Networking forms the backbone of any cloud infrastructure. On Day 8, we explore AWS Virtual Private Cloud (VPC), subnets, route tables, and security groups—the core components that define how resources communicate and remain secure.
At Curiosity Tech, we emphasize that mastering networking is crucial for cloud engineers. Misconfigured networks can lead to downtime, security breaches, and performance bottlenecks. Beginners who understand VPC design from the start are well-prepared to architect scalable and secure cloud environments.
1. What is an AWS VPC?
A Virtual Private Cloud (VPC) is a logically isolated section of AWS where you launch resources like EC2 instances, RDS databases, and Lambda functions. Think of a VPC as a private network in the cloud, similar to your company’s on-premise data center, but scalable, flexible, and fully controlled.
Key Features:
- Logical isolation of resources
- Control over IP address ranges
- Integration with subnets, route tables, and gateways
- Enhanced security and access control
Analogy: Imagine your VPC as a walled city in the cloud. Subnets are neighborhoods, route tables are the roads, and security groups are checkpoints at every entrance.
2. Core Networking Components
| Component | Description | Example |
| VPC | Logical isolated network | vpc-curiositytech |
| Subnet | Smaller segment of VPC for resource placement | Public Subnet: 10.0.1.0/24 |
| Route Table | Rules for traffic routing | Direct internet traffic from public subnet |
| Internet Gateway (IGW) | Connects VPC to the Internet | Enable public EC2 access |
| NAT Gateway | Allows private instances to access the Internet | Software updates from private subnet |
| Security Group | Virtual firewall for instances | Allow SSH from admin IP only |
Expert Tip: Beginners often confuse security groups with network ACLs. Remember: security groups are instance-level, stateful firewalls, while ACLs are subnet-level, stateless filters.
3. Understanding Subnets
Subnets divide a VPC into smaller IP ranges, allowing for better organization and security:
- Public Subnets: Accessible from the Internet (e.g., web servers)
- Private Subnets: No direct Internet access (e.g., databases, backend apps)
- Subnet CIDR Range: Defines the number of IP addresses available
Hierarchical Diagram Concept:
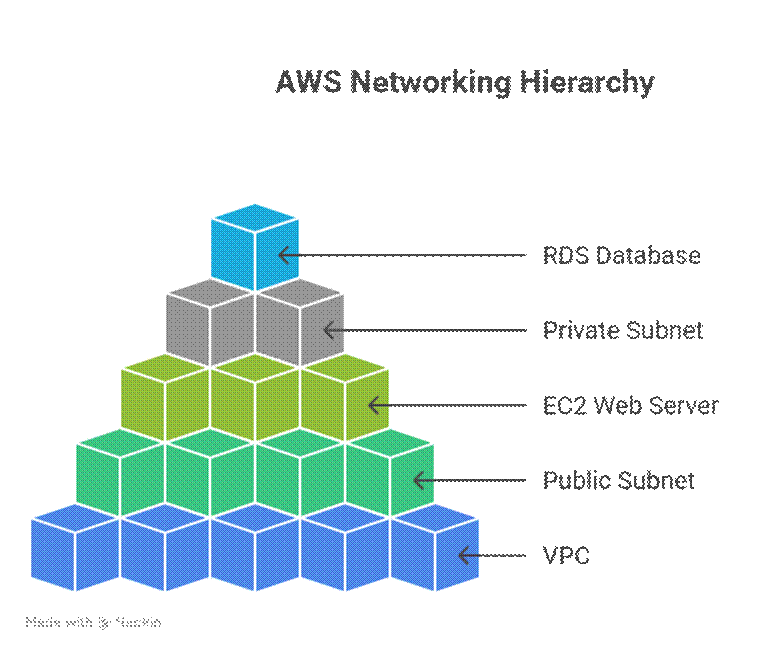
This shows how public-facing and internal resources are isolated, improving both security and traffic management.
4. Security Groups Explained
Security groups act as virtual firewalls that control inbound and outbound traffic for your instances.
| Feature | Description | Example |
| Stateful | Return traffic is automatically allowed | SSH request allowed, response flows back |
| Inbound Rules | Specify allowed incoming traffic | Port 22 from admin IP |
| Outbound Rules | Specify allowed outgoing traffic | Allow HTTP traffic to Internet |
| Instance-level | Applied directly to EC2, RDS, Lambda | Each EC2 instance can have multiple SGs |
Expert Tip: Always start with restrictive rules (deny all by default) and open only required ports.
