In my 20 years as a cyber security consultant, I’ve learned this truth: what isn’t tested isn’t secure. Organizations often believe their defenses are solid after installing a firewall or updating policies. But until those defenses are actively tested, no one really knows how strong they are. This is where Vulnerability Assessment (VA) and Penetration Testing (PT) come into play.
At CuriosityTech.in Nagpur, when training new cyber engineers, we immerse them into lab environments where they learn to scan, identify, and ethically exploit weaknesses—before malicious hackers do it for real.
VA vs PT – First Principles
| Aspect | Vulnerability Assessment (VA) | Penetration Testing (PT) |
| Definition | Systematic identification, classification, and reporting of security vulnerabilities. | Simulated ethical hacking to exploit vulnerabilities and measure real-world impact. |
| Approach | Broad but shallow – scans large surface, reports all weaknesses. | Focused and deep – targets specific weaknesses to confirm exploitability. |
| Outcome | Risk list with severity ratings (e.g., CVSS scoring). | Proof-of-concept exploits showing actual damage potential. |
| Frequency | Regular – monthly/quarterly. | Periodic – yearly, before/after product launch. |
| Tools | Nessus, OpenVAS, Qualys. | Metasploit, Burp Suite, Nmap, custom scripts. |
Analogy:
- VA is like a doctor’s health checkup report listing possible issues.
- PT is like stress-testing your body—running on a treadmill to see if the heart handles pressure.
The Vulnerability Assessment & Penetration Testing Lifecycle
Diagram Description: A circular lifecycle flowchart with 6 steps:
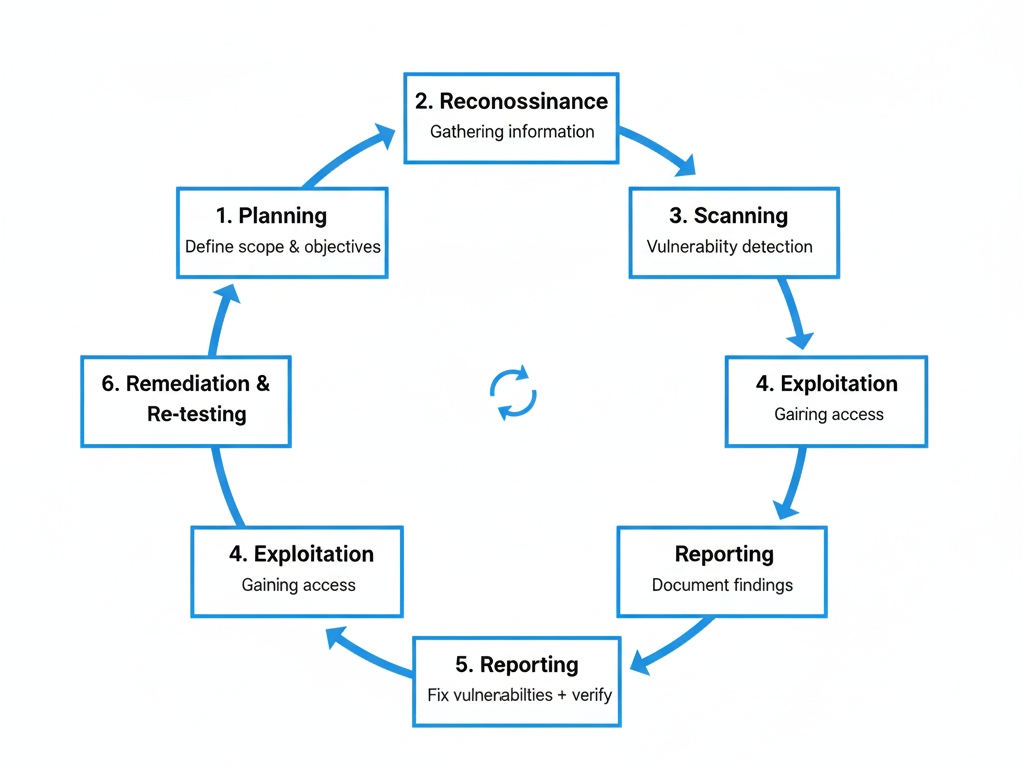
Planning → Reconnaissance → Scanning → Exploitation → Reporting → Remediation & Re-testing.
