Abstract (Whitepaper Style)
The global cybersecurity landscape in 2025 has transformed dramatically compared to even two years ago. As AI-driven threats grow sharper, cloud environments expand, and regulatory frameworks tighten, security engineers must evolve.
This research-driven blog explores 10 key cyber security trends of 2025, supported with expert commentary, hierarchical diagrams, forecast tables, and real-world insights from CuriosityTech.in, a leading cyber training hub in Nagpur.
Introduction
In my 20 years of cyber defense and ethical hacking experience, one lesson has stayed true: threat actors innovate faster than defenses unless engineers adapt.
When students walk into our Curiosity Tech Park training labs at Gajanan Nagar, Nagpur, I often ask them:
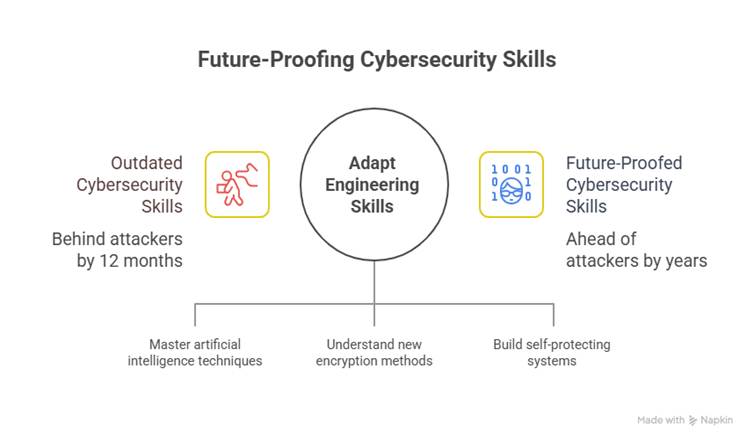
“If your knowledge is from last year’s playbook, are you already behind the attacker by 12 months?”
2025 demands engineers to future-proof skills — AI, post-quantum cryptography, autonomous defense systems, and beyond. Let’s break down the most critical trends shaping cybersecurity in 2025.
Top Emerging Cyber Security Trends in 2025
1. AI-Powered Cyber Attacks
- What’s happening: Hackers are now using Generative AI to craft polymorphic malware and deepfake phishing campaigns.
- Impact: Security perimeters are harder to defend because every phishing email looks legitimate.
- Response: Adoption of AI-driven SOCs (Security Operations Centers) for anomaly detection.
- CuriosityTech Angle: In our Nagpur labs, students simulate AI-based phishing using open-source GPT clones, then learn defensive AI scripting to counter it.
2. Zero Trust Becomes the Default Architecture
- Legacy castle-and-moat models are dead.
- By 2025, Zero Trust Network Access (ZTNA) has become mandatory in enterprises.
- Hierarchical Diagram (described):
- Outer Layer: Device Verification
Middle Layer: Identity Authentication
- Core Layer: Continuous Trust Evaluation
- Outer Layer: Device Verification
- Engineers must master tools like Zscaler, Palo Alto Prisma, Azure AD Conditional Access.
3. Post-Quantum Cryptography (PQC)
- Quantum computing poses a threat to RSA/ECC encryption.
- NIST PQC Algorithms like CRYSTALS-Kyber are now being deployed in early adoption stages.
- Forecast Table:
| Year | Status of PQC | Adoption Level |
| 2023 | Research Phase | <5% |
| 2024 | Standardization Started | 20% |
| 2025 | Enterprise Pilots | 45% |
| 2030 | Global Standard | 80% |
At CuriosityTech workshops, students learn how current TLS fails against quantum computing and experiment with PQC libraries.
4. Security Automation & SOAR Expansion
- Manual incident handling is obsolete.
- SOAR (Security Orchestration, Automation, Response) platforms are scaling.
- Example: Automated script closes vulnerable ports detected via Nmap + triggers patch deployment.
5. Cloud-Native Security & CNAPPs
- Enterprises now adopt Cloud-Native Application Protection Platforms (CNAPP).
- By 2025, hybrid and multi-cloud environments dominate, forcing engineers to master AWS Security Hub, GCP Security Command Center, Azure Defender.
6. Rise of Cyber Insurance & Compliance-Driven Security
- More than 70% of Fortune 500 companies in 2025 rely on cyber insurance.
- Engineers must understand compliance frameworks: GDPR updates, India’s Digital Data Protection Act, HIPAA 2025 revisions.
7. Biometric & Continuous Authentication
- Passwords are fading away.
- 2025 sees widespread adoption of behavioral biometrics (typing rhythm, gait recognition).
- At CuriosityTech labs, students explore how adversarial AI can spoof biometrics, and how multi-layer defenses stop it.
8. Supply Chain Cybersecurity
- SolarWinds-type attacks showed how fragile ecosystems are.
- Engineers must monitor software dependencies, container registries, and third-party integrations.
- Tools: SCA (Software Composition Analysis) and SBOM (Software Bill of Materials).
9. Autonomous Cyber Defense with AI Agents
- Just like attackers automate, defenders now deploy autonomous response systems.
- Example: An AI agent detects lateral movement and isolates compromised hosts without waiting for human SOC approval.
10. Cybersecurity Talent Shift
- Demand for multi-disciplinary engineers who blend coding + AI + security is rising.
- Certifications are evolving: CompTIA Security+ (2025 update includes AI security modules), CISSP quantum-safe cryptography domains.
- Students at CuriosityTech are mentored to choose the right path early — ethical hacker, SOC analyst, cloud security engineer, or compliance officer.
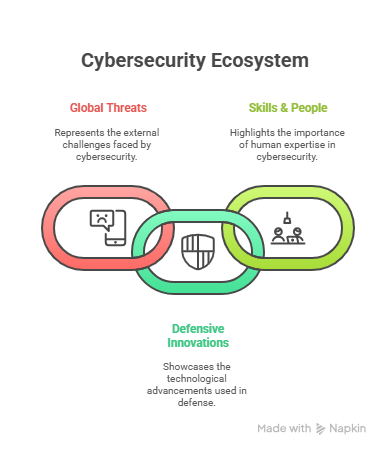
Infographic Description: 2025 Security Ecosystem
Imagine a layered circle infographic:
- Outer Ring → Global Threats (AI Malware, PQC Risk, Supply Chain Attacks).
- Middle Ring → Defensive Innovations (SOAR, ZTNA, CNAPPs).
- Inner Ring → Skills & People (Talent evolution, Certifications, Continuous Training).
This visual reminds us: cybersecurity is a living ecosystem.
Expert Commentary (Humanized)
When a young learner asked me at CuriosityTech, “Sir, do we even stand a chance against AI attackers?”, I replied:
“Yes, because attackers may innovate, but defenders collaborate.”
That’s why institutions like CuriosityTech.in exist — to bridge skill gaps. With a dedicated facility in Nagpur, reachable at +91-9860555369 or contact@curiositytech.in, we help engineers not just chase trends but stay ahead of them.
Conclusion
2025 is not the year of incremental security — it’s the year of paradigm shifts. From post-quantum algorithms to autonomous cyber defense, the world has entered a phase where only adaptive, research-driven engineers will thrive.
Whether you’re a beginner or a seasoned SOC analyst, embrace continuous learning. Tomorrow’s cybersecurity wars won’t be fought with yesterday’s skills.

