Executive Overview
Security is the number one reason why enterprises hesitate to fully embrace multi-cloud. Each provider—AWS, Azure, and GCP—offers robust security mechanisms, but once workloads are distributed, gaps appear: inconsistent IAM policies, fragmented logging, cross-cloud data exposure, and regulatory blind spots.
This blog, structured like a threat modeling guide, explores the security challenges unique to multi-cloud environments and provides solutions mapped to industry frameworks. At Curiosity Tech we transform these challenges into learning opportunities through labs where engineers simulate attacks and implement defenses across multiple clouds.
Part 1 – Threat Modeling in Multi-Cloud
When designing a secure architecture, we begin by identifying threats. Below is a simplified STRIDE threat model applied to multi-cloud:
| Threat Category | Multi-Cloud Example | Potential Impact |
| Spoofing | Compromised API key reused across AWS & Azure | Unauthorized access |
| Tampering | Altered logs during cross-cloud transfer | Loss of audit integrity |
| Repudiation | No unified logging; attacker denies activity | Compliance failure |
| Information Disclosure | Data in transit between AWS & GCP not encrypted | Data breach |
| Denial of Service | Coordinated DDoS hitting Azure & AWS simultaneously | Service outage |
| Elevation of Privilege | Misconfigured IAM roles across providers | Root-level access |
Part 2 – Security Challenges in Multi-Cloud
1. Identity & Access Management Drift
- Each cloud uses different IAM paradigms.
- Risk: Inconsistent role enforcement → privilege escalation.
2. Network Exposure Across Clouds
- Inter-cloud peering or VPN misconfiguration exposes attack surfaces.
3. Data Protection & Sovereignty
- Data replication across regions may violate GDPR, HIPAA, or RBI guidelines.
4. Fragmented Monitoring
- Logs scattered across CloudWatch, Azure Monitor, and GCP Logging → blind spots
5. Shadow IT & Unmanaged Services
- Teams spin up resources in one cloud without enterprise-wide governance.
Part 3 – Security Solutions & Frameworks
1. Identity & Access Management (IAM)
- Use federated identity (SAML, OIDC) across AWS, Azure, and GCP.
- Enforce least privilege using attribute-based access control (ABAC).
- Rotate keys and prefer short-lived tokens.
2. Zero Trust Networking
- Replace perimeter defense with context-aware policies.
- Example: Only allow traffic from verified workloads, regardless of cloud.
3. Encryption & Data Security
- Encrypt in transit with TLS 1.3, at rest with KMS (AWS), Key Vault (Azure), CMEK (GCP).
- Centralize keys with HSM-backed multi-cloud vaults.
4. Unified Monitoring & SIEM
- Export all logs to a central SIEM (Splunk, Elastic SIEM, Sentinel).
- Correlate events across providers for end-to-end detection.
5. Compliance & Governance
- Map frameworks like NIST CSF, ISO 27001, GDPR, HIPAA.
- Use Cloud Security Posture Management (CSPM) tools (Prisma Cloud, Wiz).
