In 2014, I was assisting a manufacturing firm in Nagpur hit by a suspected insider attack. Logs existed—from firewalls, servers, applications—but they were scattered, unread, and unanalyzed. The attacker’s footsteps were hiding in plain sight, but no one could connect the dots. That’s when I introduced them to a SIEM (Security Information and Event Management) solution, which stitched together logs into actionable intelligence.
Fast forward to 2025, SIEM tools remain the digital nerve center of cyber security—without structured monitoring and logging, even the most advanced defenses go blind.
At Curiosity Tech Nagpur, our labs teach how logs travel from devices to a SIEM dashboard, how correlations expose attacks, and how engineers learn to think like detectives.
What is SIEM?
Security Information and Event Management (SIEM) systems collect and aggregate logs from across infrastructure, correlate them, and generate alerts for suspicious patterns.
Think of SIEM as a crime detective: every server, router, firewall, and endpoint reports their diary; SIEM cross-checks these diaries to detect when stories don’t align—revealing crimes.
The Log Lifecycle
A flow diagram shows:
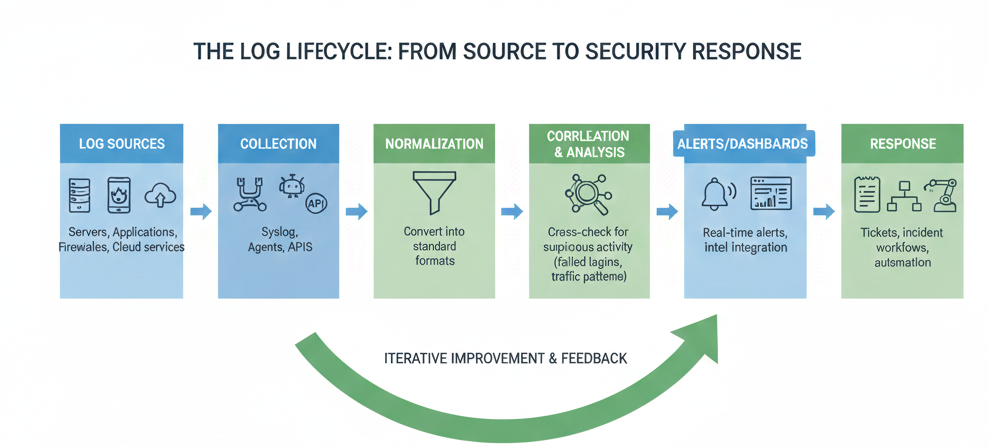
This is the heartbeat of SIEM.
SIEM Dashboard Storytelling
Imagine you’re looking at a SIEM dashboard during a live incident:
- Top panel: Heat map showing spikes of failed login attempts across India.
- Center graph: Real-time connections—sudden outbound traffic to an unknown IP flagged.
- Left column: Log timeline—“10 failed RDP login attempts from IP 45.12.221…”
- Alert box: “Critical: Possible brute force attack on Finance Server.”
This visualization gives engineers contextual awareness within seconds—something raw logs can’t deliver.
Leading SIEM Tools in 2025
| Tool | Strengths | Use Case |
| Splunk | Highly scalable, customizable dashboards. | Fortune 500 enterprises, complex multi-cloud environments. |
| ELK Stack (Elasticsearch-Logstash-Kibana) | Open-source, cost-effective, great visualization. | SMEs, labs, DevOps environments. |
| IBM QRadar | Strong correlation & compliance reporting. | Banks, healthcare, high-regulation sectors. |
| Microsoft Sentinel (Azure-native) | Native integration with Azure + AI-based analytics. | Cloud-first organizations. |
| Chronicle SIEM (by Google) | Handles petabytes of data with Google infrastructure. | Global corporations needing advanced scale. |
Attack Scenario with SIEM in Action
Scenario: SSH Brute Force Attack
- Firewall logs: multiple failed SSH attempts from a foreign IP.
- Server logs: unusual login attempt timestamps.
- SIEM correlates logs → raises alert with severity “Critical.”
- Dashboard highlights attacker’s pattern (50 attempts/min).
