Introduction
In Google Cloud Platform (GCP), security is not an afterthought—it is a core pillar of cloud architecture. At the heart of GCP security lies Identity and Access Management (IAM), which defines who can do what, and where, in your cloud environment. Whether you are an enterprise deploying critical applications or a small team experimenting with cloud services, understanding IAM is essential for cloud engineers to prevent misconfigurations, protect sensitive data, and maintain compliance.
Curiosity Tech emphasizes that IAM mastery goes beyond just “granting roles”; it’s about strategic access control, least privilege enforcement, and audit readiness. This guide covers IAM in extreme depth, with practical examples, hierarchical diagrams, tables, and best practices.
What is IAM in GCP?
IAM in GCP is a centralized system to manage access to all Google Cloud resources. It ensures that only authorized users, groups, or service accounts can perform specific actions on your cloud resources.
Core concepts:
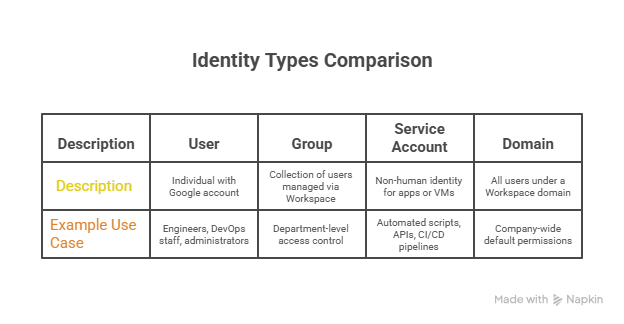
- Identity: User, group, service account, or domain that requires access.
- Roles: A collection of permissions that define what actions the identity can perform.
- Permissions: Individual actions, e.g., compute.instances.create or storage.buckets.delete.
IAM allows you to manage fine-grained access, which is critical for cloud governance, compliance, and risk reduction.
Types of Identities in GCP
Roles in GCP IAM
Roles define what actions identities can perform. GCP offers three main types of roles:
- Primitive Roles :-
- Owner: Full control over all resources.
- Editor: Modify resources but limited to management features.
- Viewer: Read-only access.
- Predefined Roles :-
- Fine-grained, specific to services like Compute Engine, Cloud Storage, or BigQuery.
- Example: roles/storage.objectAdmin allows full access to Cloud Storage objects without other service privileges.
- Custom Roles :-
- Created to meet unique business requirements.
- Combines specific permissions to enforce least privilege.
IAM Policy Structure
Key components:
IAM policies are JSON objects attached to resources, defining who has what access.
- bindings: Assign roles to members.
- members: Users, groups, or service accounts.
- roles: Predefined, primitive, or custom.
Example IAM policy snippet:
{
“bindings”: [
{
“role”: “roles/storage.objectViewer”,
“members”: [
“user:alice@example.com”,
“serviceAccount:my-app@project.iam.gserviceaccount.com”
]
}
]
}
This policy allows Alice and the service account to view Cloud Storage objects.
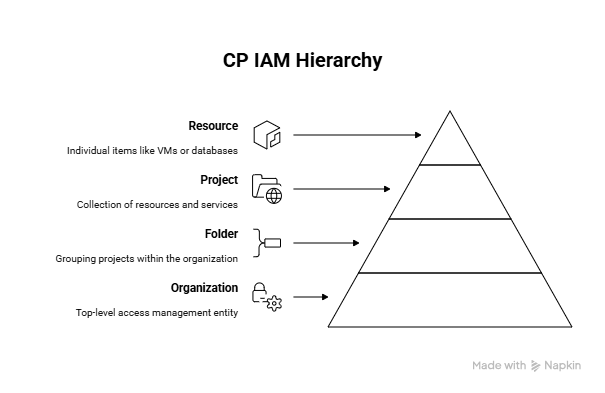
IAM Hierarchy
GCP IAM is hierarchical, meaning access can be inherited from parent resources.
Hierarchy Diagram (Infographic Concept):
Best Practices for IAM
- Follow the Principle of Least Privilege: Only grant permissions needed for a task.
- Use Groups and Service Accounts Wisely: Avoid assigning roles to individual users for easier management.
- Enable Audit Logging: Track who did what and when.
- Regularly Review Roles: Remove unnecessary permissions to reduce risk.
- Custom Roles Over Primitive Roles: Custom roles give precise control.
(Curiosity Tech guides engineers through hands-on labs to audit IAM policies and optimize access controls—crucial for real enterprise environments.)
Practical Example: Secure Deployment
Scenario: Deploying a web application in a secure GCP environment.
- Create service accounts for backend processes.
- Assign predefined roles like roles/compute.instanceAdmin only to service accounts that need them.
- Use groups for developers and ops teams to manage project-level permissions.
- Enable Cloud Audit Logs to monitor role usage and detect anomalies.
