Introduction
In 2025, Industrial IoT (IIoT) security is paramount to ensuring uninterrupted, safe, and compliant manufacturing and critical infrastructure operations. The rise of sophisticated cyber threats combined with complex IIoT ecosystems demands a multi-layered, adaptive security strategy spanning devices, communication networks, cloud platforms, and operational processes.
This guide consolidates comprehensive industry best practices, emerging security frameworks, case insights, and strategic approaches to defend IIoT environments, based on cutting-edge insights from the latest expert reports and standards.
Unique Challenges of IIoT Security
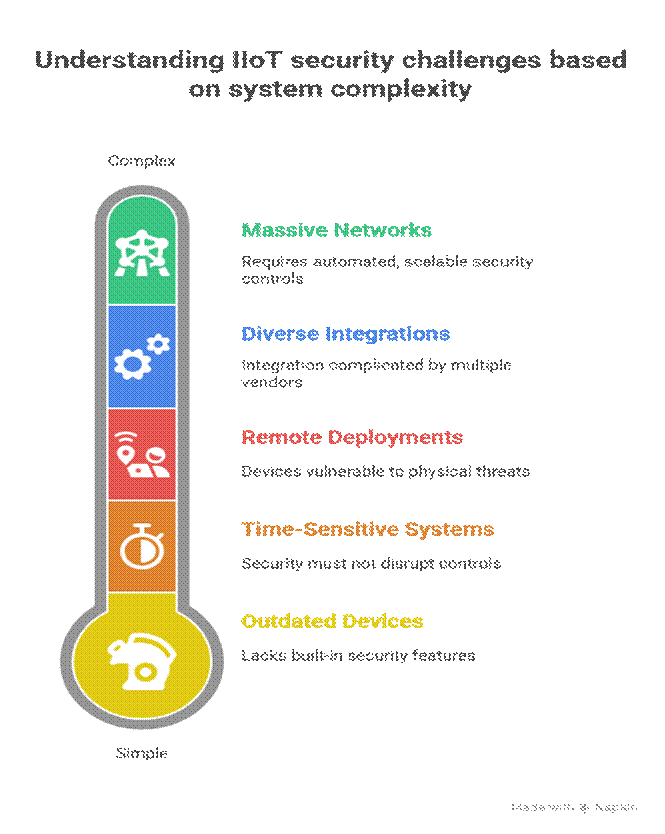
- Legacy Equipment: Industrial devices often have outdated or no built-in security.
- Real-Time Operational Constraints: Security solutions must not induce latency or disrupt deterministic controls.
- Physical and Network Exposure: Devices deployed in harsh or remote zones are physically vulnerable.
- Diverse and Heterogeneous Systems: Multiple vendors, protocols, and systems complicate integration.
- Scale of Deployment: Thousands to millions of devices require automated, scalable controls.
Core Principles: Defense-in-Depth for IIoT
Device Security
- Secure Boot and Hardware Root of Trust: Ensures running firmware is authentic, preventing malicious code.
- Unique Device Identity: Each device is provisioned with X.509 certificates or hardware-backed keys for authentication.
- Firmware Integrity Checks and Secure OTA Updates: Prevents unauthorized firmware installation; facilitates patches.
- Trusted Platform Modules: Hardware security modules secure cryptographic keys and device state.
Network Security
- Encrypted Communication: TLS/DTLS for MQTT, secured OPC-UA, and HTTPS. No plaintext protocols (e.g., raw Modbus).
- Segmented and Isolated Networks: Purdue model with zones/levels, DMZs separating IT and OT systems.
- Secure IoT Gateways: Gateways enforce policies, filter traffic, and securely bridge OT devices to cloud.
- Replace or Wrap Legacy Protocols: Use secure tunnels or protocol converters to upgrade older equipment.
Monitoring & Anomaly Detection
- Intrusion Detection & Prevention Systems (IDS/IPS): Tailored for industrial protocols.