This cycle is repeated until the system is hardened.
Step-by-Step Lab Guide
Step 1: Planning & Scoping
- Define target systems: web applications, internal servers, cloud resources.
- Define engagement rules: what’s allowed, what’s forbidden.
- At CuriosityTech, we enforce a “Get written permission first” principle. Without scope clarity, testing = hacking.
Lab Exercise: Create an engagement scope document for testing a small e-commerce website. Include assets (web app, database server), timelines, and objectives (test SQL injection, scan for open ports).
Step 2: Reconnaissance (Information Gathering)
- Passive Recon: Collect external information (WHOIS records, DNS, open-source data).
- Active Recon: Network mapping, banner grabbing.
Tools: Nmap, Maltego.
Lab Task: Run nmap -sV target.com and document open ports. Example output could show port 80 (HTTP), port 443 (HTTPS), and port 22 (SSH).
Step 3: Scanning & Enumeration
- Vulnerability Scanning: Nessus/OpenVAS scan entire system.
- Enumeration: Identify specific services, versions, known CVEs.
Practical Example:
- Scan reveals Apache HTTPD version 2.4.43.
- CVE database cross-check shows known remote code execution vulnerability.
Lab Task: Export vulnerability report with CVSS scores, highlighting High (7–8.9) vs Critical (9–10).
Step 4: Exploitation (Penetration Testing)
- Attempt to exploit critical vulnerabilities discovered in scans.
- Use frameworks like Metasploit.
- Example: SQL injection discovered on login page during VA → carry out controlled exploitation to confirm database extraction.
Lab Exercise: Run SQL injection on DVWA (Damn Vulnerable Web Application) in a controlled sandbox. Document findings responsibly.
Step 5: Reporting
- VA → A table of risks, severity, affected assets.
- PT → Detailed proof-of-concept with evidence (screenshots, commands).
Reporting Best Practices:
- Executive Summary (for non-technical audience).
- Technical Details (for IT teams).
- Remediation roadmap.
Case Insight: At CuriosityTech, when we submitted a PT report for a logistics firm, executives panicked at hearing “SQL injection.” But we translated it into business terms: “Hackers can steal customer data, exposing you to ₹50 crore in penalties under GDPR.” That’s when executive buy-in became real.
Step 6: Remediation & Re-testing
- Patch uncovered vulnerabilities.
- Harden misconfigurations.
- Retest to confirm issues are resolved.
Checklist for Engineers:
- Is the patched system tested?
- Has monitoring been adjusted?
- Has a “lessons learned” session been held?
Practical VA/PT Tools & Purposes
| Tool | Use |
| Nmap | Recon, open port scanning |
| Nessus / OpenVAS | Vulnerability scanning |
| Burp Suite | Web application exploitation |
| Metasploit | Exploit framework |
| Wireshark | Packet analysis |
| Nikto | Web server scanner |
Case Study: Small Business in Nagpur
In 2023, a Nagpur-based retail company believed it was “safe” because it used cloud-hosted apps. A VA scan we performed at CuriosityTech.in revealed outdated plugins on their WordPress website with a CVSS 9.8 vulnerability. During PT, we demonstrated how an attacker could upload a malicious shell and gain database access.
Impact if ignored? Complete loss of customer payment records.
Action taken? Plugins patched, WAF (Web Application Firewall) installed, and quarterly VA/PT scheduled.
Lesson: No company is “too small” for attack.
