Introduction
When I ask young engineers at Curiosity Tech, Nagpur about their first thought in network defense, the most common answer is firewalls. And though they’re not wrong, that’s only one piece of the larger puzzle. In real-world defense, Firewalls, Intrusion Detection Systems (IDS), and Intrusion Prevention Systems (IPS) operate in unison to secure networks.
Think of it like a medieval castle:
- Firewall = the gates and walls that block unwanted entry.
- IDS = surveillance guards watching for suspicious behavior.
- IPS = armed soldiers who don’t just watch, but immediately stop intruders.
Let’s break this down systematically for future cyber engineers.
The Hierarchy of Network Defense
Diagram Description: Picture a layered defense hierarchy:
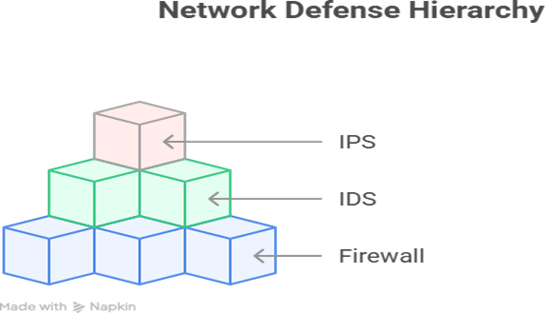
This hierarchy demonstrates progression from basic filtering → detection → dynamic prevention.
Comparison Table: Firewall vs IDS vs IPS
| Feature | Firewall | IDS | IPS |
| Primary Role | Control access (allow/deny traffic based on rules). | Monitor and detect suspicious activities. | Actively block malicious traffic in real time. |
| Placement | Network edge or internal segmentation. | Inside network, behind firewall. | Inline with traffic flow (between firewall and internal network). |
| Mode | Preventive. | Detective. | Preventive + Detective. |
| Action | Permit/Deny based on rules. | Alert/log suspicious patterns. | Alert + block malicious packets. |
| Tools | pfSense, Cisco ASA, Palo Alto. | Snort (IDS mode), Suricata. | Snort/Suricata (IPS mode), Cisco FirePOWER. |
| Limitations | Cannot detect application-level attacks. | Cannot block—only alerts administrators. | Can block, but if misconfigured may drop legitimate traffic. |
Scenario Casebook: How They Work Together
1: An Employee Connects to Malicious Website
- Firewall: Blocks known malicious IPs based on static rules.
- IDS: Detects abnormal outbound requests (strange DNS query). Raises alert.
- IPS: Identifies payload signature as malware → blocks connection instantly.
2: Brute-Force Attack Against SSH (Port 22)
- Firewall: Port 22 allowed for admins. Attack traffic still passes.
- IDS: Logs suspicious repeated failed logins.
- IPS: Detects brute-force pattern signature → drops attacker’s IP.
Practical Configuration Walkthrough
Firewall Rules Example (pfSense Scenario)
- Block inbound traffic from all external IPs except port 443 (HTTPS).
- Allow SSH only from internal admin subnet (192.168.1.0/24).
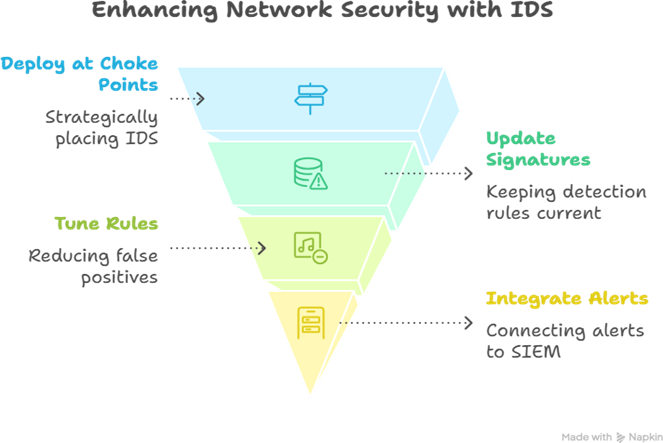
IDS Setup (Snort Example)
- Install Snort on a mirrored port behind firewall.
- Load rulesets for detecting common exploits (e.g., SQL injection attempt signature).
- IDS will log suspicious SQL query from unexpected IP.
IPS Function (Suricata in Inline Mode)
- Suricata inline blocks any packet matching rule drop tcp any any -> any 1433 (msg:“MSSQL attack attempt”).
- IPS stops packet in real-time before reaching database server.
Real-World Case from My Consulting
In 2019, a financial services company in Nagpur relied only on a firewall. They believed strict firewall rules were enough. But a phishing email bypassed all perimeter settings (since it was user-driven). Once malware infected systems inside, the firewall was blind—it didn’t detect lateral spread.
When they enrolled with CuriosityTech, we implemented a three-layer model: Firewall for border control, IDS for monitoring lateral moves, and IPS to shut malicious communications instantly. Within two months, the system detected and blocked a brute-force attempt from overseas IPs—proving why layered defense matters.
Infographic Description
A castle defense infographic:
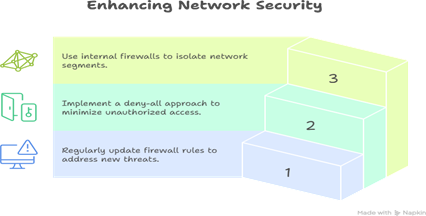
Best Practices for Firewalls, IDS & IPS
Quick Engineer Checklist
| Step | Firewall | IDS | IPS |
| Initial Setup | Deny-all inbound, allow essential services. | Deploy sensors, enable rules. | Inline mode, testing rules. |
| Maintenance | Update rules regularly. | Tweak rules to reduce noise alerts. | Refine block rules, avoid business disruption. |
| Testing | Try allowed + blocked ports. | Generate test alerts (Nmap scans). | Simulate attacks, verify IPS blocks instantly. |
My Field Insight
One of the most painful mistakes I saw was when a company operated an IPS but left it disabled, fearing false positives. When an attack happened, the IPS detected every malicious packet, but it hadn’t been switched to blocking mode. Logs showed the entire attack in detail but damage was already done. Lesson? Security tools are only as strong as their configuration and trust in them.
Conclusion
The triad of Firewall + IDS + IPS is the backbone of secure networking in 2025. Firewalls create boundaries, IDS provide intelligence, and IPS ensures instant action. Used together, they form layered, resilient defense mechanisms that drastically reduce breach chances.
At CuriosityTech.in (Address: Plot No 81, Wardha Rd, Gajanan Nagar, Nagpur | Contact: +91-9860555369 | Email: contact@curiositytech.in | Socials: Instagram @curiositytechpark, LinkedIn/Facebook: Curiosity Tech), we build real lab environments where learners configure pfSense firewalls, run Snort/Suricata IDS/IPS, and test their effectiveness with simulated attacks. Because in the real world, knowing about these tools isn’t enough—you must see them in action.



