Introduction
Security is the foundation of any robust cloud deployment. In Google Cloud Platform (GCP), engineers must implement end-to-end security across infrastructure, applications, and data. Misconfigurations or overlooked vulnerabilities can lead to costly breaches, downtime, or compliance violations.
Google Cloud Security encompasses identity management, data protection, network security, threat detection, and compliance. At Curiosity Tech, we emphasize a security-first mindset for engineers, combining practical strategies, GCP-native tools, and best practices to build secure, enterprise-grade applications.
Core Principles of GCP Security
1. Identity & Access Management (IAM)
- Control who can access what using roles, policies, and service accounts.
- Enforce least privilege access and use groups for efficient management.
2. Data Protection
- Encrypt data at rest and in transit.
- Use Customer-Managed Encryption Keys (CMEK) for sensitive data.
- Secure databases with IAM and network policies.
3. Network Security
- Use Virtual Private Cloud (VPC) with subnets, firewall rules, and private IPs.
- Implement VPC Service Controls to protect sensitive data from exfiltration.
4. Threat Detection & Logging
- Enable Cloud Logging and Cloud Monitoring.
- Use Cloud Security Command Center (SCC) to detect misconfigurations and vulnerabilities.
5. Compliance & Governance
- Maintain audit trails using Cloud Audit Logs.
- Follow regulatory standards (ISO, SOC, GDPR) using GCP compliance tools.
Key GCP Security Tools
| Tool / Service | Purpose |
|---|---|
| Cloud IAM | Manage access and roles for users, groups, and service accounts. |
| VPC Firewall Rules | Control network access to resources. |
| Cloud KMS | Key management for encryption. |
| Cloud Security Command Center | Centralized view of vulnerabilities and compliance status. |
| Cloud Armor | Protect applications from DDoS and web attacks. |
| Binary Authorization | Enforce trusted images for deployment. |
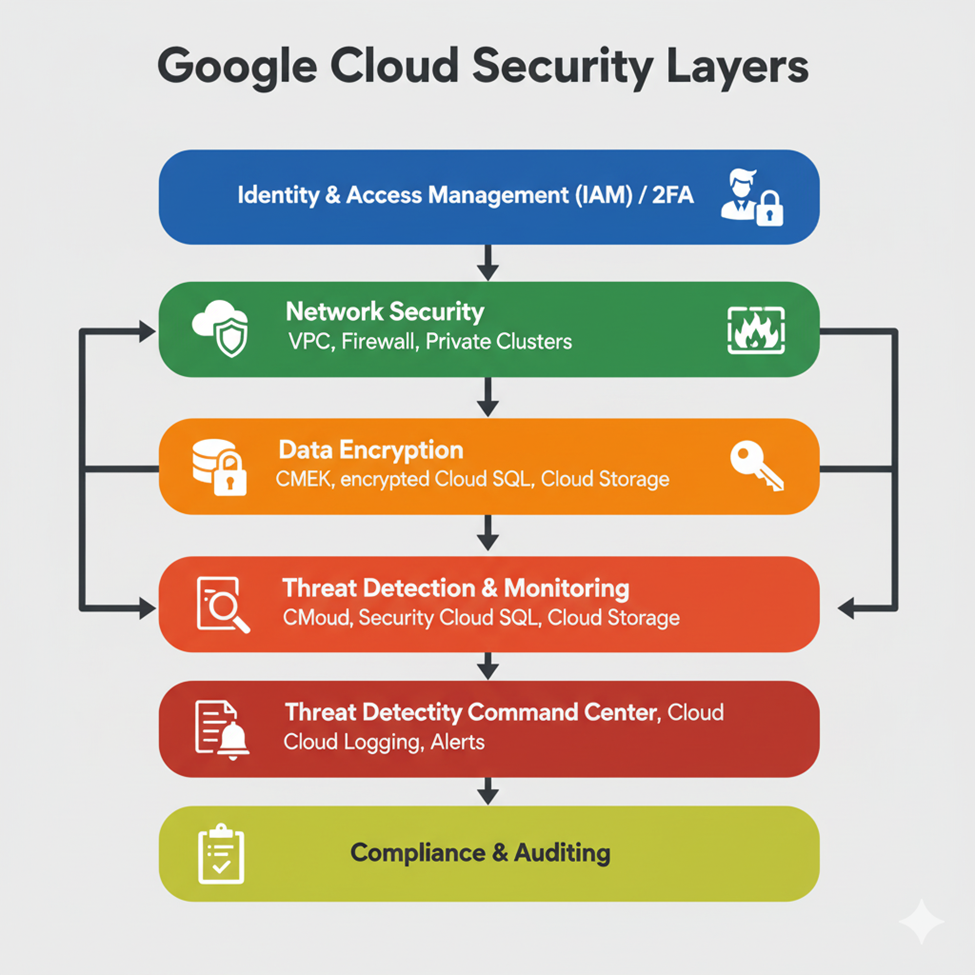
Diagram Concept: GCP Security Layers
[Identity & Access] → [Network Security] → [Data Encryption] → [Threat Detection & Monitoring] → [Compliance & Auditing]
Identity & Access Management Best Practices
- Use Service Accounts: Assign to workloads instead of human users.
