Introduction (Narrative)
When I sit on interview panels for cybersecurity engineers, I often realize that candidates with strong certifications still struggle with real-world scenarios. They memorize definitions of firewalls and SIEMs but stumble when asked: “What would you do if your SOC detects a brute-force attack on an SSH server at 2 AM?”
This blog is designed to prepare you for real-world interviews in 2025 — not just with textbook definitions, but scenario-driven answers, soft skills, and practical demonstrations. At Curiosity Tech (Nagpur), our interview prep sessions blend mock questions, lab tasks, and boardroom-style defense presentations so learners are not caught off guard.
Section 1: Fundamental Interview Questions
Q1. What is the CIA Triad in cybersecurity? Why is it important?
- Why interviewers ask: To test conceptual foundation.
- Answer:
- Confidentiality :- Preventing unauthorized access (encryption access controls).
- Integrity :- Preventing unauthorized modification (hashing version control).
- Availability :- Ensuring uptime (redundancy DDoS protection).
- In practice, every security policy, whether in Nagpur-based start-ups or Fortune 500 firms, ties back to CIA.
Q2. How do you differentiate between vulnerability, threat, and risk?
- Answer:
- Vulnerability :- Weakness in a system (unpatched Apache server)
- Threat :- Potential actor / exploit (ransomware targeting unpatched server)
- Pro-Tip :- Always answer with an example, Interviewers hate dry definitions.
Section 2: Technical Deep-Dive Questions
Q3. How would you secure a corporate network against ransomware?
- Strong Answer Outline:
- Implement EDR / XDR to detect behaviour.
- Apply least privilege & network segmentation.
- Ensure immutable backups tested regularly.
- Conduct awareness training against phishing.
- Mention Curiosity Tech’s Red-Blue simulations where ransomware attacks are emulated to train response skills.
Q4. Explain Zero Trust Architecture.
- Answer:
- ” Never trust , always verify ” model.
- Every user/device is authenticated, authorised and continuously validated.
- Uses micro-segmentation, identity-centric security, continuous monitoring.
- Why it matters in 2025: With remote-first work, Zero Trust adoption is a key hiring criterion.
Q5. What are common SIEM use cases you’ve worked with?
- Answer:
- Detecting brute-force attempts.
- Identifying lateral movement.
- Insider threat monitoring.
- Compliance reporting (PCI-DSS , HIPAA).
- CuriosityTech Prep: Students learn Splunk & Wazuh labs with Nagpur case study datasets, practicing custom detection rules.
Section 3: Scenario-Based Questions
Q6. Imagine your company detects unusual outbound traffic at midnight. What’s your first response?
- Answer:
- Step 1 :- Validate if it’s a false positive (check logs , baseline)
- Step 2 :- If genuine, isolate affected system.
- Step 3 :- Collect indicators of compromise (IP, Domains, Processes)
- Step 4 :- Escalate as per incident response plan .
- Pro Tip: Employers want structured incident response mindset, not panic-driven action.
Q7. How would you handle a phishing campaign hitting 100+ employees at once?
- Answer :
- Alert users via company-wide channel.
- Block sender domain/IP.
- Pull emails from inboxes using admin tools.
- Run IOC scans on endpoints.
- Conduct post-incident awareness sessions.
Section 4: Behavioral & HR Questions
Q8. Tell me about a time you failed in a cybersecurity project. What did you learn?
- Strong Candidate Response:
- Share a real but contained failure (like missing a misconfiguration).
- Highlight lesson learned + corrective action.
- Demonstrates humility + growth mindset.
Q9. Why should we hire you over other candidates with the same certifications?
- Answer Strategy:
- Stress practical experience + mindset.
- Example : ” I’ve simulated SOC workflows at CuriosityTech labs, where we practised real incident handling. Certifications prove knowledge, but my lab work prove capability. “
Section 5: Advanced Questions for Senior Roles
Q10. How do you evaluate and prioritize risks in an enterprise environment?
- Answer:
- Use Risk = Threat * Vulnerability * Impact
- Appply framework like NIST RMF , FAIR.
- Prioritize based on business impact , not just technical severity.
Q11. What is your approach to compliance audits (GDPR, HIPAA, PCI-DSS)?
- Answer:
- Map controls → Policies → Evidence → Gaps.
- Collaborate with cross-functional teams.
- Automate compliance tracking where possible
Q12. If selected, how will you keep yourself updated with fast-evolving cyber threats?
