Introduction:
When enterprises adopt cloud computing, the first excitement often revolves around scalability, flexibility, and cost savings. But as an engineer with two decades of experience, I’ve seen firsthand that without strong identity and access management (IAM), even the most advanced cloud architectures crumble under security risks. This is especially true in multi-cloud environments where you’re juggling AWS, Azure, and Google Cloud Platform (GCP).
At CuriosityTech.in, we’ve mentored engineers who start their cloud journey overwhelmed by IAM terminologies—users, groups, roles, policies, RBAC, service accounts—but once they master these, the path toward secure multi-cloud deployments becomes clearer. And that’s exactly what we’ll explore today.
Why IAM Matters in Multi-Cloud
IAM is the bridge between people, processes, and cloud resources. Imagine your cloud infrastructure as a massive skyscraper: IAM defines who can enter, which floors they can access, and what they can do inside. Without IAM, the skyscraper doors would be wide open.
Key reasons IAM is critical:
- Protects sensitive workloads and customer data.
- Ensures compliance with regulations (GDPR, HIPAA, ISO 27001).
- Avoids shadow IT and unauthorized resource usage.
- Simplifies user management across different teams and services.
AWS IAM: The Pioneer
AWS IAM (Identity & Access Management) was one of the earliest cloud-native IAM services.
Core AWS IAM Concepts:
- Users: Individual accounts with credentials.
- Groups: Logical collections of users for permission management.
- Roles: Temporary permissions for services or cross-account access.
- Policies: JSON-based definitions of allowed/denied actions.
Best Practices (AWS):
- Always apply Least Privilege Principle—no more, no less.
- Use IAM Roles instead of long-lived access keys for apps.
- Rotate access keys regularly.
- Apply MFA (Multi-Factor Authentication).
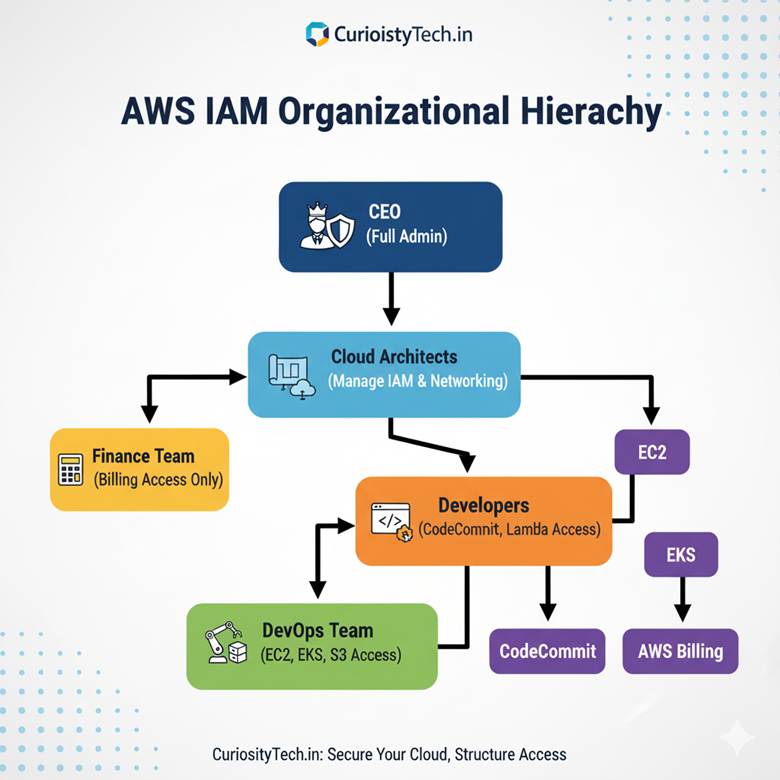
Example AWS IAM Hierarchy:
This hierarchy avoids giving “root-like” powers to everyone, reducing security risk.
Azure IAM: The Enterprise Integrator
Azure takes IAM a step further by extending its Active Directory (AD) heritage into the cloud.
Core Azure IAM Concepts:
- Azure AD: Cloud-based identity service.
- RBAC (Role-Based Access Control): Assigns permissions at subscription, resource group, or resource levels.
- Conditional Access: Enforces contextual policies (location, device, risk).
- Managed Identities: Secure way for apps to connect without credentials.
Best Practices (Azure):
- Leverage Conditional Access for risky sign-ins.
- Use Privileged Identity Management (PIM) to give time-bound elevated access.
