When people ask me: “What’s the heart of cyber security?” my answer has always been the same—Networking. Without an in-depth understanding of networks, no cyber security engineer can defend systems effectively. Every firewall rule, intrusion detection alert, VPN tunnel, or attack vector is tied to networks.
At CuriosityTech.in, Nagpur, I often see students rushing into cybersecurity tools like Kali Linux or penetration testing labs without learning networking. The result? They can run scans, but they cannot interpret what’s happening under the hood. That’s why, in this tutorial-style guide, I’ll mentor you through the networking skills that form the backbone of cyber security—layer by layer.
Why Networking is Critical for Cyber Security
- Attacks travel over networks: Malware, phishing, ransomware—these threats enter through network communication.
- Every defense is network-linked: Firewalls, IDS, VPNs, proxies all sit on the network pathway.
- Detection depends on traffic flows: Logs, SIEM alerts, anomaly detection rely on analyzing network packets.
- Loud adoption increases networking complexity: AWS VPCs, Azure VNets, multi-cloud hybrid environments introduce new challenges.
A cyber security engineer who doesn’t understand IP packets is like a doctor who doesn’t know anatomy.
Networking Basics Every Cyber Security Engineer Must Learn
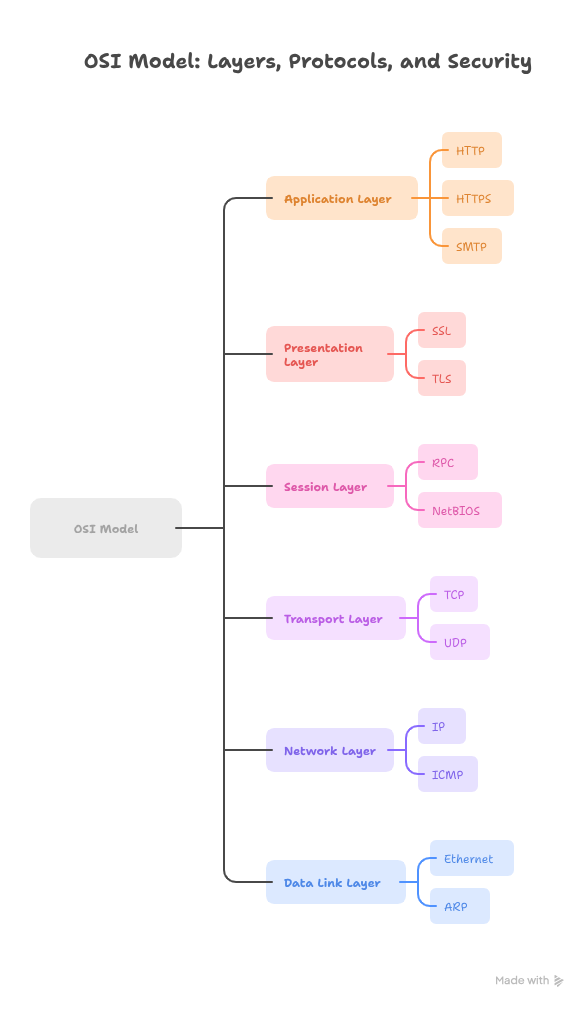
1. OSI & TCP/IP Models
The OSI (Open System Interconnection) model is the conceptual framework engineers use to understand how data flows in layers.
| OSI Layer | Example Protocols | Security Perspective |
| Application | HTTP, HTTPS, SMTP | Attacks like XSS, CSRF |
| Presentation | SSL/TLS | Encryption/Decryption |
| Session | RPC, NetBIOS | Session hijacking |
| Transport | TCP, UDP | DoS attacks, port scanning |
| Network | IP, ICMP | IP spoofing, routing attacks |
| Data Link | Ethernet, ARP | ARP spoofing |
| Physical | Cables, Wi-Fi | Signal jamming |
Packet Flow Walk through Example:
- You type www.curiositytech.in into your browser.
- The request travels down OSI layers, transforms into bits, moves through switches/routers, reaches the server IP, and travels back to your device.