Diagram
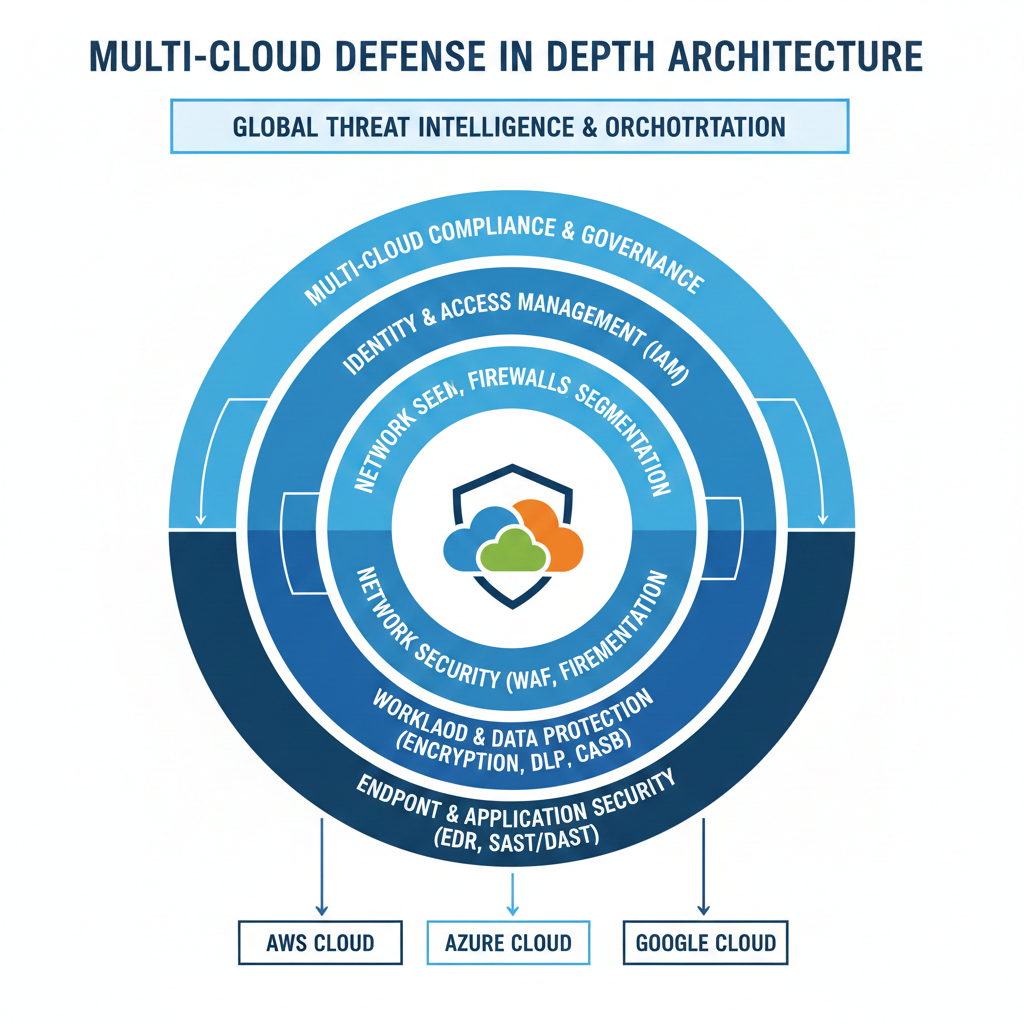
This layered architecture illustrates defense in depth for multi-cloud security.
Part 4 – Mapping Security Challenges to Solutions

Part 5 – Example Attack & Defense Simulation
Scenario: An attacker gains access to an exposed API key from an AWS developer account.
- Without unified IAM → attacker reuses the same identity to access Azure workloads
- Logs in AWS CloudTrail and Azure Monitor are separate → delayed detection.
Defense:
- Use federated identity + centralized logging.
- Alert triggers when API requests originate from suspicious IPs across clouds.
- Automated playbooks revoke compromised credentials within minutes.
At Curiosity Tech, labs replicate this scenario so learners see how quickly an attacker can pivot in multi-cloud and how defensive automation reduces breach windows.
Part 6 – Skills Roadmap for Multi-Cloud Security Experts
- Learn Cloud-Native Security Tools → IAM, VPC firewalls, KMS.
- Study Compliance Frameworks → ISO, GDPR, HIPAA.
- Practice Threat Hunting → Logs across AWS, Azure, GCP.
- Master Automation → Terraform + security modules.
- Contribute to FinOps + SecOps integration → cost + security governance.
This path is core to Curiosity Tech cloud security specialization program, where learners don’t just memorize concepts but simulate red team and blue team activities.
Conclusion
Multi-cloud introduces new attack surfaces and operational risks, but with structured threat modeling and layered defense frameworks, enterprises can transform these risks into strengths. The future is zero trust, automated defense, and compliance-first architecture.
Security engineers who rise to the multi-cloud challenge will not just protect workloads—they will enable businesses to innovate with confidence. At Curiosity Tech, we believe that security isn’t just a barrier; it is an accelerator of trust and adoption in the cloud era.