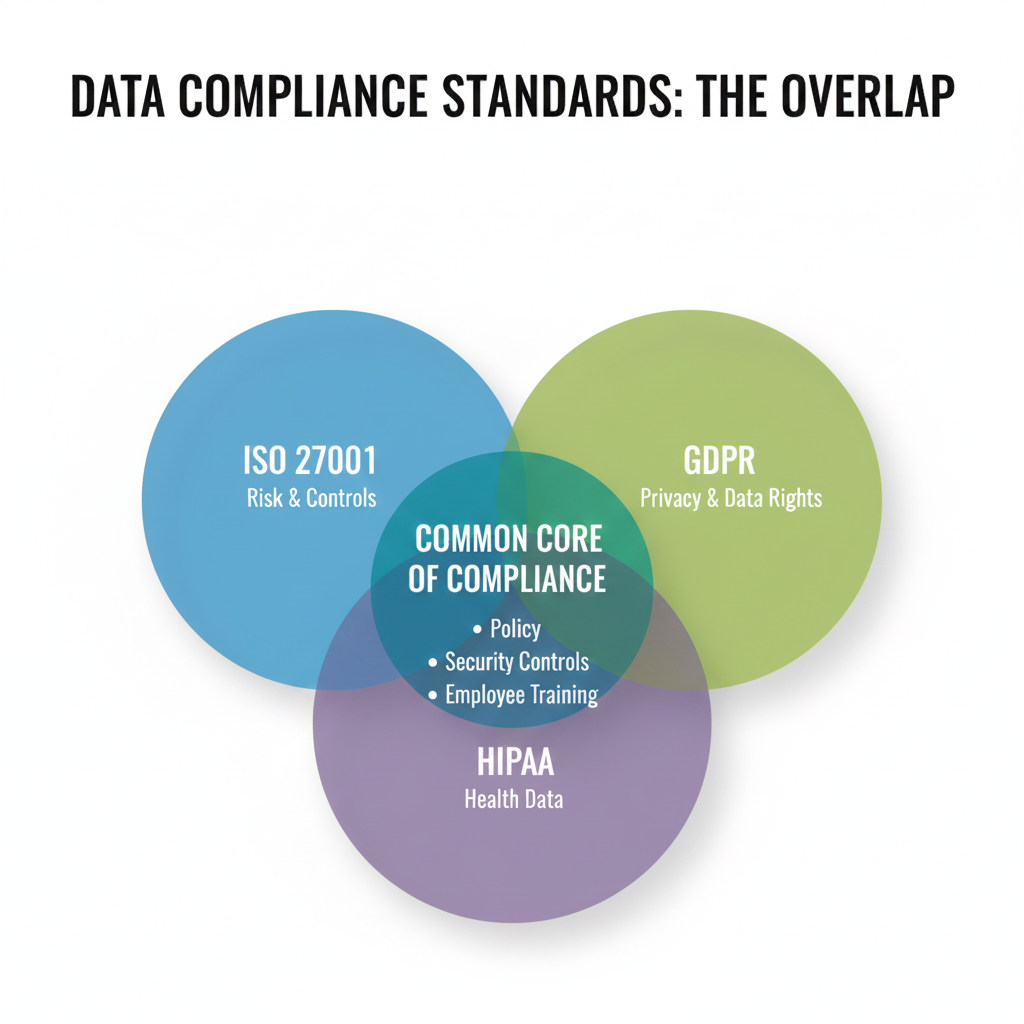
Infographic Description
A Venn diagram infographic:
My Personal Field Insight
In 2021, I worked with a mid-sized IT services firm in Nagpur outsourcing for a European retail company. They had robust security tools but no documentation of policies. An EU client audit flagged them immediately, nearly canceling the contract. With just two weeks, we built ISO-aligned documentation, introduced logs, and trained staff. Their contract survived—but they learned a hard lesson: compliance is not optional paperwork. It’s your passport to keep doing business.
Conclusion
In 2025, policies and compliance standards are as critical as firewalls and encryption. ISO 27001 guarantees globally trusted governance, GDPR mandates respect for personal data, and HIPAA enforces security in healthcare. Engineers, managers, and executives must treat compliance as core infrastructure, not a side task.
At CuriosityTech.in (1st Floor, Plot No 81, Wardha Rd, Gajanan Nagar, Nagpur | Phone: +91-9860555369 | Email: contact@curiositytech.in | Instagram: @curiositytechpark | LinkedIn / Facebook: Curiosity Tech), we build labs where students not only configure servers but draft compliance-aligned policies, simulating real audits. Because to survive the modern cyber war, compliance is law + business + engineering in action.