- Hackers often exploit weaknesses at specific layers (e.g., DoS attacks at Transport layer, DNS poisoning at Application layer).
2. IP Addressing & Subnets
- IPv4: 32-bit address (e.g., 192.168.1.1).
- IPv6: 128-bit address (e.g., 2001:0db8:85a3::8a2e:0370:7334).
- Subnetting: Divides a larger network into smaller, manageable parts.
Exercise (Hands-On at CuriosityTech Labs):
- Create a network with 2 subnets:
- 192.168.1.0/24 for laptops.
- 192.168.2.0/24 for servers.
- Observe how pinging across the subnet requires routing. This is where firewalls could block or allow cross-traffic.
3. Ports and Protocols
Security engineers must memorize critical ports used by attackers.
| Port | Protocol | Vulnerability Example |
| 21 | FTP | Anonymous login abuse |
| 22 | SSH | Brute-force SSH attacks |
| 25 | SMTP | Email spoofing/phishing |
| 53 | DNS | DNS poisoning |
| 80 | HTTP | Clear-text traffic, injection attacks |
| 443 | HTTPS | SSL/TLS vulnerabilities |
| 3389 | RDP | Remote Desktop brute force |
Hackers often use port scanning (Nmap) to find open doors. Engineers must know which doors should remain closed.
4. Routers, Switches & Firewalls
- Router: Directs traffic between networks. Attack surface: routing table poisoning.
- Switch: Connects devices in a local network. Attack surface: MAC flooding.
- Firewall: Filters traffic based on rules. Without correct rules, attackers can bypass defenses.
Tutorial Action:
- Set up a home lab with pfSense firewall.
- Block inbound traffic from port 21 while allowing port 443.
- Use Wireshark to verify packet rejection.
5. VPNs & Tunneling
Engineers must secure remote connections.
- VPN (Virtual Private Network) encrypts traffic through secure tunnels.
- Attackers target misconfigured VPNs to steal data.
At CuriosityTech workshops, we simulate VPN attacks to demonstrate why multi-factor authentication (MFA) + VPN is stronger than VPN alone.
Practical Walkthrough: How an Attack Exploits Networking
Scenario: A phishing email leads an employee to click a malicious link.
- Their computer sends an outbound request over HTTP (Port 80).
