Introduction
Security is a non-negotiable aspect of cloud computing. Azure provides a comprehensive set of tools and best practices to secure applications, data, and infrastructure. Cloud engineers must master identity management, network security, data protection, and compliance to ensure enterprise-grade security.
At curiositytech.in, learners are trained with real-world threat modeling scenarios and hands-on labs, preparing them to implement robust security strategies on Azure.
1. Understanding Azure Security Fundamentals
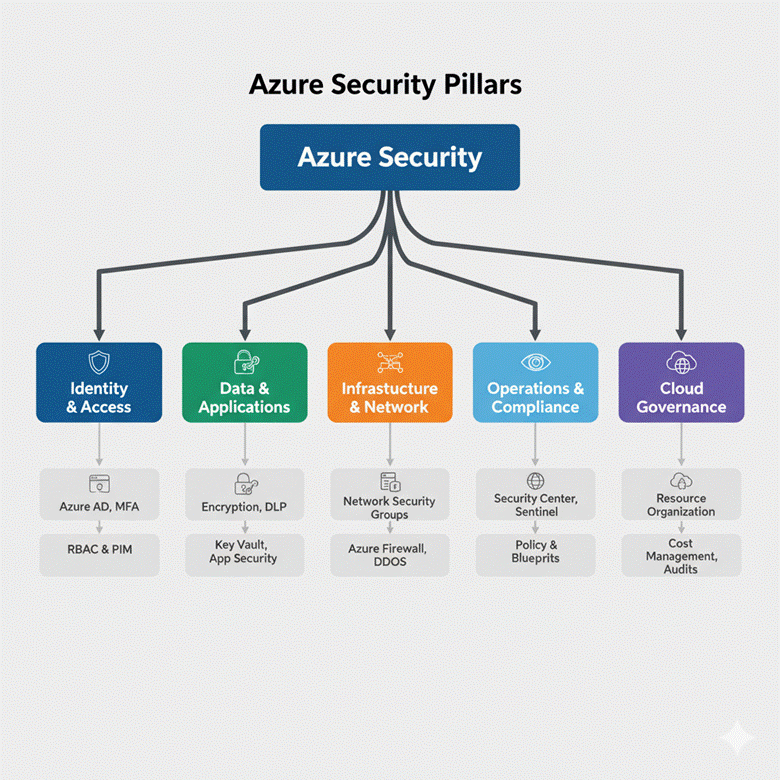
Azure Security Pillars:
- Identity & Access Management (IAM): Control who can access resources
- Network Security: Protect network boundaries and data in transit
- Data Protection: Encrypt sensitive information and manage keys
- Threat Protection: Detect, investigate, and respond to threats
- Compliance & Governance: Ensure regulatory requirements are met
Diagram: Azure Security Pillars
2. Identity & Access Management Best Practices
- Use Azure AD & RBAC: Assign least privilege roles
- Enable Multi-Factor Authentication (MFA): Protect against compromised credentials
- Privileged Identity Management (PIM): Time-bound elevated access
- Conditional Access Policies: Enforce location, device, and risk-based access
Scenario:
A financial enterprise implements MFA and PIM for its DevOps team. Access to production resources is allowed only during working hours and after approval, reducing risk of unauthorized changes.
3. Network Security Best Practices
- Virtual Networks (VNets): Isolate resources
- Network Security Groups (NSGs): Control inbound and outbound traffic
- Azure Firewall: Centralized traffic filtering
- Web Application Firewall (WAF): Protect web apps against SQL injection, XSS, and DDoS
- DDoS Protection: Use Basic or Standard plan to mitigate attacks
Scenario Example:
A company deploys a public web application. Using NSGs, WAF, and DDoS Standard, they block malicious traffic, inspect HTTP requests, and maintain uptime during volumetric attacks.
4. Data Protection Best Practices
- Encryption at Rest: Enable Transparent Data Encryption (TDE) for databases
- Encryption in Transit: Use TLS 1.2 or above for communication
- Key Vault: Store secrets, certificates, and keys securely
- Backup & Disaster Recovery: Regular automated backups with geo-redundancy
Scenario:
An e-commerce platform stores payment details. Using Azure Key Vault and TDE, sensitive data is encrypted at rest and in transit. Backups are configured to ensure quick recovery in case of failure.