- Engineer receives alert, blocks IP, enforces MFA for SSH.
Without SIEM? Data remains siloed, unnoticed until attacker succeeds.
Compliance through SIEM
- ISO 27001: Requires central logging and monitoring.
- GDPR: SIEM supports evidential logging for breach reporting.
- HIPAA: Monitors access to patient records and logs abnormal usage.
- PCI-DSS: Centralized log review mandatory for card data systems.
At CuriosityTech training, students simulate PCI-DSS compliance reports through Splunk dashboards that show every cardholder data access event.
SIEM Implementation Best Practices
1: Identify Log Sources
- Firewalls, VPN, antivirus, user directories, app servers, cloud workloads.
2: Log Collection
- Use Syslog, forwarders, or API-based ingestion.
3: Normalize & Parse
- Translate different formats into universal log schemas.
4: Correlation Rules
- Define rules detecting brute-force, privilege escalation, data exfiltration.
5: Alerts & Response
- Configure thresholds.
- Integrate with SOAR (Security Orchestration, Automation, and Response) for automated blocking.
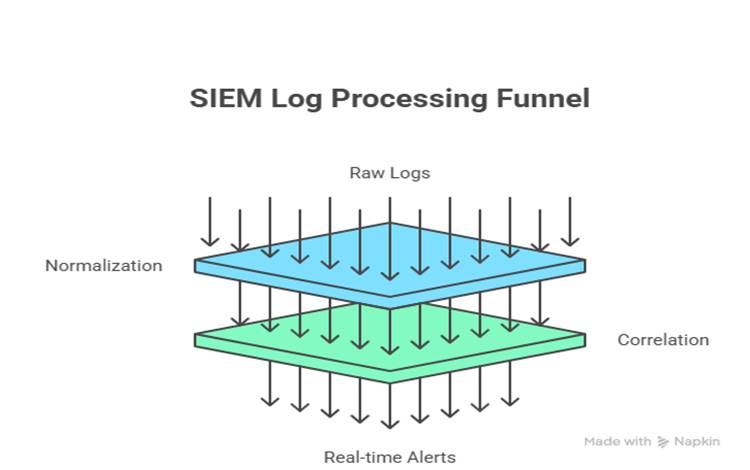
Infographic Description
A funnel infographic:
- Top wide funnel: “Raw Logs (firewalls, servers, cloud).”
- Middle narrowing: “Normalization + Correlation.”
- Bottom output: “Real-time Alerts on dashboards.”
On the sides: arrows pointing to “Compliance Reporting” and “Automated Response.”
This clearly shows how SIEM transforms “data overload” into “actionable intelligence.”
Real Consulting Anecdote
In 2019, a Nagpur IT company faced repeated ransomware attempts. Logs existed on endpoints reporting suspicious encryption attempts—but IT ignored them. After implementing Splunk SIEM, a repeat attack attempt was detected in seconds. The system automatically blocked the process, saving 200+ employee endpoints from encryption.
Lesson: Logs without SIEM are like CCTV footage no one watches. With SIEM, you catch thieves in real time.
Engineer’s SIEM Hands-On Lab (CuriosityTech Style)
- Forward Apache web server logs into ELK Stack.
- Simulate SQL injection attempt on test web app.
- Observe Kibana dashboard highlight abnormal query.
- Create alert rule that emails administrator when detected.
- Document incident → build compliance report.
This lab teaches engineers the end-to-end SIEM journey—from log ingestion to forensic reporting.
Conclusion
In 2025, SIEM isn’t just for enterprises—it’s a necessity for any organization relying on digital systems. Logs are your most valuable forensic evidence, and SIEM transforms them into real-time protections.
At CuriosityTech.in (Address: 1st Floor, Plot No 81, Wardha Rd, Gajanan Nagar, Nagpur | Contact: +91-9860555369 | Email: contact@curiositytech.in | Socials: Instagram @curiositytechpark, LinkedIn/Facebook: Curiosity Tech), our programs give learners hands-on SIEM dashboards, not just theory. Because cyber engineers must learn not only to build defenses—but to monitor them like detectives in a 24×7 battlefield.