- Centralized SIEM Platforms: Correlate OT and IT logs for holistic threat visibility.
- Passive Monitoring: Avoids disruption in sensitive industrial processes while surveilling traffic.
- AI-Driven Behavioral Analytics: Baseline normal device behavior and detect deviations promptly.
Operations & Response
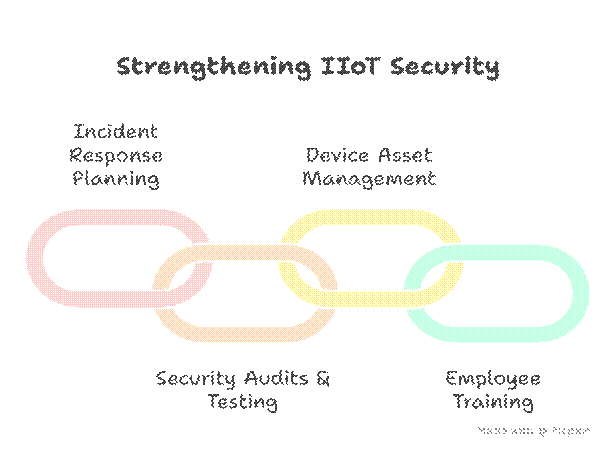
- Incident Response Planning: Tailored for industrial ecosystems including emergency shutdown procedures.
- Continuous Security Audits & Penetration Testing: Identify vulnerabilities before attackers exploit them.
- Comprehensive Device Asset Management: Full inventory with contextual metadata.
- Comprehensive Employee Training: Awareness of OT cybersecurity best practices and phishing threats.
Practical Best Practices Summary
| Practice | Description & Benefits |
| Secure Boot & Firmware Signing | Prevents malicious firmware injection |
| Device Certificate Management | Strong device identity and network access control |
| Firmware OTA Updates | Keep devices patched remotely, reduce vulnerabilities |
| Network Segmentation | Contain breaches, limit lateral movement |
| Encrypted Communications | Protects data confidentiality and integrity |
| Continuous Monitoring & SIEM | Real-time alerting and threat hunting |
| Legacy Protocol Protection | Use secure tunnels or replace insecure protocols |
| Incident Response Simulation | Preparedness for minimizing impact in attacks |
| Employee Training | Reduces human error risks |
| Regulatory Compliance | Ensures adherence to IEC 62443, NIST, GDPR |
Real-World Success Stories
- Automotive Manufacturing: Implementation of segmentation and TPM-enabled IoT devices helped prevent ransomware spread.
- Energy Sector: AI-powered anomaly detection in power plants led to early detection of sabotage attempts.
- Healthcare Manufacturing: Encryption and secure OTA updates helped meet HIPAA and FDA standards.
Emerging Trends in IIoT Security
- Zero Trust Architectures: Access verification continuously required, no implicit trust.
- Blockchain for Device Identity and Integrity: Immutable ledger of firmware versions and updates.
- Edge-based Security Functions: Moving intrusion detection and anomaly analysis to IoT gateways and edge nodes.
- Automated Patch Management: AI-driven scheduling of updates with minimal downtime.
CuriosityTech Nagpur Security Curriculum Highlights
- Labs on implementing MQTT TLS with certificate authority and mutual authentication.
- Network segmentation exercises using VLANs and firewalls.
- Hands-on penetration testing of IoT devices and protocol fuzzing.
- Deploying SIEM and AI-anomaly detection in a simulated industrial environment.
Conclusion
Securing IIoT in 2025 requires a holistic, layered security strategy that encompasses device identity, encrypted communications, network zoning, continuous monitoring, and robust operational readiness. The evolving threat landscape—combined with the critical nature of industrial processes—makes proactive IIoT security not just a best practice, but a business imperative.
Through focused training and real-world simulation, organizations like CuriosityTech.in Nagpur prepare engineers to design, deploy, and defend future-ready IIoT systems with confidence and resilience.