5. Threat Protection Best Practices
- Azure Security Center: Provides continuous security assessment and recommendations
- Microsoft Defender for Cloud: Detects vulnerabilities and threats
- Logging & Monitoring: Use Azure Monitor and Log Analytics for real-time alerts
- Incident Response: Define runbooks to automate responses to common threats
Scenario Example:
An alert from Azure Security Center detects malicious login attempts. Automated runbooks temporarily disable the affected account and notify security engineers.
6. Compliance & Governance Best Practices
- Policies & Blueprints: Apply Azure Policy to enforce standards
- Resource Tagging: Track ownership and compliance
- Audit Logs: Maintain activity and security logs for regulatory compliance
- Continuous Compliance: Use Compliance Manager to monitor standards (ISO, GDPR, HIPAA)
Scenario:
A healthcare organization uses Azure Blueprints and Policy to ensure that all storage accounts are encrypted and only approved regions are used, ensuring HIPAA compliance.
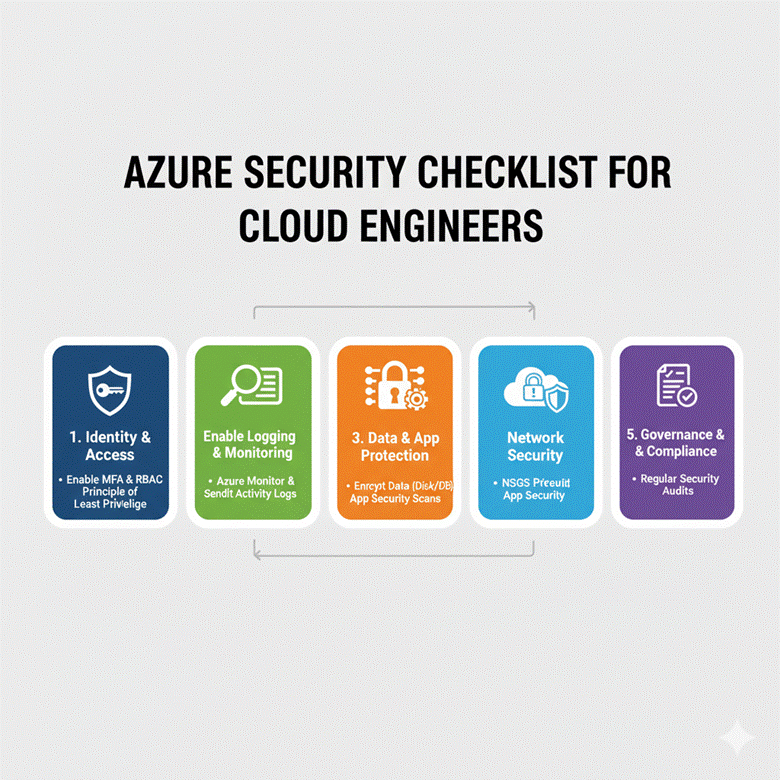
7. Security Checklist for Cloud Engineers
| Area | Best Practices |
| Identity & Access | RBAC, MFA, PIM, Conditional Access |
| Network Security | VNets, NSGs, Azure Firewall, WAF, DDoS Protection |
| Data Protection | TDE, TLS, Key Vault, Backup & Geo-Redundancy |
| Threat Protection | Security Center, Microsoft Defender, Monitoring |
| Compliance & Governance | Azure Policies, Blueprints, Audit Logs |
infographic Content :
8. Hands-On Implementation Example
- Enable MFA & Conditional Access for all users in Azure AD
- Deploy Azure Firewall in the hub VNet
- Configure NSGs for production subnets
- Encrypt SQL Database using TDE
- Enable Azure Security Center and configure alerts
- Set up Log Analytics Workspace for threat monitoring
Scenario:
A SaaS startup follows this checklist to ensure end-to-end security, protecting customer data, monitoring threats, and complying with GDPR regulations.
9.Infographic Content:
Conclusion
Security in Azure is multi-layered, covering identity, network, data, threat protection, and compliance. By adopting best practices, threat modeling, and continuous monitoring, cloud engineers can ensure enterprise-grade security. Hands-on labs at curiositytech.in help learners apply theoretical concepts in practical environments, building real-world expertise in cloud security.