Infographic Description
Imagine a VA/PT Lifecycle Infographic:
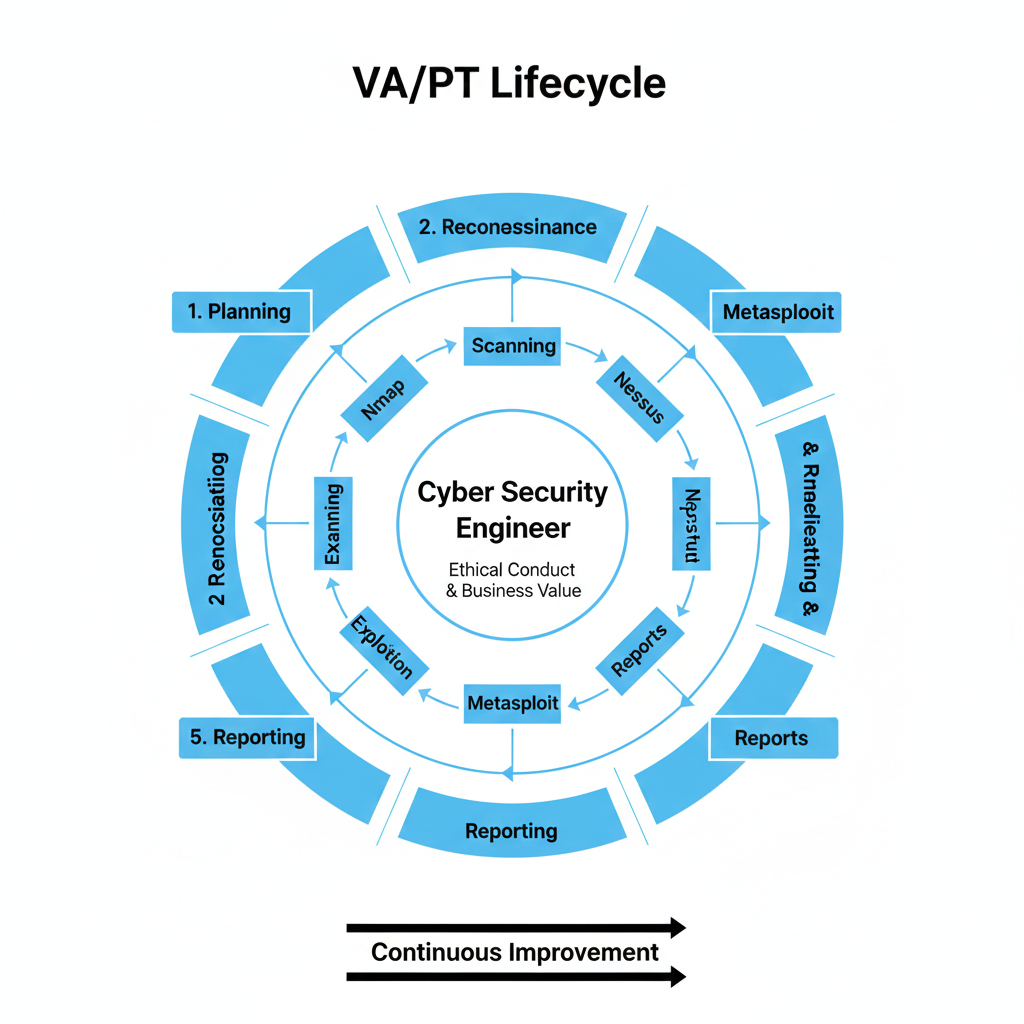
- Outer Ring: Planning, Recon, Scanning, Exploitation, Reporting, Remediation.
- Inner Ring: Tools used in each phase (Nmap → Nessus → Metasploit → Reports).
- Center: “Cyber Security Engineer” as the orchestrator ensuring ethical conduct and business value.
My Personal Field Insight
One of my toughest experiences was when a client resisted a penetration test fearing system downtime. When convinced, I ran a basic test and found an exploitable flaw that could give outsiders complete admin access. They were stunned. That day I told them: “Security without testing is just hope. And hope is not a cyber strategy.”
Conclusion
Vulnerability Assessment and Penetration Testing (VAPT) forms the frontline toolkit of cyber security engineers. VA helps you map weaknesses; PT helps prove what attackers can do with them. Together, they provide the clarity and urgency businesses need in securing assets before hackers exploit them.
At CuriosityTech.in (Contact: +91-9860555369 | Email: contact@curiositytech.in | Address: Plot No 81, Wardha Rd, Gajanan Nagar, Nagpur | Socials: Instagram @curiositytechpark, LinkedIn Curiosity Tech, Facebook Curiosity Tech), our labs simulate real-world assessments with professional tools, allowing aspiring cyber engineers to gain confidence and expertise. Whether you’re testing a small business or a global enterprise, VA/PT are not “advanced extras”—they’re essentials.