- Router passes the packet, firewall allows outbound HTTP.
- Malicious server responds, sending back malware payload.
- Infection spreads within LAN as malware scans for open ports on subnet 192.168.1.0/24.
This step-by-step packet journey reveals the role of networking at each stage and where defenders can intervene.
Networking Security Tools for Engineers
| Tool | Purpose |
| Wireshark | Packet capture and analysis |
| Nmap | Port scanning, enumeration |
| Netcat | Simple client/server testing |
| tcpdump | CLI packet capture |
| Cisco Packet Tracer | Learning network simulation |
Infographic Description:
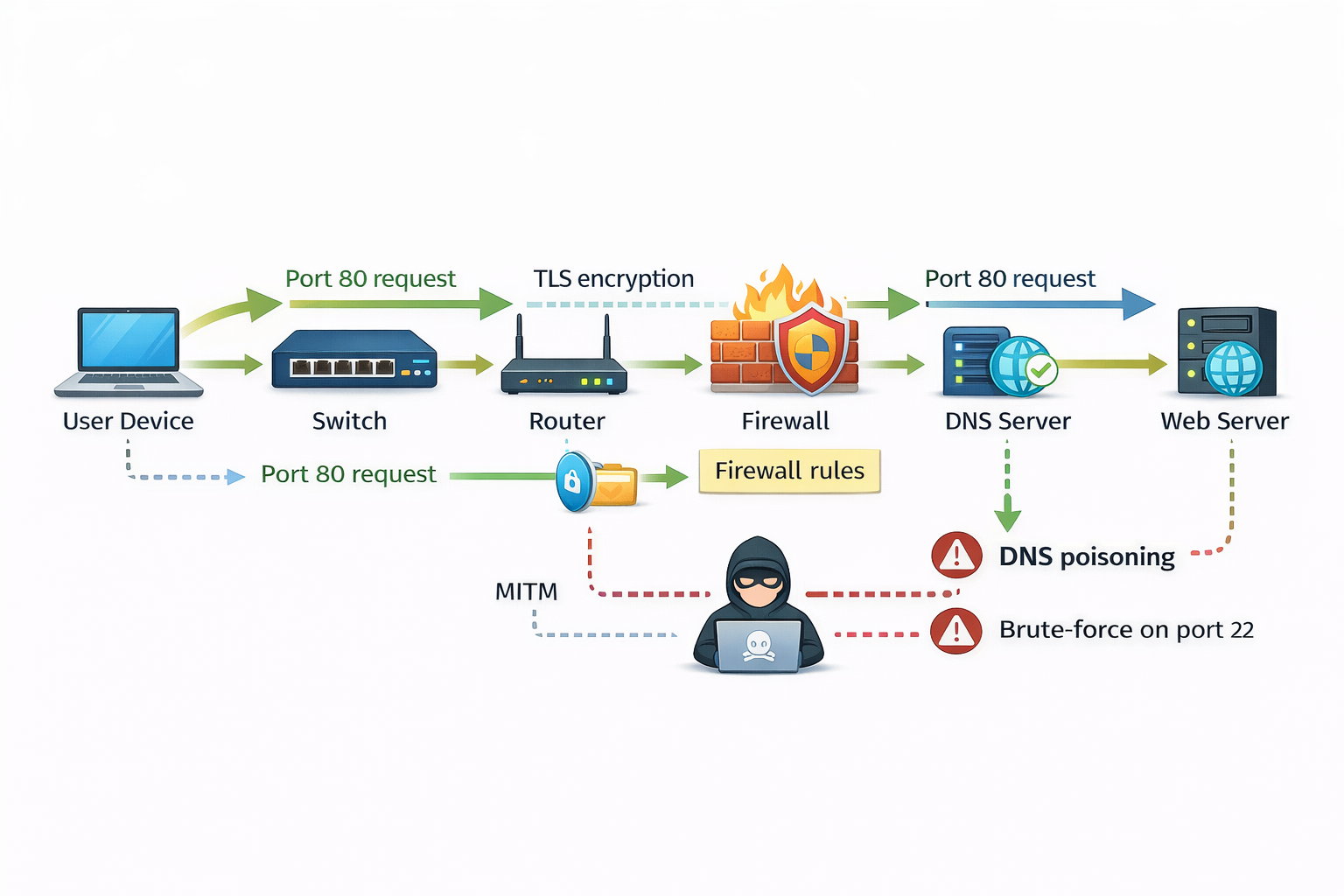
A small packet starts from “User Device” → passes “Switch” → “Router” → “Firewall” → “DNS Server” → “Web Server”.
The infographic uses arrows and labels like “Port 80 request,” “TLS encryption,” and “Firewall rules.” Alongside, small notations show where hackers typically attack (DNS poisoning, MITM, brute-force on port 22).
My Career Insight
In my early years, I once misdiagnosed a persistent DDoS issue as a server vulnerability. Later, deep packet inspection revealed the problem was actually at the Transport Layer—a flood of SYN packets exhausting resources. That experience taught me the weight of networking in cyber defense: if you skip fundamentals, you misinterpret threats.
Conclusion
Networking is not just a technical requirement—it’s the language of cyber security. Every engineer must become fluent in protocols, ports, flows, and defense mechanisms. Once you can visualize packet journeys like a map, you can defend organizations against attacks more effectively.
At CuriosityTech.in (Address: Plot No 81, Wardha Rd, Gajanan Nagar, Nagpur | Call: +91-9860555369 | Email: contact@curiositytech.in | Instagram: curiositytechpark | LinkedIn: Curiosity Tech | Facebook: Curiosity Tech), our programs emphasize networking labs as the foundation before diving into advanced topics like penetration testing or cloud security. Because if you understand the roads, you can secure the city.