- Enable Two-Factor Authentication (2FA): For all users in Google Workspace.
- Implement IAM Conditions: Restrict access based on time, IP, or device.
- Audit IAM Policies Regularly: Remove unnecessary permissions.
- Use Groups Instead of Individual Users: Simplifies permission management.
Data Security Best Practices
| Practice | Description & Benefits |
|---|---|
| Encryption at Rest | All GCP data is encrypted by default; use CMEK for additional control. |
| Encryption in Transit | Use TLS for all communications between services and endpoints. |
| Data Masking & Tokenization | Mask sensitive PII in databases for compliance and privacy. |
| Cloud DLP (Data Loss Prevention) | Scan, classify, and protect sensitive data automatically. |
| Backup & Disaster Recovery | Regular snapshots and replication for availability. |
Network Security Best Practices
- Use Private IPs: Avoid exposing resources publicly unless necessary.
- Firewall Rules: Restrict inbound/outbound traffic by IP, protocol, and port.
- VPC Service Controls: Define security perimeters to prevent data exfiltration.
- VPN & Cloud Interconnect: Secure hybrid or multi-cloud connections.
- Segmentation: Separate workloads into different VPCs or subnets for isolation.
Threat Detection & Monitoring
- Cloud Security Command Center (SCC): Centralized security dashboard.
- Event Threat Detection: Identify suspicious activity like brute-force attacks or privilege escalation.
- Cloud Logging & Monitoring: Real-time visibility and alerting on anomalous behavior.
Practical Scenario: Detect unauthorized access to a sensitive database:
- Enable Cloud Audit Logs for Cloud SQL.
- Create log-based alerts for failed login attempts.
- Respond with Cloud Functions that automatically revoke compromised credentials.
Advanced Security Practices
- Binary Authorization: Ensure only trusted container images are deployed on GKE.
- Security Health Analytics: Automatically monitor compliance of resources.
- Zero Trust Architecture: Combine Identity-Aware Proxy (IAP), VPC Service Controls, and IAM to enforce strict access policies.
- Regular Penetration Testing: Simulate attacks to discover weaknesses.
- Automated Patching: Keep OS and software components updated using managed services.
Practical Case Study: Securing a Multi-Service GCP Application
Scenario: An online fintech platform with GKE, Cloud SQL, and Cloud Storage.
- Identity: Service accounts for microservices; 2FA for all human users.
- Network: Private clusters, VPC firewall rules, and segmentation per service.
- Data: Encryption using CMEK, backups, and DLP scans for PII.
- Monitoring: SCC and log-based alerts for unusual access patterns.
- Deployment: Binary Authorization ensures only trusted container images are deployed.
Diagram Concept: End-to-End GCP Security Architecture

[Users / Applications] → [IAM / 2FA] → [VPC / Firewall / Private Cluster] → [Encrypted Data in Cloud SQL / Storage] → [SCC Monitoring / Alerts]
Conclusion
Mastering Google Cloud Security is critical for any cloud engineer. By implementing IAM best practices, data encryption, network security, monitoring, and compliance controls, engineers can ensure applications are secure, resilient, and compliant.
At Curiosity Tech, engineers gain hands-on labs and real-world projects focused on securing multi-service cloud architectures, preparing them to handle enterprise security challenges confidently.



