Introduction
Securing Industrial IoT (IIoT) is a critical requirement in 2025 due to the increasing sophistication of cyber threats and the physical risks posed by breaches in manufacturing environments. Unlike traditional IT, IIoT systems control physical machinery, infrastructure, and sensitive operations where failures can cost millions or endanger lives.
This comprehensive guide outlines layered security best practices, threat models, compliance standards, and proactive measures required for robust IIoT security, pulled from recent expert industry reports and emerging 2025 trends.
Unique IIoT Security Challenges
- Legacy Equipment Vulnerabilities: Many industrial setups use decades-old equipment not designed for cybersecurity.
- Real-Time Constraints: IIoT’s deterministic operational needs limit traditional security tools that induce latency.
- Physical Exposure: Devices often located in unsecured, remote, or harsh environments vulnerable to tampering.
- Heterogeneity: Mixed vendor devices and protocols complicate unified security.
- Scale & Complexity: Thousands of devices distributed across multiple zones or factories require consistent enforcement.
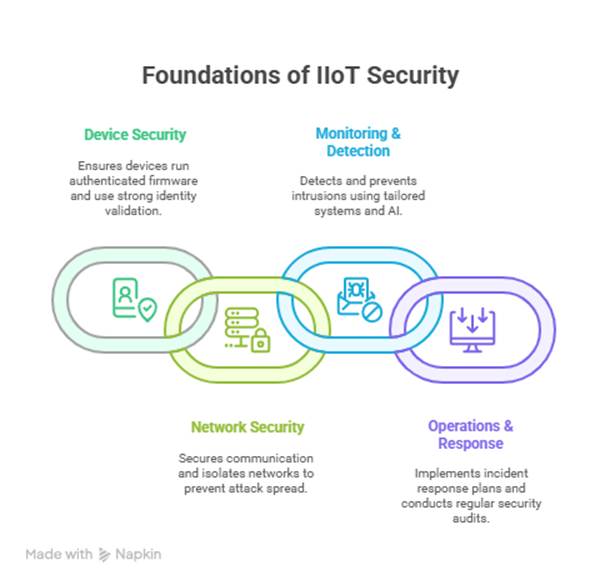
Core Pillars of IIoT Security
- Device Security
- Secure Boot & Hardware Root of Trust: Ensures devices only run authenticated firmware preventing tampering.
- Certificate-Based Authentication: Each device uses unique X.509 certificates for strong identity validation.Firmware Integrity & OTA Updates: Cryptographically signed updates distributed securely and regularly.
- Trusted Platform Modules (TPMs): Hardware security modules store keys and certificates, protecting device integrity.
- Network Security
- Encrypted and Authenticated Communication: Use TLS-encrypted MQTT, OPC UA over TLS, HTTPS.
- Replace/Wrap Legacy Protocols: Upgrade legacy Modbus or proprietary protocols with secure ones or employ protocol gateways.
- Network Segmentation & Isolation: Purdue model implementation isolates OT networks from IT to prevent lateral attack spread.
- Secure Gateways: IoT edge gateways act as controlled DMZs, mediating device-cloud communications.
- Monitoring & Detection
- Intrusion Detection & Prevention Systems (IDS/IPS) tailored for OT environments.
- Security Information and Event Management (SIEM) that ingests IIoT device logs alongside IT security feeds.
- Passive Network Monitoring to minimize disruption with active threat hunting.
- AI-driven Behavioral Anomaly Detection to spot unusual traffic patterns or device behavior.
- Operations & Response
- Incident Response Plan customized for IIoT, including procedures for immediate production line shutdown or isolation.
- Regular Security Audits and Penetration Testing focusing on protocols, APIs, and operational vulnerabilities.
- Comprehensive Device Inventory with automatic discovery and compliance checks.
- Security Training and Awareness programs for all stakeholders — operators, engineers, management.
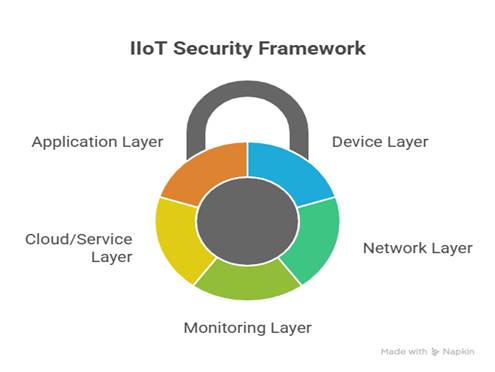
Layered IIoT Security Architecture (Conceptual Overview)
| Layer | Security Controls |
| Device Layer | Secure boot, TPM, cryptographic identity, firmware signing |
| Network Layer | Encryption (TLS, IPSec), segmentation, secure gateways |
| Monitoring Layer | IDS/IPS, AI detection, SIEM integration |
| Cloud/Service Layer | Identity & access management, anomaly detection, audit logging |
| Application Layer | Role-based access, MFA, API security |
This architecture supports a defense-in-depth strategy crucial for mitigating IIoT risks[^].
Best Practices Checklist for IIoT Security in 2025
- Implement secure boot to prevent execution of malicious firmware.
- Enforce mutual TLS authentication between devices and cloud.
- Rotate cryptographic keys regularly and automate certificate renewal.
- Use network segmentation to separate OT and IT networks with DMZ zones.
- Replace insecure legacy protocols with secured OLE for Process Control (OPC) UA over TLS.
- Enable continuous monitoring using AI-powered anomaly detection tools.
- Conduct regular penetration testing focused on IIoT vulnerabilities.
- Establish detailed device inventory and asset management for visibility.
- Provide cybersecurity training to operational staff with focus on IIoT threats.
- Develop and practice an incident response plan including industrial-specific scenarios.
Real-World Examples
- Many manufacturing plants block ransomware attacks by segmenting and isolating their OT networks.
- Leading automotive manufacturers deploy TPM-backed devices to secure their robotic arms and actuators.
- Facilities report significant threat reduction after implementing AI-driven SIEM platforms that integrate IIoT logs with IT data[^][^].
Compliance and Standards to Follow
- IEC 62443: Industrial automation and control system security standard is the gold standard worldwide.
- NIST Cybersecurity Framework: Provides guidelines for risk management in Critical Infrastructure.
- FDA & HIPAA: For healthcare IoT devices, data confidentiality and integrity are mandatory.
- ISO 27001: General information security management systems standard applying to cloud and on-premise IoT deployments.
Challenges Ahead
- Legacy equipment retrofit challenges.
- Balancing real-time operational constraints with security overheads.
- Managing heterogeneous multi-vendor environments securely.
- Scaling automated security processes across thousands of devices.
CuriosityTech IoT Security Labs
CuriosityTech.in Nagpur integrates IIoT security into all coursework:
- Hands-on labs for configuring secure MQTT brokers with TLS and certificate authority (CA).
- Simulated attacks including MQTT flooding and firmware tampering to train rapid response.
- Network segmentation exercises using firewalls and VLANs.
- Real-time SIEM dashboards analyzing OT device logs, drawing actionable alerts via AI.
Conclusion
IIoT security demands a multi-layered, proactive approach combining hardware-root trust, encryption, segmentation, monitoring, and compliant operational practices. With the stakes high in manufacturing—safety, downtime, reputation—security can never be an afterthought.
Achieving this security maturity requires continuous investment and training. Organizations like CuriosityTech.in Nagpur prepare IoT engineers not only to build connected factories but to defend them against evolving cyber risks with comprehensive, practical capabilities.