- Integrate Azure AD with on-prem AD for hybrid identity.
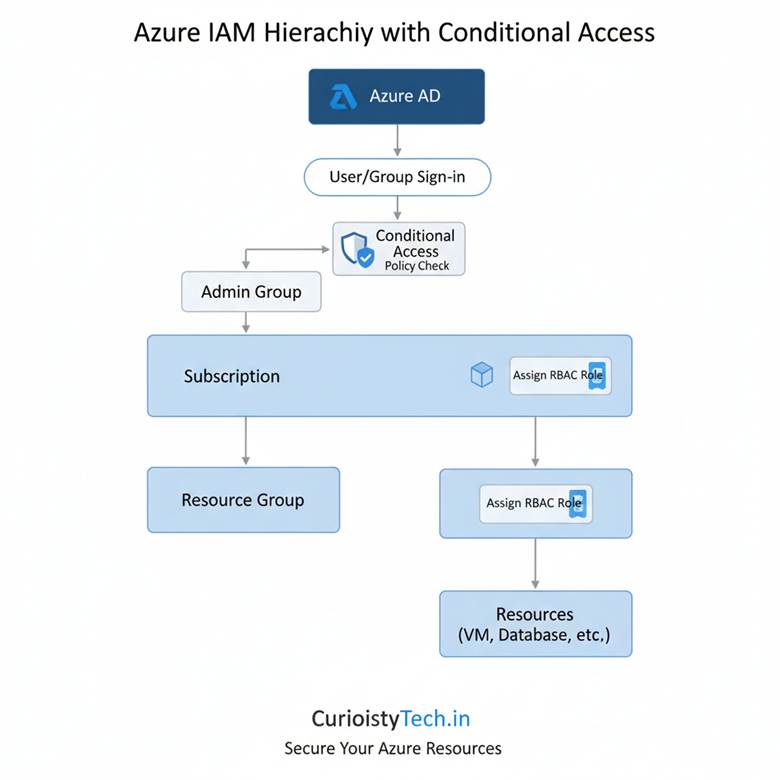
AWS IAM Hierarchy:
Azure’s IAM strength lies in enterprise contexts—think banks, governments, healthcare providers—where integration with existing directories and compliance is critical.
GCP IAM: The Precision Tool
Google Cloud IAM is often praised for fine-grained access control.
Core GCP IAM Concepts:
- Members: Users, groups, service accounts.
- Roles: Predefined, basic, or custom roles.
- Policies: Bindings between members and roles.
- Service Accounts: Identities for apps, VMs, and workloads.
Best Practices (GCP):
- Assign roles at project/folder level instead of organization-wide.
- Use service accounts for workloads, not personal accounts.
- Monitor IAM changes with Cloud Audit Logs.
GCP IAM Hierarchy:
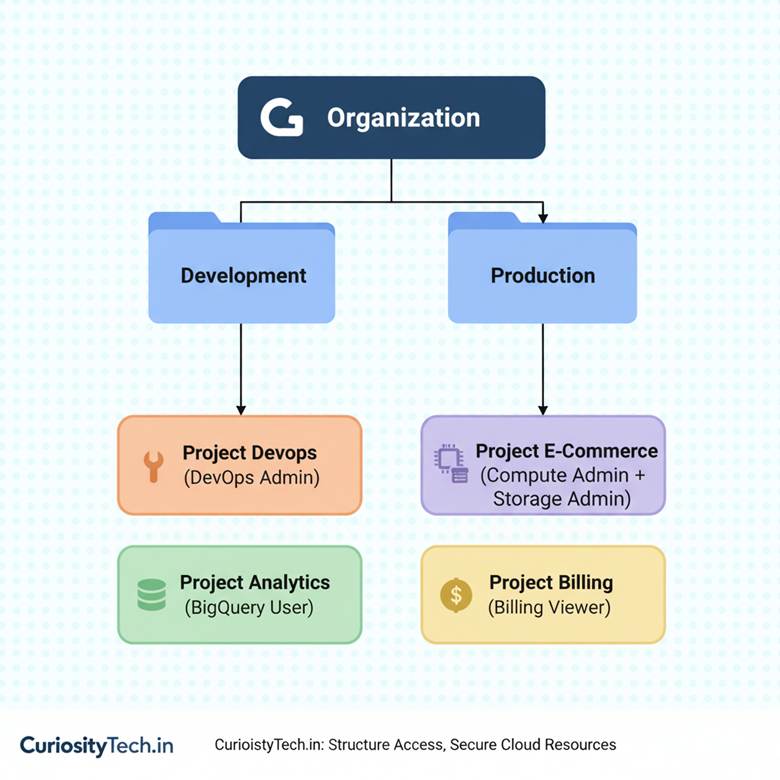
This clarity helps avoid “role creep,” where users accumulate unnecessary permissions over time.