5. Step-by-Step: Create a Simple VPC with Public and Private Subnets
1 – Create VPC
- Navigate to VPC Dashboard → Create VPC
- CIDR block: 10.0.0.0/16
2 – Create Subnets
- Public Subnet: 10.0.1.0/24
- Private Subnet: 10.0.2.0/24
3 – Configure Internet Gateway
- Create IGW → Attach to VPC
- Update route table for public subnet → IGW
4 – Launch EC2 Instances
- Public subnet → Web server (access via SSH)
- Private subnet → Database server (no direct Internet access)
5 – Configure Security Groups
- Public EC2 → SSH from your IP, HTTP for web traffic
- Private EC2 → Allow only internal VPC traffic
Curiosity Tech Insight: Beginners often forget routing rules. Our labs focus on testing connectivity and verifying security rules, which is crucial for real-world deployments.
6. Infographic Concept
Visual Idea:
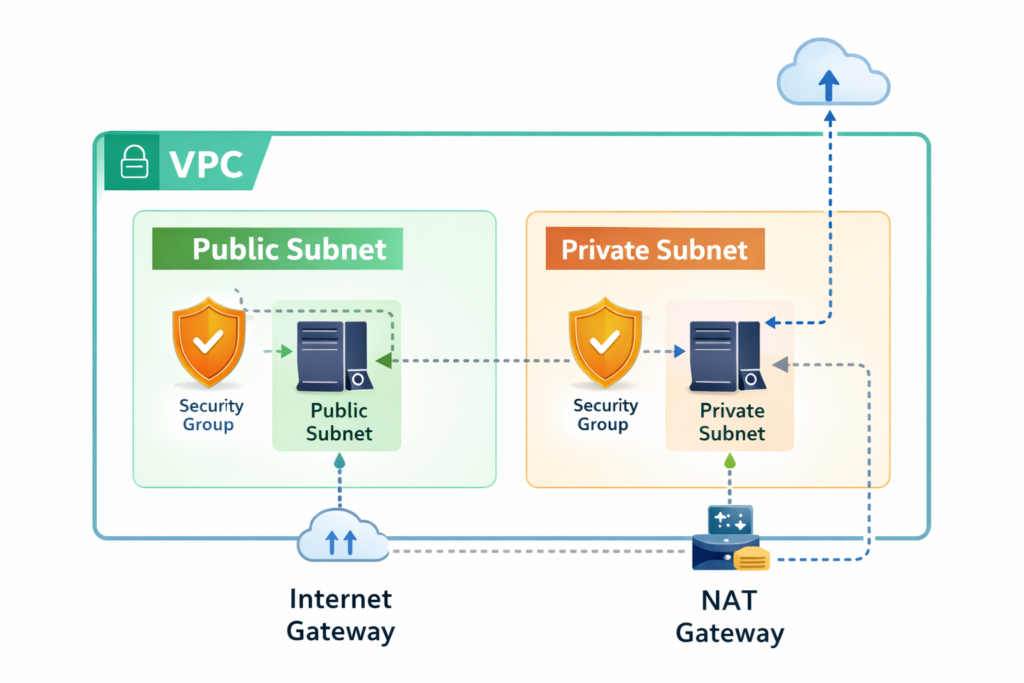
7. Common Beginner Mistakes
- Launching private instances without NAT → No software updates
- Open security groups to 0.0.0.0/0 → Security risk
- Ignoring subnet IP ranges → Insufficient IP addresses
- Misconfigured route tables → Inaccessible instances
Expert Tip: Use AWS VPC Flow Logs to monitor traffic and troubleshoot connectivity issues.
8. Path to Expertise
- Start with default VPCs, explore subnets and route tables
- Launch simple EC2 instances in public/private subnets.
- Experiment with security groups, NACLs, and NAT gateways.
- Advance to multi-tier architectures with VPC peering.
- Integrate CloudWatch and CloudTrail to monitor network activity.
At Curiosity Tech, learners progress from single VPC setups to multi-VPC, multi-region networks, gaining confidence in secure and scalable network design.
Conclusion
AWS networking is the foundation of secure, scalable cloud architecture. Mastering VPCs, subnets, route tables, and security groups equips cloud engineers to design robust infrastructures.
Hands-on practice, combined with mentorship and real-world lab simulations at Curiosity Tech, ensures learners not only understand concepts but can implement production-ready networks