Introduction
On Day 19, we focus on security best practices for PHP Full Stack Development. Security is a critical aspect of web applications because vulnerabilities can compromise data, users, and business credibility.
At CuriosityTech.in, learners implement secure coding practices, data validation, authentication, and encryption to build applications that are safe for production use.
1. Common PHP Security Vulnerabilities
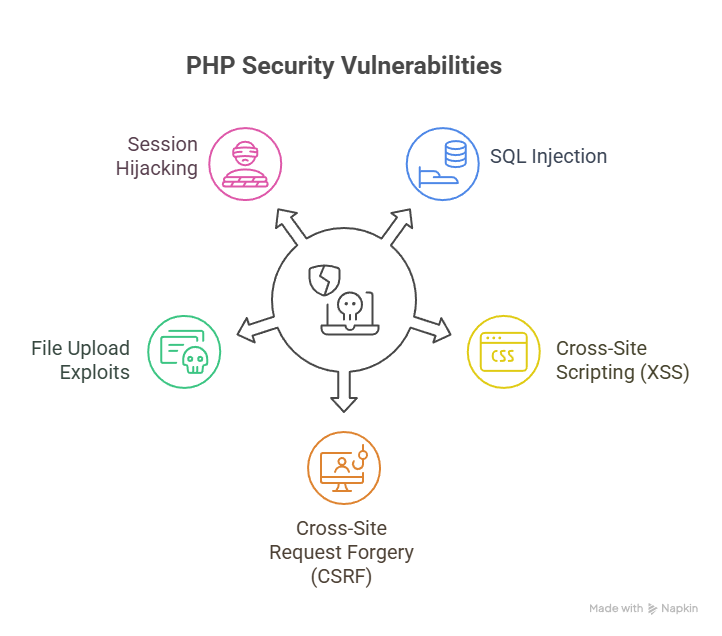
2. Input Validation & Sanitization
Core PHP Example:
$email = filter_input(INPUT_POST, ’email’, FILTER_SANITIZE_EMAIL);
$password = htmlspecialchars($_POST[‘password’], ENT_QUOTES, ‘UTF-8’);
- filter_input() ensures proper data type
- htmlspecialchars() prevents XSS by escaping HTML characters
Laravel Example:
$request->validate([
’email’ => ‘required|email’,
‘password’ => ‘required|min:8’
]);
Laravel automatically handles XSS protection in Blade templates using {{ $variable }}.
3. Prepared Statements & ORM
Core PHP (PDO) Example:
$stmt = $pdo->prepare(“SELECT * FROM users WHERE email = :email”);
$stmt->execute([’email’ => $email]);
$user = $stmt->fetch();
Laravel Eloquent Example:
$user = User::where(’email’, $email)->first();
Using prepared statements or Eloquent ORM prevents SQL injection attacks.
4. Password Security
- Always hash passwords before storing:
// Core PHP
$passwordHash = password_hash($password, PASSWORD_BCRYPT);
// Laravel
User::create([
‘name’ => $name,
’email’ => $email,
‘password’ => bcrypt($password)
]);
- Verify passwords using password_verify() in PHP or Hash::check() in Laravel
5. CSRF Protection
Laravel: Automatically includes CSRF tokens in forms:
<form method=”POST” action=”/submit”>
@csrf
<input type=”text” name=”name”>
<button type=”submit”>Submit</button>
</form>
Core PHP Example: Generate CSRF token manually:
session_start();
if (empty($_SESSION[‘csrf_token’])) {
$_SESSION[‘csrf_token’] = bin2hex(random_bytes(32));
}
6. Session Security
- Use secure, HTTP-only cookies
- Regenerate session IDs after login:- session_regenerate_id(true);
- Store sensitive session data securely
7. File Upload Security
- Restrict file types and size
- Store files outside the webroot
- Rename files to avoid conflicts
- Scan files for malware
Laravel Example:
$request->validate([
‘file’ => ‘required|mimes:jpg,jpeg,png,pdf|max:5120’,
]);
$path = $request->file(‘file’)->store(‘uploads’, ‘public’);
8. HTTPS & Data Encryption
- Always use SSL certificates to encrypt data in transit
- Encrypt sensitive data in the database if necessary
- Use Laravel’s encrypt() and decrypt() helpers
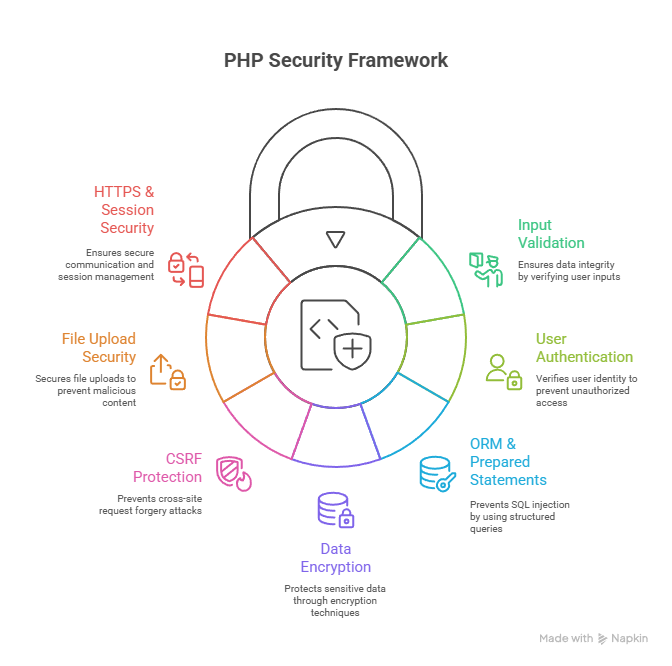
9. Hierarchical Diagram: PHP Security Workflow
10. CuriosityTech.in Perspective
At CuriosityTech.in, learners integrate security best practices into their PHP and Laravel projects, ensuring applications are robust, reliable, and production-ready.
Hands-on exercises include:
- Preventing SQL Injection and XSS
- Secure authentication and session management
- Safe file upload and storage
- Using HTTPS for secure communication
By mastering these practices, developers build trustworthy web applications ready for real-world deployment.
11. Infographic Concept: Security Best Practices for PHP
- Input validation & sanitization
- Password hashing & authentication
- CSRF & XSS protection
- Secure session handling
- Safe file uploads
- HTTPS & encryption
Conclusion
Security is a critical pillar of full-stack development. Today’s lesson equips developers to protect their PHP and Laravel applications from common vulnerabilities, ensuring that their projects are safe, scalable, and production-ready. Mastery of security prepares developers for real-world projects like online stores and dashboards (Day 20).