Introduction
Authentication and authorization are critical for securing modern web applications. Authentication verifies the user’s identity, while authorization determines what resources the user can access.
In FullStack .NET development, securing your ASP.NET Core applications with Identity, JWT tokens, and role-based access is essential. CuriosityTech.in provides hands-on guidance to implement these security measures in real-world projects, ensuring learners build secure, professional-grade applications.
1. Understanding Authentication vs Authorization
| Concept | Description | Example |
| Authentication | Verifying who the user is | Logging in with username and password |
| Authorization | Determining what the user can do | Admin can delete courses, students can only view |
Flow Diagram:
[User] —> [Login Page] —> [Authentication Service] —> [Token/Session]
[Authorization Check] —> Access Resource
2. Setting Up ASP.NET Core Identity
- Install Identity packages:
Install-Package Microsoft.AspNetCore.Identity.EntityFrameworkCore
- Configure Identity in Program.cs:
builder.Services.AddDbContext<ApplicationDbContext>(options =>
options.UseSqlServer(connectionString));
builder.Services.AddIdentity<IdentityUser, IdentityRole>()
.AddEntityFrameworkStores<ApplicationDbContext>()
.AddDefaultTokenProviders();
- Update Startup.cs or Program.cs for middleware:
app.UseAuthentication();
app.UseAuthorization();
3. Creating User Roles
Roles define what users can do:
var roleManager = serviceProvider.GetRequiredService<RoleManager<IdentityRole>>();
if(!await roleManager.RoleExistsAsync(“Admin”))
{
await roleManager.CreateAsync(new IdentityRole(“Admin”));
}
if(!await roleManager.RoleExistsAsync(“Student”))
{
await roleManager.CreateAsync(new IdentityRole(“Student”));
}
4. Registering and Logging In Users
Register User:
var user = new IdentityUser { UserName = model.Email, Email = model.Email };
var result = await _userManager.CreateAsync(user, model.Password);
Login User:
var result = await _signInManager.PasswordSignInAsync(model.Email, model.Password, false, false);
5. Role-Based Authorization
Controllers can restrict access:
[Authorize(Roles = “Admin”)]
public IActionResult ManageCourses()
{
return View();
}
[Authorize(Roles = “Student”)]
public IActionResult ViewCourses()
{
return View();
}