IAM Comparison Across Clouds
| Feature | AWS IAM | Azure IAM (AD + RBAC) | GCP IAM |
| Identity Source | IAM Users | Azure AD Users/Groups | Google Accounts/Groups |
| Access Model | Policies + Roles | RBAC + Conditional Access | Roles + Policies |
| Temporary Access | IAM Roles | Managed Identities | Service Accounts |
| MFA Support | Yes | Yes | Yes |
| Granularity | Resource-level | Resource + Conditional | Resource-level (precise) |
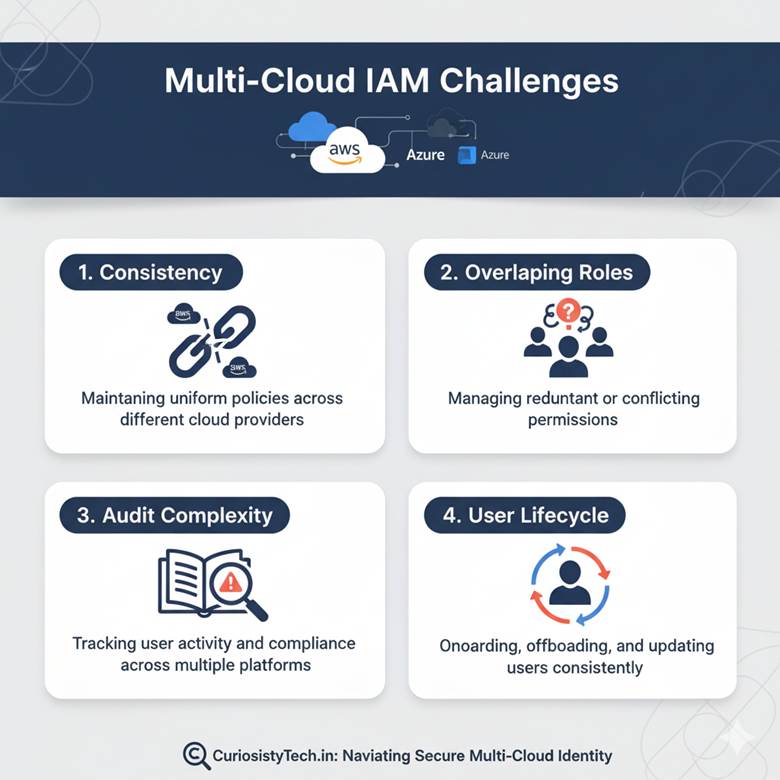
IAM Challenges in Multi-Cloud
- Consistency: Different clouds have different IAM models.
- Overlapping Roles: Risk of giving duplicate or excessive access.
- Audit Complexity: Logs and monitoring spread across providers.
- User Lifecycle: Offboarding users securely across clouds.
That’s why multi-cloud IAM governance tools (like Okta, Ping Identity, or HashiCorp Vault) are becoming popular.
Infographic Idea (Described)
How You Become an IAM Expert
To truly master IAM across clouds:
- Hands-On Labs: Don’t just read—practice creating users, roles, and conditional policies.
- Certifications: AWS Security Specialty, Azure Security Engineer, GCP Security Engineer.
- Real Projects: Deploy a multi-cloud app with IAM as the backbone.
- Continuous Learning: IAM evolves—stay updated with new features like AWS IAM Identity Center or Azure’s Entra ID.
At CuriosityTech.in, we emphasize labs and guided projects. Our learners don’t just pass exams—they deploy IAM in live multi-cloud labs, troubleshoot misconfigurations, and learn to balance security with usability.
Conclusion
IAM isn’t just another chapter in cloud computing—it’s the foundation of secure multi-cloud success. From AWS policies to Azure RBAC to GCP service accounts, every platform provides unique tools. But the real mastery lies in understanding their differences, aligning them to organizational needs, and implementing governance consistently.
For learners and enterprises alike, platforms like CuriosityTech.in provide the perfect ecosystem to go from basic IAM awareness to enterprise-grade expertise. When your IAM is strong, your cloud future is secure.


