Over the past two decades, one of my greatest privileges as a cybersecurity consultant has been helping organizations turn near-disasters into success stories. Cyber threats are universal—impacting hospitals, banks, IT firms, and even local startups. But what separates those who fall from those who survive is a combination of preparation, timely response, and layered strategy.
At CuriosityTech.in, Nagpur, we teach engineers that prevention isn’t abstract theory—it’s about learning from real-world battles. Below are four stories across industries, illustrating how clever strategies and discipline prevented cyber catastrophes.
Case 1 – Banking Sector: Stopping a Phishing Campaign
Problem: In 2022, a regional bank faced a wave of phishing emails impersonating its executives. Attackers crafted convincing emails urging staff to “approve urgent wire transfers.” Early employees fell into the trap, risking millions.
Response:
- Bank contacted security consultants quickly.
- Security team deployed Secure Email Gateway with DMARC, SPF, and DKIM enforcement.
- Phishing awareness training conducted for all employees, with simulated phishing every month.
- Multifactor authentication (MFA) added to all transfer approvals.
Tools Involved: Microsoft 365 Defender, Mimecast, SIEM log correlation.
Outcome:
- Phishing attacks still arrived—but employees began reporting rather than clicking.
- The number of “clicks” in simulated training dropped from 20% to below 2% in six months.
- No fraudulent transactions occurred.
Lesson for Engineers: Tools are not enough; human firewall must be trained.
Case 2 – Healthcare Sector: Protecting Patient Data From Ransomware
Problem: A mid-sized hospital using outdated Windows servers was hit with an attempted ransomware campaign. Malware entered via a malicious email attachment opened by an employee. Within minutes, infections began encrypting files.
Response:
- Hospital IT had deployed endpoint detection & response (EDR) earlier as part of HIPAA compliance.
- Suspicious file actions (mass encryption attempts) immediately triggered alerts.
- Network segmentation prevented ransomware from spreading to medical equipment systems.
- Offline backup systems restored critical patient data.
Tools Involved: CrowdStrike Falcon (EDR), Veeam Backup, Cisco Firewalls.
Outcome:
- Ransomware stopped at 15 machines before full hospital compromise.
- Downtime limited to only 6 hours (compared to days in similar hospitals).
Lesson for Engineers: Preventing cyber attacks is about layered security + backups.
Case 3 – E-Commerce Startup: Preventing SQL Injection
Problem:
In 2023, a growing Nagpur-based e-commerce startup faced a serious threat: ethical hackers reported that their login page was vulnerable to SQL Injection. A malicious actor could exfiltrate entire customer databases.
Response:
- Security team fixed vulnerable code by switching from dynamic SQL to parameterized queries.
- Deployed a Web Application Firewall (WAF) to filter malicious inputs.
- Conducted penetration test using Kali Linux tools (SQLmap) to verify patch success.
Tools Involved: Nginx WAF, Burp Suite, SQLmap, OWASP ZAP.
Outcome:
- Vulnerability patched before exploitation.
- Startup received ISO 27001 certification for improved governance—helping them close deals with European clients subject to GDPR.
Lesson for Engineers: Timely secure coding saves both data breaches and business reputation.
Case 4 – Manufacturing Industry: Defending Against Insider Threats
Problem: A manufacturing firm noticed large outbound data transfer attempts late at night. Suspicion grew of an insider potentially stealing Intellectual Property (IP) designs.
Response:
- Deployed User and Entity Behavior Analytics (UEBA) through SIEM system.
- Detected anomalies: a junior engineer account logged in from Nagpur, yet attempted large transfers to an unusual IP address.
- Investigation revealed compromised credentials were used.
- Rapid incident response: account revoked, new IAM rules enforced, and forensic log analysis performed.
Tools Involved: Splunk SIEM with UEBA, AWS IAM, Digital Forensics EnCase.
Outcome:
- Data theft attempt disrupted before exfiltration.
- Company avoided millions in losses from stolen designs.
- Strengthened Zero Trust Model internally.
Lesson for Engineers: Not only “outsiders” threaten you—insider threat detection is critical.
