I still remember my first exposure to cryptography during an onsite project back in 2007. A global bank in Mumbai asked me to secure credit card transactions. At first, I thought firewalls and antivirus software were enough. But when I saw how modern attackers don’t just break into systems—they intercept or manipulate data in transit, I realized that cryptography is the invisible shield behind every secure digital transaction.
In 2025, without cryptography, concepts like online banking, e-commerce, cloud computing, or even WhatsApp messages would collapse overnight.
At CuriosityTech.in Nagpur, we train aspiring cyber engineers to not just know cryptography but to implement, visualize, and test it—because encryption and hashing form the backbone of cyber security.
What is Cryptography?
Cryptography is the practice of securing information by transforming it into unreadable form for unauthorized users while ensuring it can be retrieved by those authorized.
Security Goals Achieved by Cryptography (CIA+3)
- Confidentiality – Keep information secret (encryption).
- Integrity – Prevent unauthorized changes (hashing, signatures).
- Availability – Ensure legitimate access.
- Authentication – Proof of identity (digital certificates).
- Non-repudiation – Prevent denial of actions (digital signatures).
Encryption vs Hashing
| Aspect | Encryption | Hashing |
| Definition | Process of converting plaintext into ciphertext using a key; reversible with key. | One-way mathematical function producing fixed-length digest; irreversible. |
| Purpose | Protect confidentiality (e.g., secure emails, file storage). | Ensure integrity (verify files, passwords). |
| Reversibility | Reversible (with decryption key). | Irreversible. |
| Real-World Use | WhatsApp E2E encryption, SSL/TLS. | Password storage, file verification (e.g., SHA-256). |
Cryptographic Systems Overview
1. Symmetric Encryption (Shared Key)
- Same key for both encryption and decryption.
- Faster, suitable for bulk data.
- Example Algorithm: AES (Advanced Encryption Standard).
Equation Illustration:
If plaintext = P ; key = K
Encryption: C = EK(P)
Decryption: P=DK(C)
Real Example:- AES-256 encrypts files on your laptop (BitLocker, VeraCrypt).
2. Asymmetric Encryption (Public/Private Keys)
- Public key (shared) encrypts, private key (secret) decrypts.
- Slower but more secure for communication.
- Example Algorithms: RSA, ECC.
Equation Illustration:
- If plaintext = P ; public key = Kpub ; private key = Kpriv
C = EK pub(P) ; P = DK priv(C)
C = E
Kpub (P)
P=D
Kpriv (C)
Real Example: SSL/TLS certificates securing HTTPS websites.
3. Hashing (Integrity Checking)
- One-way mathematical function producing fixed digest.
- SHA-256 turns any input (no matter the size) into a 256-bit hash.
- Even a small change in input completely changes output (avalanche effect).
Hash Example:
- Input:- “CuriosityTech” → Hash: e3c8b74bb220cd9229de11aa…
- Input:- “Curiositytech” → Hash (completely different).
Used for :- protecting user passwords, validating file downloads, blockchain.
4. Digital Signatures & Certificates
- Combine asymmetric keys + hashing.
- Steps:
- Sender hashes message.
- Hash is encrypted with sender’s private key = signature.