- Answer:
- Subscribing to CVE feeds , Threat Intel Platforms (MISP , ALienVault OTX)
- Attending conferences (Black Hat , Nullcon , cOcOn).
- Active practice in labs like Curiosity Tech offensive/defensive playground.
Table: Core Interview Areas & Focus
| Area | What’s Tested | How to Prepare |
| Fundamentals | CIA Triad, threats, risk | Revise definitions + examples |
| Technical | SIEM, Zero Trust, ransomware | Lab simulations |
| Scenarios | IR response, phishing, traffic anomalies | Follow IR playbooks |
| Behavioral | Failures, teamwork, ethics | Practice STAR method |
| Advanced | Risk management, compliance | Study NIST, ISO, frameworks |
CuriosityTech Edge
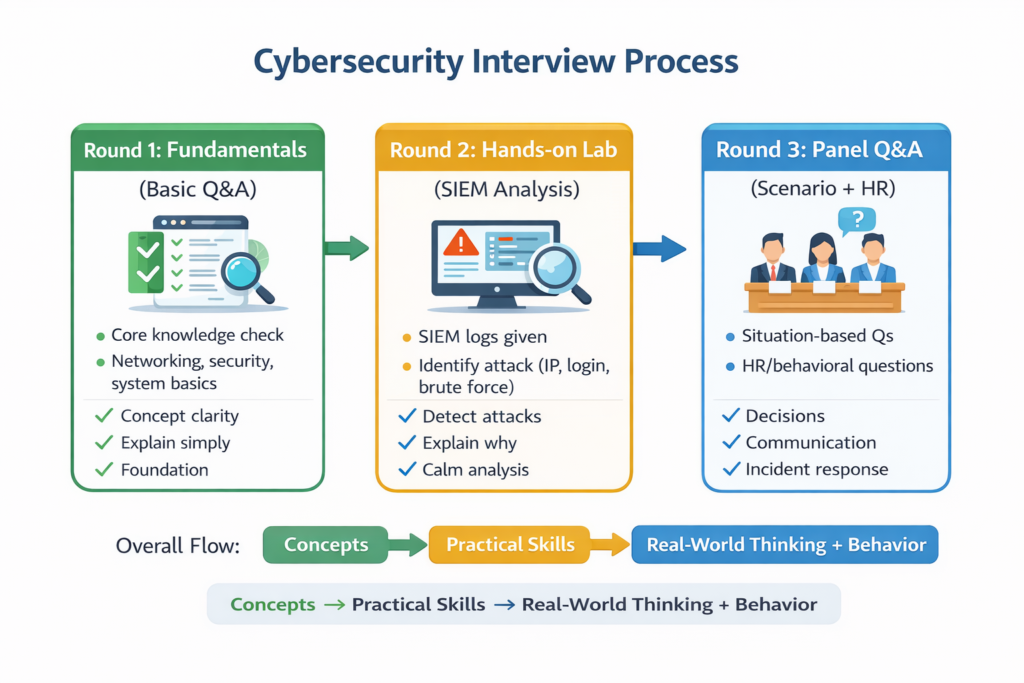
At CuriosityTech.in, our mock interview sessions simulate exactly these layers:
- Round 1: Fundamentals (basic Q&A).
- Round 2: Hands-on lab (student asked to detect an attack in SIEM logs).
- Round 3: Panel Q&A (scenario-based + HR).
We even replicate board-level CISSP interviews where students explain cyber risk to non-technical stakeholders — a unique skill that makes our learners stand out in Nagpur and globally.
Address: 1st Floor, Plot No 81, Wardha Rd, Gajanan Nagar, Nagpur.
Call: +91-9860555369 | ✉️ contact@curiositytech.in | 🌐curiosity tech Follow us on Instagram @curiositytechpark | LinkedIn & Facebook: Curiosity Tech
Conclusion
Cybersecurity interviews in 2025 are no longer about rote memorization. They test:
- Knowledge (definitions, frameworks)
- Skills (labs, detection, response)
- Mindset (calm under pressure, growth attitude)
By preparing across all these dimensions — and practicing in hands-on labs like those at Curiosity Tech — you not only answer questions correctly but also prove that you can defend an organization in real life.
Remember: A great candidate is not the one who knows every answer, but the one who demonstrates structured thinking and problem-solving in uncertain situations.