Comparative Insights from these Cases
| Industry | Threat Faced | Prevention Strategy | Core Lesson |
| Banking | Phishing | Email filtering + MFA + awareness | Employees are first defense. |
| Healthcare | Ransomware | EDR + backups + segmentation | Resilience wins, not just defense. |
| E-Commerce | SQL Injection | Secure coding + WAF + Pentest | Fix issues before exploitation. |
| Manufacturing | Insider Threat | SIEM + UEBA + Zero Trust | Watch inside as much as outside. |
Infographic Description
An industry-shield infographic:
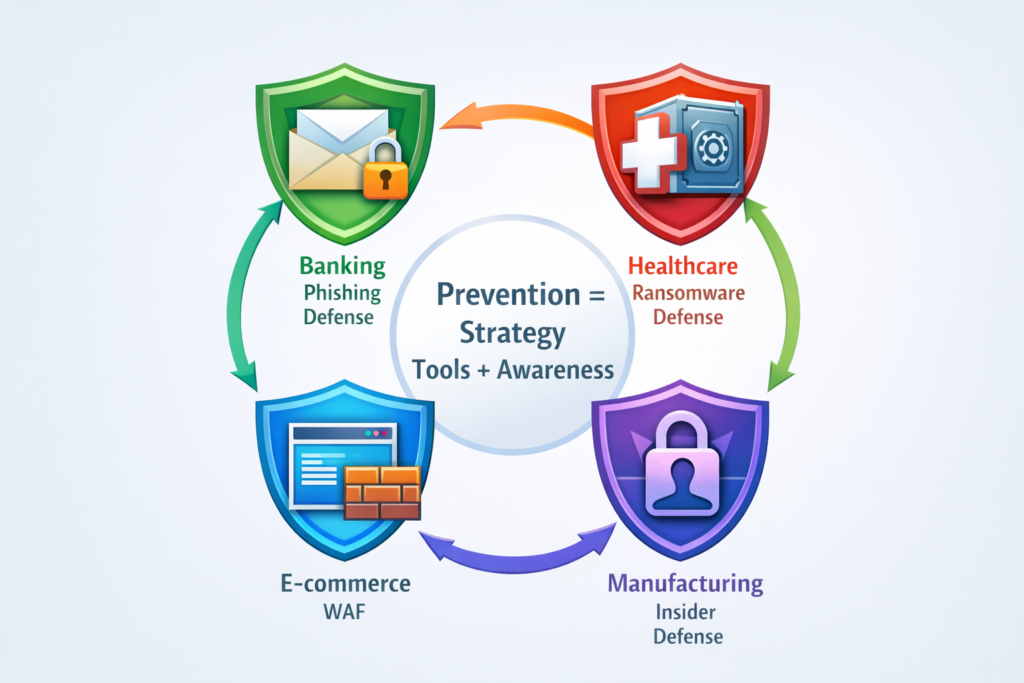
- Four shields arranged in a circle.
- Shield 1 (Banking): Envelope with padlock (phishing defense).
- Shield 2 (Healthcare): Cross symbol with backup vault (ransomware defense).
- Shield 3 (E-commerce): Web page with brick wall (WAF).
- Shield 4 (Manufacturing): Human silhouette inside lock (insider defense).
- Center label: “Prevention = Strategy + Tools + Awareness.”
My Personal Insight
Some of my proudest consulting stories aren’t just stopping attacks—but seeing companies evolve because of them. At CuriosityTech, one client told me: “We didn’t just prevent a cyber attack, we became more disciplined as a business.” That is the hidden lesson—security transforms business culture.
Conclusion
Whether it’s banks fending off phishing, hospitals surviving ransomware, startups fixing vulnerable code, or manufacturers catching insider threats, prevention is never “one magic tool.” It always comes down to awareness, layered tools, proactive governance, and monitoring.
At CuriosityTech.in (Gajanan Nagar, Nagpur | Phone: +91-9860555369 | Email: contact@curiositytech.in | Socials: Instagram @curiositytechpark, LinkedIn/Facebook: Curiosity Tech) we recreate such case studies in lab form, so learners can experience the fears, actions, and relief of real-world defenders. Because future engineers must not only know techniques—they must feel the urgency that drives security culture.



