Introduction
In Full Stack development, security is not optional—it is essential. Python developers often focus on functionality and performance, but neglecting security can lead to data breaches, financial loss, and reputational damage.
At CuriosityTech, we teach that building secure Python web applications is a professional responsibility. In this blog, we’ll explore practical security best practices, from input validation to authentication, data protection, and deployment-level security measures.
Common Security Risks
| Risk | Description | Mitigation Strategy |
| SQL Injection | Malicious input manipulates database queries | Use ORM (Django ORM, SQLAlchemy), parameterized queries |
| Cross-Site Scripting (XSS) | Attackers inject malicious scripts into web pages | Sanitize user input, use Django autoescape, React JSX |
| Cross-Site Request Forgery (CSRF) | Unauthorized commands sent from authenticated users | CSRF tokens, Django/Flask built-in protection |
| Insecure Authentication | Weak passwords or token leakage | Use strong hashing (bcrypt), JWT, OAuth2 |
| Data Exposure | Sensitive data in plaintext | HTTPS, encryption at rest (AES), secure environment vars |
| Insecure Dependencies | Vulnerabilities in third-party packages | Regularly update packages, use pip-audit |
Backend Security Best Practices
1. Use Secure Authentication
Django Example:
# settings.py
PASSWORD_HASHERS = [‘django.contrib.auth.hashers.Argon2PasswordHasher’ ‘django.contrib.auth.hashers.PBKDF2PasswordHasher’,]
# Use Django’s built-in authentication system from django.contrib.auth.models import User
user = User.objects.create_user(username=’bhavesh’, password=’SecurePass123!’)
- Strong password hashing prevents attackers from easily cracking user passwords.
Flask Example:
from werkzeug.security import generate_password_hash, check_password_hash
hashed_password = generate_password_hash(“SecurePass123!”, method=”pbkdf2:sha256″, salt_length=16)
check_password_hash(hashed_password, “SecurePass123!”) # Returns True
2. Input Validation & Sanitization
- Validate all user inputs at server-side.
- Prevent XSS attacks by escaping HTML content.
Django Example: Autoescape in templates
{{ user_input }} <!– Autoescaped –>
Flask Example: Using bleach library
import bleach
safe_content = bleach.clean(user_input)
3. CSRF Protection
- Django: Enabled by default with CSRF middleware.
<form method=”post”>
{% csrf_token %}
<input type=”text” name=”comment”>
</form>
- Flask: Use Flask-WTF for forms with CSRF protection.
from flask_wtf import FlaskForm
from wtforms import StringField
class CommentForm(FlaskForm):
comment = StringField(‘Comment’)
4. HTTPS & Secure Headers
- Always use HTTPS for production apps to encrypt data in transit.
- Add security headers.
| Header | Purpose |
| Strict-Transport-Security | Forces HTTPS connections |
| X-Content-Type-Options | Prevents MIME type sniffing |
| Content-Security-Policy | Restricts resources to trusted sources |
Django Example:
SECURE_HSTS_SECONDS = 3600
SECURE_CONTENT_TYPE_NOSNIFF = True
SECURE_BROWSER_XSS_FILTER = True
5. Protect Sensitive Data
- Store secrets in environment variables.
- Encrypt sensitive database fields.
Example: Environment Variables
export SECRET_KEY=”super_secure_key”
export DATABASE_PASSWORD=”StrongPass123!”
- Never commit secrets to version control.
Frontend Security Best Practices
- Escape all dynamic content to prevent XSS.
- Validate forms client-side but always re-validate server-side.
- Use JWT securely: Store tokens in HTTP-only cookies, not localStorage.
- Limit API rate to prevent brute-force attacks.
Security Monitoring & Tools
| Tool/Library | Purpose |
| bandit | Static code analysis for Python security issues |
| pip-audit | Checks vulnerabilities in Python packages |
| sentry | Monitors errors and potential security breaches |
| OWASP ZAP | Web application penetration testing |
Infographic Idea – “Python Web Security Layers”
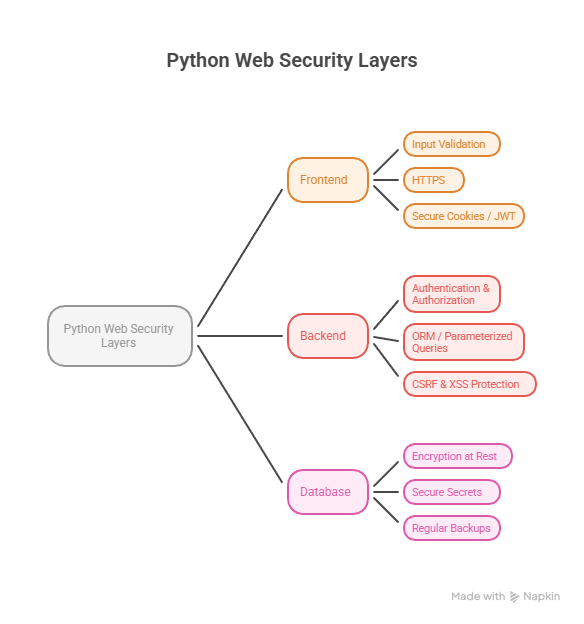
- Visualizing security layers helps developers understand holistic security.
Real-World CuriosityTech Example
- Students at CuriosityTech built a Python Full Stack e-commerce app:-
- Implemented Argon2 password hashing and JWT authentication
- Used HTTPS and secure headers for production
- Outcome: The application passed security audits, demonstrating real-world secure Python development practices.
Best Practices Checklist
Security is the foundation of professional Python Full Stack development. Following best practices ensures your applications are robust, trustworthy, and production-ready.
At CuriosityTech, students learn to integrate security into every layer—from frontend forms, backend logic, to deployment—preparing them for real-world challenges in web application security.