Explanation:
- Only Admins can access course management.
- Students can view available courses but cannot modify data.
6. Using JWT for API Authentication
For Web API scenarios, use JWT tokens:
Generating JWT Token:
var tokenHandler = new JwtSecurityTokenHandler();
var key = Encoding.ASCII.GetBytes(“YourSecretKey”);
var tokenDescriptor = new SecurityTokenDescriptor
{
Subject = new ClaimsIdentity(new Claim[]
{
new Claim(ClaimTypes.Name, user.Id.ToString())
}),
Expires = DateTime.UtcNow.AddHours(1),
SigningCredentials = new SigningCredentials(new SymmetricSecurityKey(key), SecurityAlgorithms.HmacSha256Signature)
};
var token = tokenHandler.CreateToken(tokenDescriptor);
var tokenString = tokenHandler.WriteToken(token);
Protecting API endpoints:
[Authorize]
[HttpGet(“GetCourses”)]
public IActionResult GetCourses()
{
return Ok(_context.Courses.ToList());
}
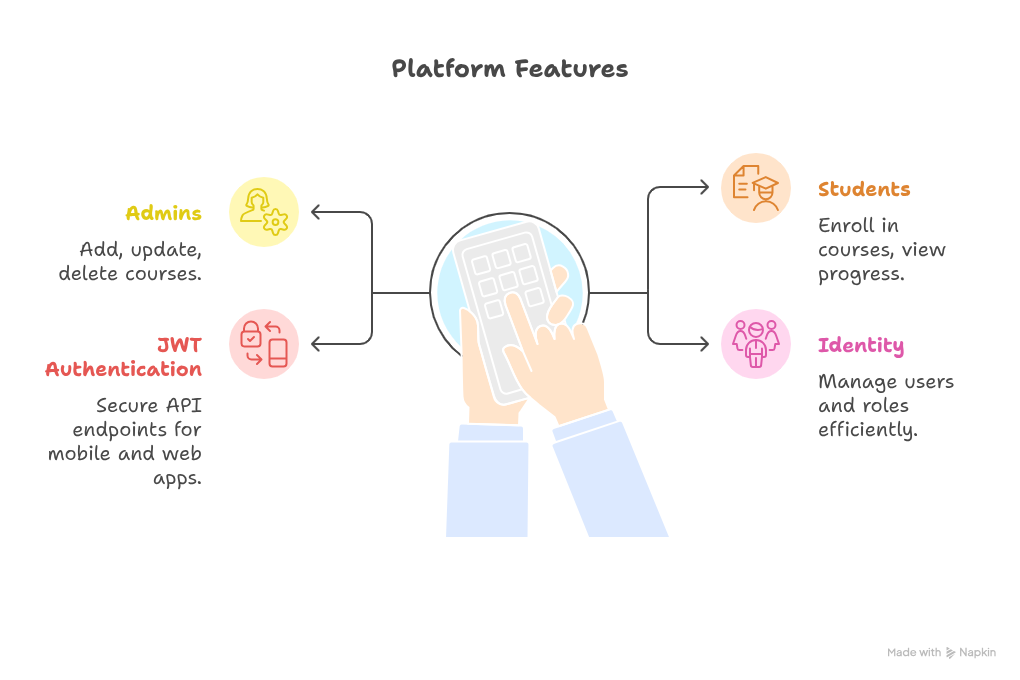
7. Real-World Project: CuriosityTech Learning Platform
- Admins: Add, update, delete courses
- Students: Enroll in courses, view progress
- JWT Authentication: Secure API endpoints for mobile and web apps
- Identity: Manage users and roles efficiently
Project Flow Diagram:
[User Login] –> [Identity Service] –> [JWT Token Issued] –> [API Access]
|
V
[Role-based Authorization]
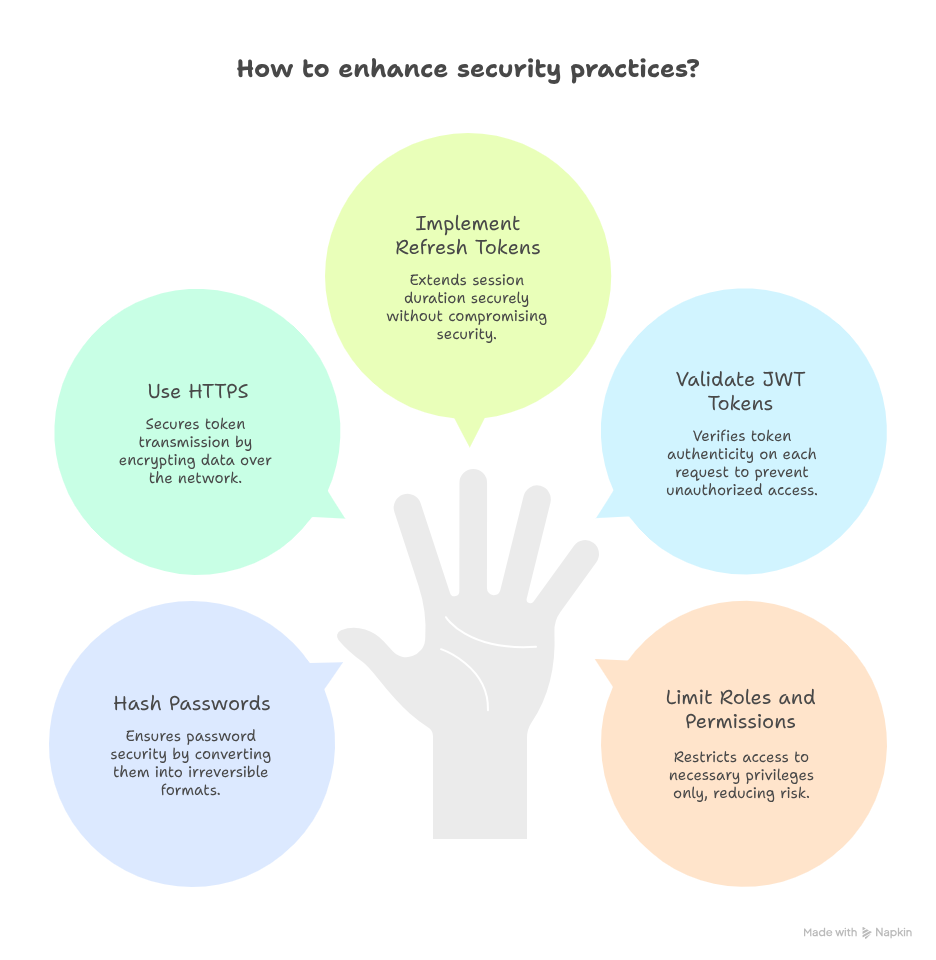
8. Best Practices
- Always hash passwords (Identity handles this automatically)
- Use HTTPS for secure token transmission
- Implement refresh tokens for prolonged sessions
- Validate JWT tokens on every request
- Limit roles and permissions to principle of least privilege
9. CuriosityTech.in Mentorship Insights
- Step-by-step guidance on implementing Identity and JWT
- Hands-on projects like secure course portals and dashboards
- Prepares learners for industry-standard security practices
Conclusion
Authentication and authorization are the backbone of secure applications. By leveraging ASP.NET Core Identity and JWT tokens, FullStack developers can ensure that users only access authorized resources. With CuriosityTech.in’s practical mentorship, learners gain the skills and confidence to build professional, secure web applications.
The next step is Day 13 – Frontend Integration: Using React or Angular with .NET Backend, where we’ll connect frontend applications to your secure backend.