- Receiver decrypts signature with sender’s public key & comapares with their own hash.
This ensures message authenticity + integrity + non-repudiation.
Visual Flow: Secure Messaging Example
Diagram Description :- A visual showing two users (Alice → Bob).
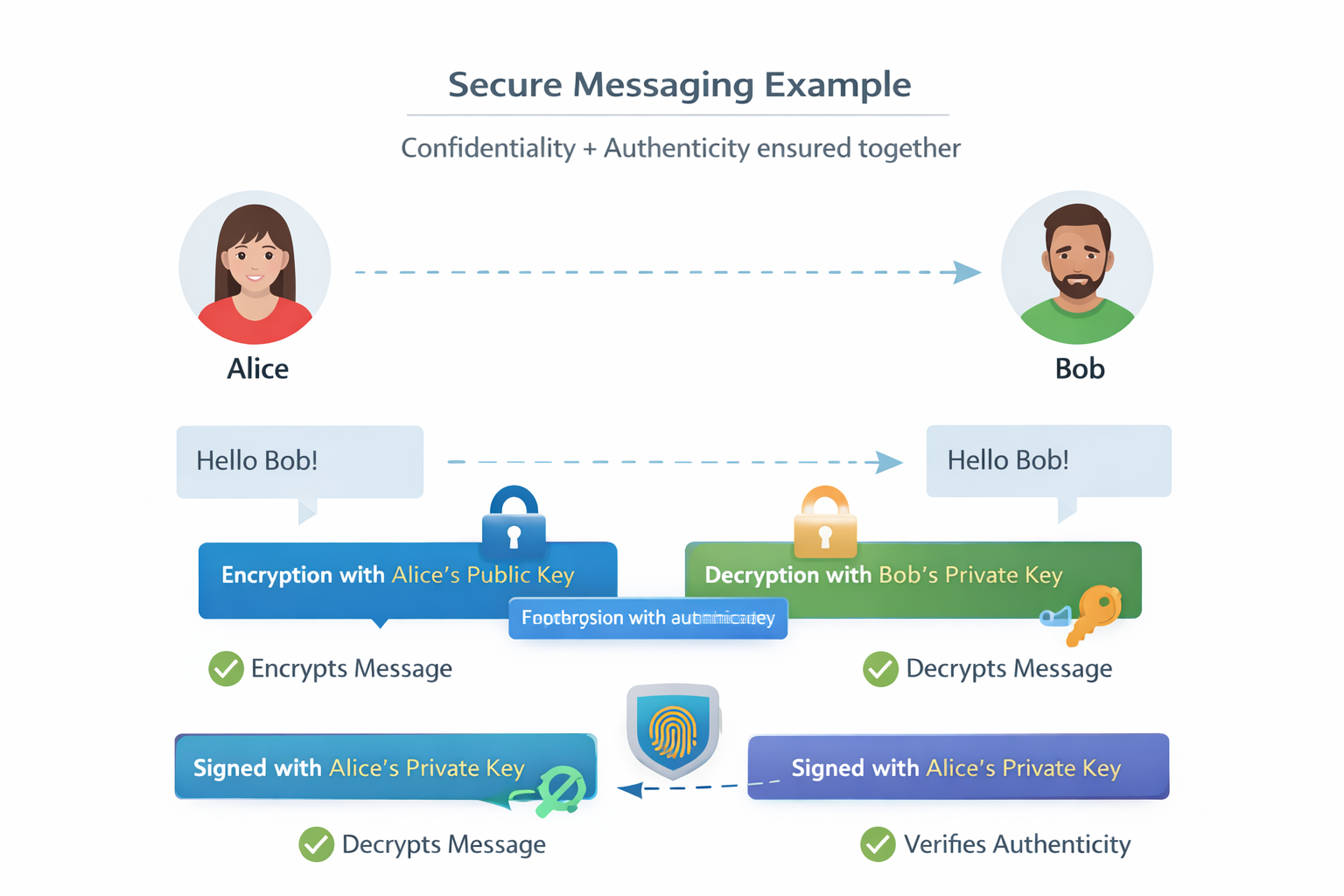
This diagram clearly explains how confidentiality + authenticity are ensured together.
Real-World Case Studies
Case 1 – WhatsApp End-to-End Encryption
- Protocol: Signal Protocol (Double Ratchet + AES-256 + Curve25519 ECC).
- Every message encrypted with a fresh key pair (forward secrecy). Protects against interception even by WhatsApp itself.
Case 2 – Ransomware Encryption Attacks
- Wannacry ransomware used AES for local file encryption + RSA to encrypt AES keys.
- Engineers learned an important lesson—the same algorithms that protect us can also be weaponized. Defense requires backups + key management.
Case 3 – Banking Transactions
- TLS 1.3 encrypts transactions on https://curiositytech.in or banking portals.
- Without TLS encryption, attackers could sniff credentials in plaintext (classic “Man-in-the-Middle” attack).
Practical Lab Guide for Beginners
At CuriosityTech Labs, I instruct students to build a cryptography playground:
- Use OpenSSL to encrypt a file with AES and then decrypt it
- Command :- openssl enc -aes-256-cbc -in file.enc -k secretkey.
- Decrypt :- openssl enc -aes-256-cbc -d -in file.enc -out file_dec.txt -k secretkey.
- Hash the same file with SHA-256.
- Command :- shs256sum file.txt
- Compare integrity after downloading—prove no tampering occurred.
Lab exercises like these transform cryptography from abstract math into lived experience.
Common Mistakes Engineers Make
- Using weak ciphers (MD5, DES, RC4 are obsolete in 2025).
- Poor key management (storing keys in plain text on same servers).
- Believing hashing = encryption (it does not provide confidentiality).
- Forgetting to apply nonce/IV (initialization vectors) for AES, which leads to predictable ciphertexts.
Personal Field Insight
In 2014, I reviewed a Nagpur law firm storing client contracts. They believed encrypting passwords in Excel files with simple XOR was “enough.” When attackers broke in, encryption was brute-forced in hours. We replaced their system with AES + centralized key vaulting. Since then, they’ve faced zero incidents.
Lesson? Cryptography is not about any protection. It’s about using the right algorithm with the right key management practices.
Conclusion
Cryptography is the hidden engine that makes modern cyber security work. Encryption delivers confidentiality, hashing assures integrity, and digital signatures ensure authenticity and non-repudiation. Mastering these essentials is non-negotiable for cyber security engineers in 2025.
At CuriosityTech.in (1st Floor, Plot No 81, Wardha Rd, Gajanan Nagar, Nagpur | Phone: +91-9860555369 | Email: contact@curiositytech.in | Instagram: curiositytechpark | LinkedIn/Facebook: Curiosity Tech), our mission is to transform cryptography from complex equations into practical security shields every engineer can use with confidence. Because encryption is not just math—it’s trust in the digital age.



