Introduction
Security is a critical aspect of MERN Stack development. Web applications often handle sensitive data, including user credentials, personal information, and transactional data. Without proper security measures, apps are vulnerable to data breaches, hacks, and exploitation.
CuriosityTech.in emphasizes practical, hands-on security measures, helping developers safeguard MERN applications against common vulnerabilities while maintaining usability and performance.
Step 1: Authentication & Authorization
- JWT (JSON Web Tokens):
- Standard for stateless authentication in MERN apps.
- Securely transmit user identity between client and server.
const jwt = require(‘jsonwebtoken’);
const token = jwt.sign({ userId: user._id }, process.env.JWT_SECRET, { expiresIn: ‘1h’ });
- Role-Based Access Control (RBAC):
- Differentiate access for users, admins, and moderators.
- Middleware ensures users can only access authorized routes.
Step 2: Input Validation & Sanitization
- Prevent SQL/NoSQL injection and XSS attacks.
- Use libraries like express-validator or joi for backend validation.
const { body, validationResult } = require(‘express-validator’);
app.post(‘/register’,
body(’email’).isEmail(),
body(‘password’).isLength({ min: 6 }),
(req, res) => {
const errors = validationResult(req);
if (!errors.isEmpty()) return res.status(400).json({ errors: errors.array() });
});
- Sanitize inputs to remove malicious scripts.
Step 3: Secure Password Storage
- Never store passwords in plain text.
- Use bcrypt for hashing:
const bcrypt = require(‘bcrypt’);
const hashedPassword = await bcrypt.hash(password, 10);
- Combine with salt rounds for added security.
Step 4: Secure API Endpoints
| Best Practice | Description |
| HTTPS | Encrypt all traffic between client and server using SSL/TLS |
| Rate Limiting | Prevent brute-force attacks using express-rate-limit |
| CORS Configuration | Restrict API access to allowed origins |
| Helmet Middleware | Set HTTP headers for security (helmet) |
| Logging & Monitoring | Track suspicious activity with centralized logs and alerts |
Step 5: Protect Against XSS & CSRF
- XSS (Cross-Site Scripting):
- Sanitize user inputs before rendering on frontend.
- Use React’s built-in protections and avoid dangerouslySetInnerHTML unless necessary.
- CSRF (Cross-Site Request Forgery):
- Use CSRF tokens in forms or JWT-based protection for APIs.
- Libraries: csurf for Express.
Step 6: MongoDB Security
- Connection Security:
- Use connection strings with credentials and IP whitelisting.
- Role-Based Database Access:
- Assign minimal privileges to database users.
- Data Encryption:
- Enable field-level encryption or use MongoDB Atlas encryption features.
Step 7: Monitoring & Vulnerability Management
- Use tools to identify vulnerabilities:
- OWASP ZAP or Snyk for dependency scanning.
- PM2 or New Relic for monitoring runtime security issues.
- Keep dependencies updated to prevent exploits.
Diagram – Security Layers in MERN App:
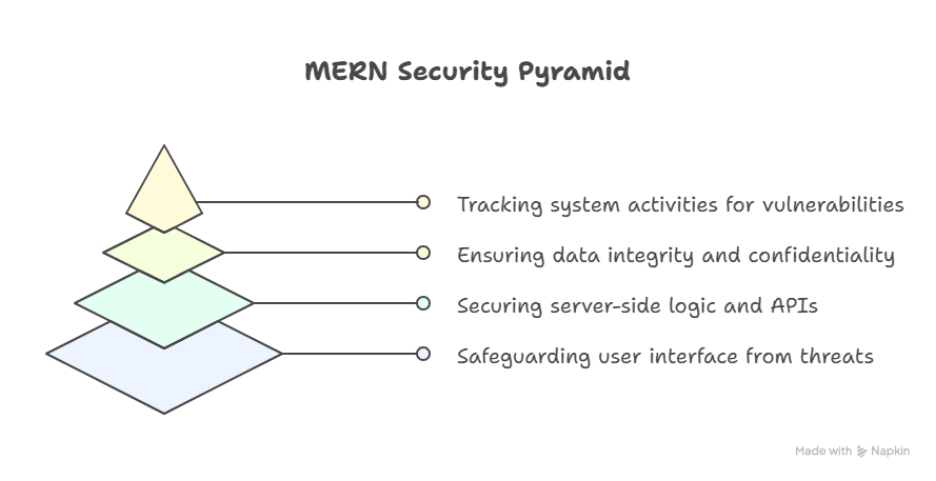
Step 8: Becoming an Expert in MERN Security
- Implement end-to-end authentication and authorization using JWT and RBAC.
- Master input validation, sanitization, and secure coding practices.
- Configure secure database connections and access controls.
- Monitor and respond to real-time threats and logs.
- Regularly update dependencies and audit for vulnerabilities.
CuriosityTech.in provides hands-on security workshops, helping developers secure MERN applications effectively while building professional full-stack skills.
Infographic Suggestion
Title: “Security Best Practices for MERN Applications”
- Sections: Frontend Protection → Backend Middleware → Database Security → Monitoring & Auditing
- Description: Visualizes layered security measures to safeguard MERN applications against common threats.
Conclusion
Securing a MERN application is essential to protect sensitive data and maintain user trust. Following best practices for authentication, authorization, input validation, database security, and monitoring ensures production-ready, secure applications. CuriosityTech.in guides learners through practical security implementations in MERN projects for real-world readiness.