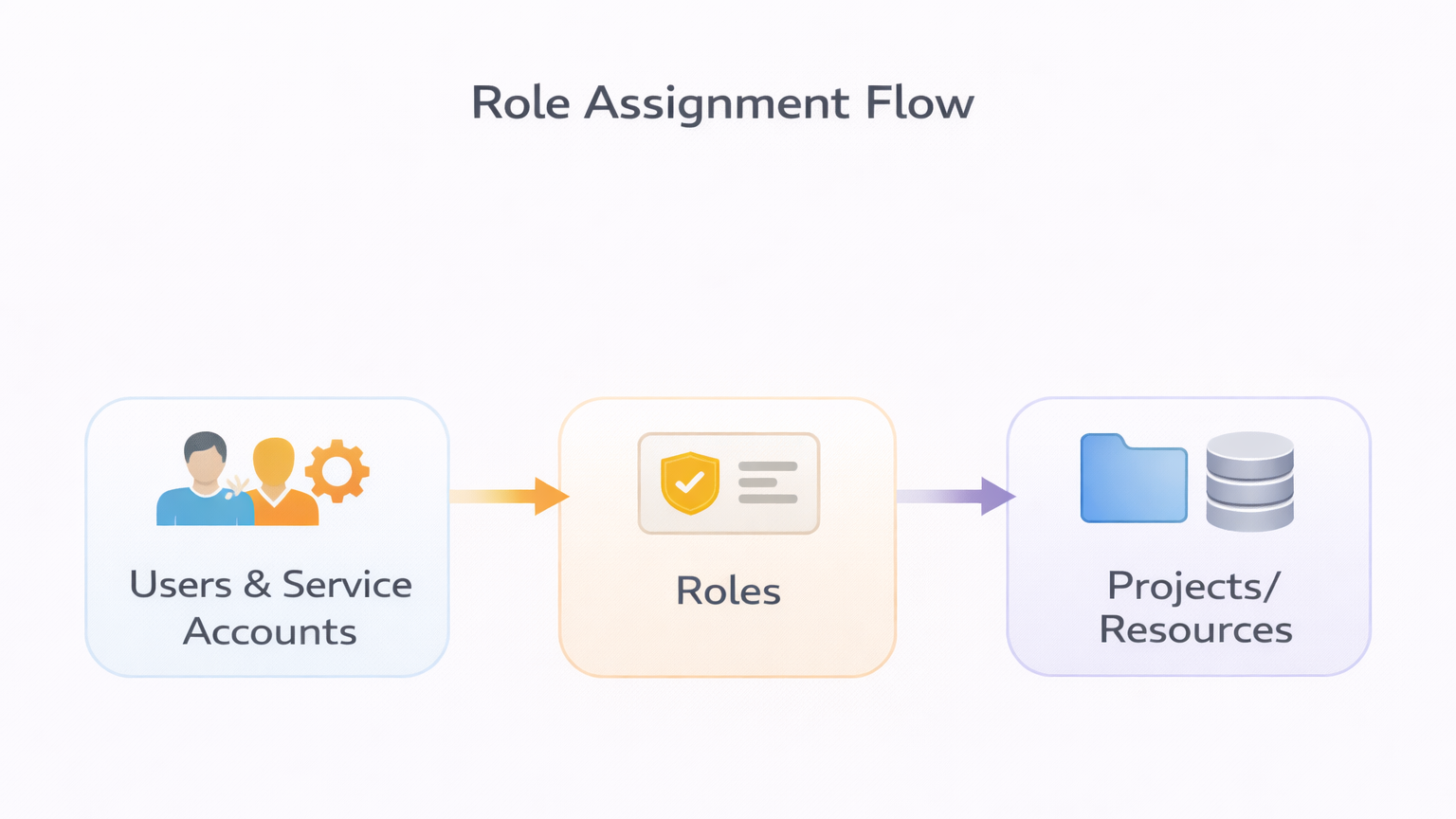
Diagram: Role Assignment Flow (Users & Service Accounts → Roles → Projects/Resources)
Advanced IAM Features
- Conditional Role Bindings: Grant access only if certain conditions are met (e.g., access only during business hours).
- Organization Policies: Enforce restrictions across all projects (e.g., disallow external IPs).
- IAM Recommender: Suggests rightsizing permissions to align with least privilege.
Becoming an expert involves hands-on experimentation, auditing existing IAM policies, and exploring conditional and custom roles. Real mastery comes when you can design secure, scalable, and compliant IAM architectures for multi-project environments.
Conclusion
IAM is the cornerstone of GCP security and governance. By mastering roles, permissions, and policy management, engineers can securely deploy, manage, and scale applications. Continuous learning, auditing, and strategic role assignment are keys to becoming a GCP IAM expert.
At Curiosity Tech, we focus on practical labs, real-world scenarios, and strategic insights so engineers can confidently manage permissions, design secure architectures, and prepare for GCP certifications.



